Here we are at the final post in the Managing Machine Identities in Hybrid Clouds blog series. Now it’s time to wrap up the issues I discussed in the first 5 bogs in this series: the growth of hybrid cloud in enterprises, the challenges of protecting machine identities, the risks you’ll need to overcome, why you should consider a cloud agnostic security strategy and which policies you’ll need to enforce consistent security for machine identities across your hybrid cloud environment.
Machine identities are at the heart of digital transformation. Cloud computing, microservices, API-enabled integration and DevOps, all require machine identities to place trust on the online communications. When it comes to certificate and keys management, there are many misconceptions, such as that certificate management services offered by cloud service providers (CSPs) can cover all aspects of certificate management. On top of that, “security in the cloud” is the sole responsibility of the customer and not of the cloud services provider.
To mitigate above issues, businesses need to develop and maintain a concise security policy which should be cloud agnostic, unique for both on-premises and in the cloud. This policy should be based on certificate management best practices identified by NIST SP 1800-16 and tailored to the needs of each specific business.

Tale of 3 Clouds eBook: How Venafi Creates Digital Transformation
Challenges of certificate management for DevOps
Even though machine identities are critical to the security of both internet-facing and private web services, many organizations do not have the ability to centrally monitor and manage their certificates, no matter where they are being deployed. This lack of a central certificate management service puts the organization at risk because once certificates are deployed, they require regular monitoring and maintenance. Organizations that improperly manage their certificates risk system outages and security breaches, which can result in revenue loss, harm to reputation, and exposure of confidential data to attackers.
With the advent of virtualization and the proliferation of cloud computing and containerization, the DevOps teams provision systems and software through programmatic means. This introduces new certificate challenges for organizations. As organizations push for more rapid and efficient deployment of business applications, many DevOps teams deploy certificates without coordination with the Certificate Services team. This can result in certificates for mission-critical applications not being tracked. This can be particularly problematic if bugs in DevOps programs/scripts cause certificates to be improperly deployed or updated. In addition, as DevOps teams adopt newer frameworks and tools, it is important to continue to monitor certificates and applications deployed and maintained by older DevOps frameworks and tools.
Therefore, the enterprise-wide security policy should solve certificate management problems that fall into these categories:
- Discovery: Discovery is a must-have. You need to know what you have, and whether it complies with your policies.
- Issuance: You must know what is issued, and if it has been issued according to the corporate security policy. The policy should apply controls to the who/what/when/how of issuing certificates.
- Monitoring: Monitoring is of essence when it comes to hybrid cloud environments. For external and third-party systems that can’t be controlled, how can your organization monitor and understand what exists?
- Provisioning and Automation: You need to get control over your environment. Automation and provisioning will eliminate mistakes made with manual process and reliance on humans making the right decision at the right time.
- Authentication: In order to discover, provision and monitor your systems across the enterprise, cloud authentication to your end-systems is a requirement.
When implementing in the cloud, these challenges are the exact same ones that are faced when managing machine identities on-premise. The difference is that some of the technologies needed to solve these challenges differ from on-premise.
One policy to manage machine identities across all platforms
Since the certificate management challenges faced in cloud environments are the exact same as the ones faced on-premise, it makes perfect sense to have one certificate management policy across all platforms.
Cloud services need to afford the same level of policy, control and visibility as the on-premise delivered. You can’t just rely on the services offered by the certificate management tools built in the cloud platforms. These tools are very good and easy at provisioning certificates for the development teams, but when it comes to policy compliance there are many gaps that may jeopardize your certificate management strategy.
Furthermore, it is not a good idea to get locked into a single cloud vendor. Cloud computing has revolutionized the ways that companies do business. However, this increased reliance on cloud computing also comes with the risk of dependency. By making your company more flexible and adaptable, being cloud agnostic inoculates against the risk of vendor lock-in. By standardizing on a toolchain and services in a multi-cloud environment, organizations can minimize the long-term operational and architectural debt. Standardized toolchains encourage cross-cloud architects and engineers by using the same languages and tools across clouds. While the APIs will continue to be unique, using the same scripting language and tools to manage and monitor them can dramatically reduce costs. Your applications need to be cloud-agnostic so you can get the most out of cloud computing. Your certificate management strategy needs to be cloud-agnostic too. Hence, a single platform can help you achieve cloud mobility and consistency with your policy.
Finally, if your well-tested and implemented on-premise policies, methodology, controls and visibility are a success, why should you change them? Successful best practices for your on-premise certificates, will still be successful when you extend them in the cloud.
The goal of your consistent certificate management policy across all platforms should be to deliver and manage certificates when and where it is needed, to provide a Certificates-as-a-Service solution. This is a best practice described in NIST SP 1800-16 publication (emphasis added): “The most efficient and effective approach is for the Certificate Services team to provide a central Certificate Service that includes technology-based solutions that provide automation and that support certificate owners in effectively managing their certificates. This service should include the technology/services for CAs, certificate discovery, inventory management, reporting, monitoring, enrollment, installation, renewal, revocation, and other certificate management operations. The central Certificate Service should also provide self-service access for certificate owners, so they are able to configure and operate the services for their areas without requiring significant interaction with the Certificate Services team. Furthermore, the central Certificate Service should be able to integrate with other enterprise systems, including identity and access management systems, ticketing systems, configuration management databases, email, workflow, and logging and auditing.”
