Bleeping Computer reported on March 23, 2021, that the Microsoft Exchange admin portal was not accessible because of an expired SSL/TLS certificate.
On that day, when Microsoft Exchange administrators attempted to access the admin portal at admin.exchange.microsoft.com, they found that their browsers were issuing warnings that the connection was not private due to an expired SSL certificate. Depending on the browser, users were blocked from accessing the site as a security precaution or shown an alert that the data may not be secure.
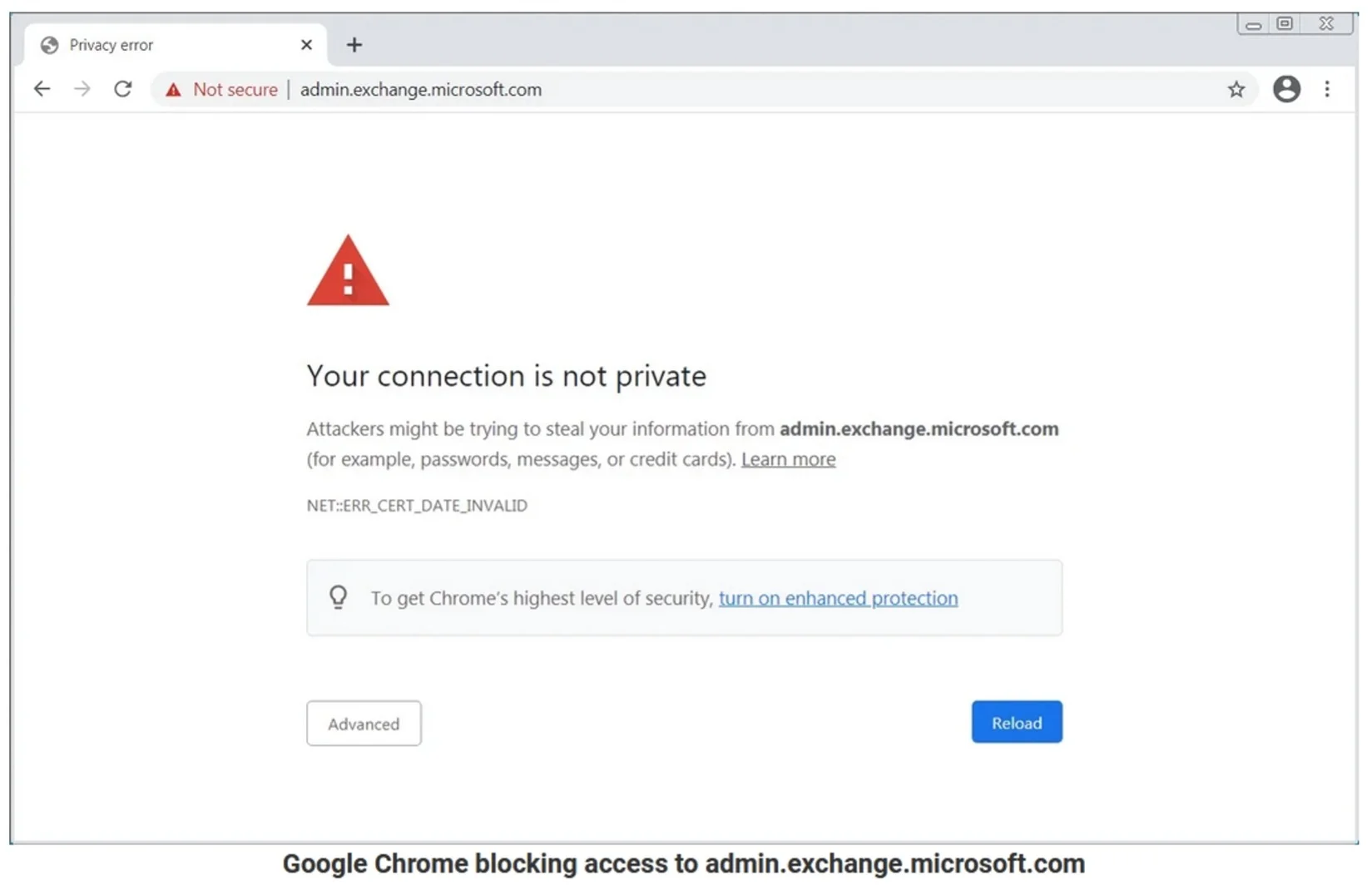
Figure 1: Image source: Bleeping Computer
Microsoft became aware of the expired certificate following a tweet by Tzatl, which prompted the company’s reaction.
