SHA-1 is on the verge of breathing its last. But someone needs to notify the next of kin, because new research from Venafi® Labs shows that 1 in 5 of the world’s websites are still using certificates signed with the vulnerable secure hash algorithm, SHA-1. It’s not like these organizations didn’t know SHA-1 was a problem. All major browsers are currently issuing security warnings to visitors who access sites using insecure SHA-1 certificates.
If you have been living in a cave for the past several years, you may not have heard that SHA-1 is deprecated. But SHA-1 is worse than vulnerable. Recent collision attacks have proven that SHA-1 is officially broken. That makes it even more puzzling to learn that ANY sites rely on SHA-1, let alone a substantial percentage. Yet, it appears that 21% of websites are still using the exploitable SHA-1 hashing algorithm, according to Venafi Labs research on over 33 million publicly visible IPv4 websites.
SHA-1 collisions should have taken no one by surprise. It was only a matter of time until computing power caught up with the SHA-1 algorithm. Cryptoanalysts began warning of SHA-1 vulnerability in 2005. But it wasn’t until February of 2017 that we had definitive proof when researchers from Google and leading universities demonstrated that the deprecated cryptographic secure hash algorithm still used to sign many website digital certificates can be manipulated.

SSL/TLS Certificates and Their Prevalence on the Dark Web
Fixing this problem seems to be relatively straightforward. Organizations can immediately reduce vulnerability by rotating out old SHA-1 certificates and replacing them with newly issued certificates that use SHA-2. But if it’s so straightforward, why are so many organizations still using SHA-1? It’s a good question. I think it’s safe to assume that no organization would intentionally leave itself open to security breaches, compliance problems, and outages that can affect security, availability, reliability. So, the explanation must be less obvious.
I suspect that many organizations may simply be unware that they still have any SHA-1 certificates on their networks because they are relying on certificate authority (CA) tools to manage their keys and certificates. The problem with this approach, especially now that free and very low cost certificates are widely available, is that anyone in your organization can get and install a certificate that uses weak hashing algorithms and install it on your network.
Kevin Bocek, Venafi VP of security strategy, outlines why he thinks many organizations are lagging, “Even though most organizations have worked hard to migrate away from SHA-1, they don’t have the visibility and automation necessary to complete the transition. We’ve seen this problem before when organizations had a difficult time making coordinated changes to keys and certificates in response to Heartbleed, and unfortunately I’m sure we are going to see it again.”
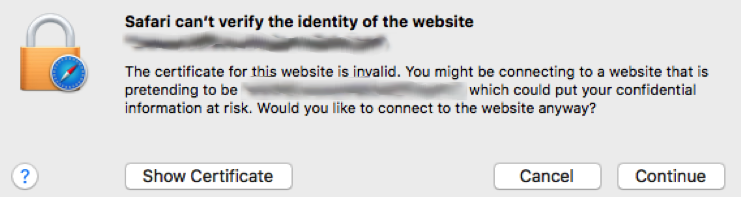
Beyond the clear security risks, SHA-1 can also interfere with web interactions and traffic in several ways:
- Insecure Site Warnings: Browsers will alert users that the site is unsafe, leading them to seek alternative websites.
- Lack of HTTPS Indicators: The 'green padlock' symbol, which signifies secure and private online transactions, will not appear in the address bar for HTTPS transactions. Consumers depend on this icon for assurance.
- Performance and Accessibility Issues: Websites might suffer from performance degradation, and in some instances, users may be entirely blocked from accessing the site.
Do you know if your website’s users are seeing any browser warnings like those listed below?