A central, technology-based certificate management solution is also ideal to serve the increasing needs for machine identities in a DevOps environment and solve this problem: “The root of the problem is twofold: we're protecting the wrong things, and we're hurting productivity in the process.”
By “shifting left” security in the CI/CD pipeline we can find and prevent defects early in the development process, reduce failure rates and integrate encryption and authentication testing. The overall goal of “shift-left” security is to identify and resolve potential vulnerabilities earlier in the development life cycle, when these issues are less expensive to fix. Doing so will help to mitigate the risk potential security concerns pose to both the delivery schedule and your end -users. On the other hand, “shifting right” security, although not a novel notion, can help the Certificate Services team move services and tools closer to the end-user, thereby providing machines identities when and where they are needed.

Machine Identity Security Architecture
What are the benefits of a “cloud agnostic” approach?
“Agnostic” in the IT context means to be interoperable and it can refer to either software, hardware or even business practices. Thinking on the same lines, “cloud agnostic” means moving from one cloud to another without much impact to the IT systems and business processes.
One of the greatest benefits of cloud computing is its flexibility. Being “cloud agnostic” takes this idea of the flexible cloud one step further. Cloud agnostic service platforms provide the required consistent and standard performance in every environment, so that data can be portable, and the organization can take full advantage of the services offered by each cloud service provider without any interoperability disruptions.
Further, using a strategy that’s cloud agnostic and multi-cloud lets you tweak and adjust your cloud roadmap exactly as you see fit. You don’t have to miss out on a feature that’s exclusive to a single provider just because you’re locked into a different solution.
In addition, with a single, standardized management interface, operations could monitor and report on each distinct workload, no matter where it is. For a multi-cloud environment, operations must aggregate information feeds from heterogeneous systems, often with a need to normalize the data and apply additional analysis before the administrators can make optimizations or resolve problems.
Standardizing on a cloud-agnostic service platform can also alleviate costs associated with policy design, deployment, and enforcement across cloud environments. Management and monitoring using the same service platform greatly reduces the issue of mismatched security policies and uncertainty in enforcement. A cloud-agnostic service platform that also operates in the context of the data center—whether in a cloud, virtualized, container, or traditional infrastructure—is a benefit for organizations who need to move quickly. Being able to reuse policies and services across the entire multi-cloud spectrum reduces friction in the deployment process and offers assurances in consistency of performance and security.
Finally, cloud-agnostic service platforms will be increasingly important to organizations adopting a multi-cloud strategy. Not only can the traditional benefits of standardization be realized when familiar services are deployed across multiple clouds, but applications and the business will benefit from the ability to better realize consistent performance and security in every environment.
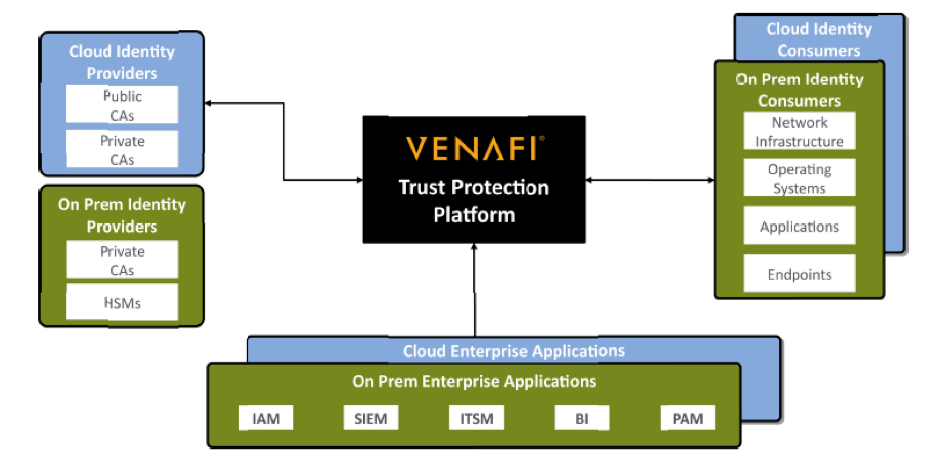
Keys for successful machine identity management policies
When it comes to managing and protecting machine identities in hybrid cloud environment, the following considerations are keys for a successful policy and strategy:
- There is no “one cloud:” Machine identity management needs to work across hybrid cloud environments comprised of different platforms, different technologies and different providers.
- Machine identity visibility needs to be straightforward and achievable across these agile and hybrid environments
- Enterprise customers need a centralized, intelligent policy to manage security across multiple, different platforms and cloud types. Crypto and cloud-agility and centralized policy control provide for the required security visibility and relieve the burden on DevOps so they stop “improvising.”
- Customers need a way to automate and unify complex, integrated workflows between different cloud component.
How prepared is your organization to manage machine identities across hybrid cloud environments?
Related posts