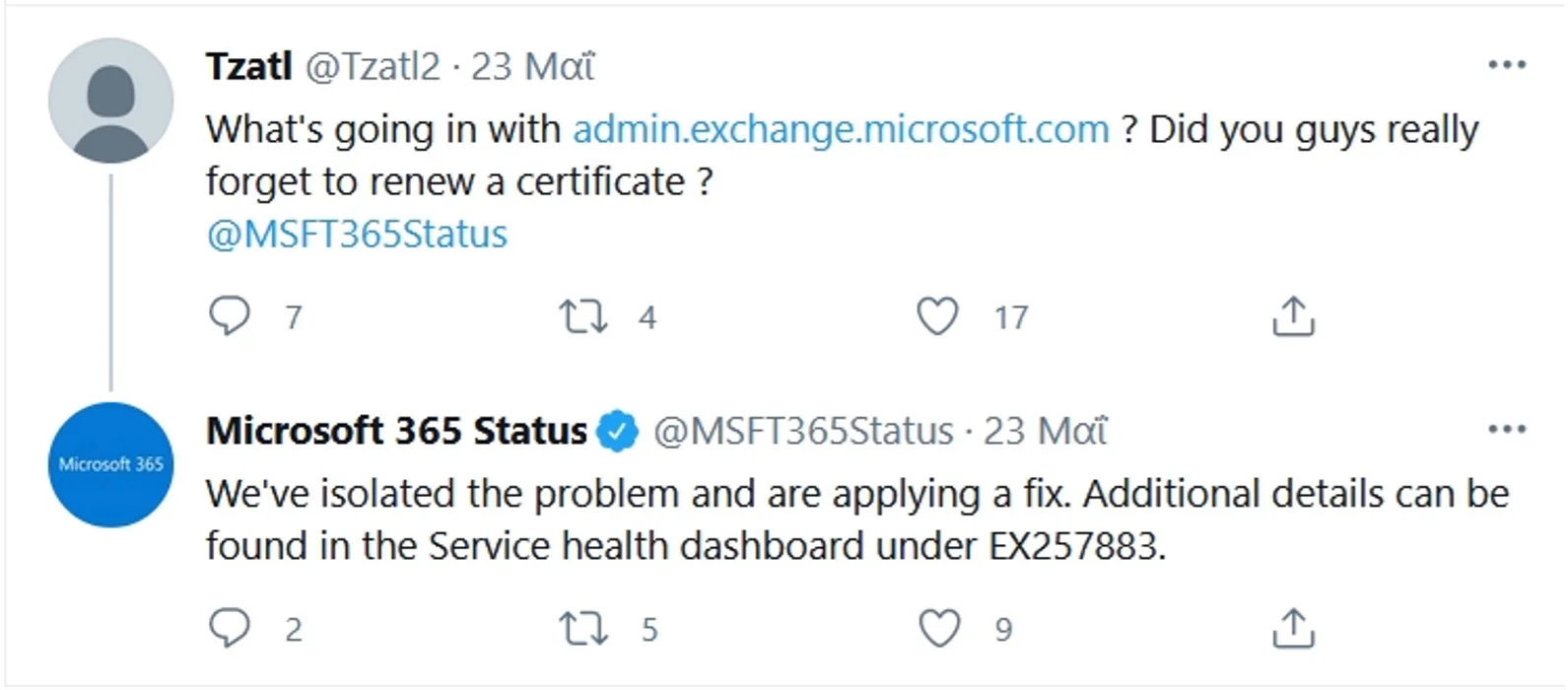
After a few minutes, Microsoft reported that “We've completed applying the configuration fix on the affected authentication component, and after monitoring service telemetry, we confirmed that the issue is now fully resolved.”
Expired certificates are an ongoing security issue
However, this incident should not come as a revelation. It is not the first time that Microsoft forgot to renew an expiring certificate - in February 2020, it was Teams which had crashed for 3 hours after forgetting to renew the corresponding certificate.
Managing SSL certificates is a painful experience for many organizations. Despite the importance that these digital certificates have on brand reputation and services reliability and availability, oftentimes certificates do expire because of broken management practices. That was the case with Spotify as well as with the State of California, when an expired certificate led to a backlog of nearly 300,000 lab records in the state’s coronavirus reporting system.
A recent study revealed that 75% of global CIOs expressed concern about the security risks connected with the proliferation of certificates. Plus, over half of CIOs say they worry about outages and business interruptions due to expired certificates.

CIO Study: Automation Vital to Address Shorter Lifespans and Massive Growth of TLS/SSL Certificates
Expired certificates: the gateway to MitM attacks
Expired certificates not only cause outages but can also act as the gateway for criminals to infiltrate corporate networks, notes Pratik Savla, Lead Security Engineer at Venafi.
“Not only can expired certificates cause unplanned system or service outages as has been seen several times over in different incidents, but what is not equally well-known is that they can also open the door through which malicious actors can find entry into one’s environment. Expired certificates lead to breaking down of the chain of trust and in turn make users vulnerable to the popular man-in-the-middle (MitM) attacks.” This is feasible, because an expired certificate breaks the chain of trust which “is critical to prove that a particular certificate originates from a trusted source,” adds Savla.
MitM are a source of concern for all security professionals since they are easy to be launched and hard to be noticed. “MitM attacks are relatively much easier to pull off and so have a remained a commonly found attack vector in the news headlines for years on end despite their awareness. If one gets down to the basic workings of an MitM attack, they’ll see that it’s relatively simple,” says Savla.
“An MitM attack involves a malicious actor intercepting the communication between a user and the server/system the user is trying to reach. There are typically two types of MitM attacks – active and passive. In the passive variety, an attacker may just eavesdrop on communications and steal sensitive credentials as well as data. On the other hand, in active MitM, the attacker would consider actively injecting malware or modifying information that is presented to a user. On top of this what is more concerning is that MitM attacks have the potential to remain unnoticed for a relatively long period of time, if its detection is not attempted in a proper way,” explains Pratik Savla.
Can we close this backdoor?
What can we do to eliminate both the risk of certificate expiration and MitM attacks? “Proper and timely renewal of expired certificates is key to mitigating the MitM attack risks," notes Savla. “The first step is to make sure that you develop and continuously update a detailed certificate inventory. Next, expiry notifications should be setup to ensure it reaches the right owners ahead of time. This includes a set period starting at least a month before the expiry date for non-critical systems and starting with at least two months before the expiry date for systems deemed critical.”
Take Control of Your Machine Identities With Automation and ELIMINATE Outages!
Related posts
