The Venafi Threat Intelligence Team found that cyberattacks and APTs that misuse machine identities have increased 1600% over the last five years, according to public data on 110 machine identity threats over a five-year period from 2015 to 2019.
How are machine identities misused by cybercriminals? Venafi vice president, security strategies and threat intelligence explains, “By stealing ‘trusted’ machine identities from global technology companies, perpetrators of APTs can execute effective attacks that don’t raise any alarms until well after the damage is done.” Bocek goes on to warn, ”There’s no doubt we’re going to see a lot more of these attacks in the future.”
Why you should be worried
An advanced persistent threat (APT) is a prolonged and targeted cyberattack during which an intruder gains access to a network and remains undetected for an extended period of time. The intention of an APT attack is usually to monitor network activity and steal sensitive or confidential data rather than to cause damage to the network or organization.
The goal of most APT attacks is to achieve and maintain ongoing access to the targeted network rather than to get in and out as quickly as possible. APT attacks typically target organizations in sectors such as national defense, manufacturing and the financial industry, as those companies deal with high-value information, including intellectual property, military plans, and other data from governments and enterprise organizations.
Trusted connections can be used to gain initial access, often through advanced exploits of zero-day vulnerabilities. Attackers may use employees’ or business partners’ credentials as a means of remaining undetected long enough to map the organization’s systems and data and devise a strategic plan of attack to harvest company data.

SSL/TLS Certificates and Their Prevalence on the Dark Web
How cybercriminals misuse machine identities
While TLS server certificates enable confidentiality for legitimate communications, these machine identities can also allow attackers to hide their malicious activities within encrypted TLS connections. When a TLS server certificate is installed and enabled on a server, all users who connect (including attackers) can establish an encrypted connection to the server. An attacker who establishes an encrypted connection can then begin to probe the server for vulnerabilities within that encrypted connection.
This is how an APT attack that leverages encrypted connections works.
- APT actors gain access to a target by targeting systems through the internet, via spear phishing emails or via an application vulnerability with the intention of leveraging any access by inserting malicious software into the target.
- Once the attacker connects to the server, he establishes an encrypted TLS session. Within that encrypted session, the attacker can probe for vulnerabilities that exist on the server and its software.
- If the attacker discovers a vulnerability and sufficiently elevates his or her privileges, then the attacker can load malware, generally called a “web shell,” onto the server.
- With this web shell loaded, the attacker can send commands over encrypted connections facilitated by the server’s certificate. The attacker can then begin to move laterally within the breached organization to pivot to other systems by probing for vulnerabilities in servers accessible from the compromised system. The increased use of encryption enables an attacker who has compromised one system to move laterally and attack other systems via encrypted connections, without being detected.
- Once the attacker has successfully reached data that he or she desires, the attacker is able to use the web shell to exfiltrate data. Because the attacker is establishing TLS connections by using the server’s certificate to connect to the web shell, all the exfiltrated data is encrypted while in transit.

APTs and Heartbleed
The Heartbleed bug is a serious vulnerability in the popular OpenSSL cryptographic software library. The bug is in the OpenSSL's implementation of the TLS heartbeat extension. When it is exploited it leads to the leak of memory contents from the server to the client and from the client to the server. The Heartbleed vulnerability is registered in the NIST NVD database as CVE-2014-0160.
The heartbeat extension is used to keep a connection alive as long as both parties are still there. Occasionally, one of the computers will send an encrypted piece of data, called a heartbeat request, to the other. The second computer will reply back with the exact same encrypted piece of data, proving that the connection is still in place. The heartbeat request includes information about its own length.
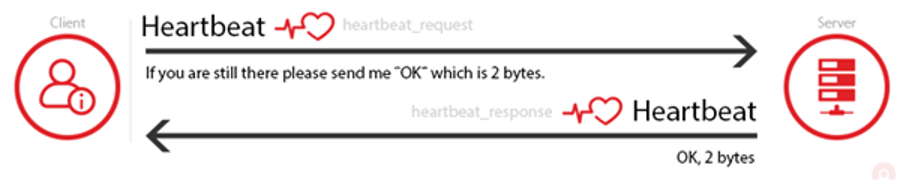
The Heartbleed vulnerability came to surface because OpenSSL's implementation of the heartbeat functionality was missing a crucial safeguard: the computer that received the heartbeat request never checked to make sure the request was actually as long as it claimed to be. So if a request said it was 40 KB long but was actually only 20 KB, the receiving computer would set aside 40 KB of memory buffer, then store the 20 KB it actually received, then send back that 20 KB plus whatever happened to be in the next 20 KB of memory. That extra 20 KB of data is information that the attacker has extracted from the web server.
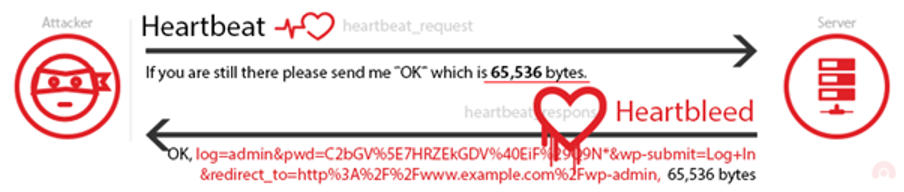
This weakness allows stealing the information protected, under normal conditions, by TLS. While a single heartbeat can be up to 64 kilobytes, there is no actual limitation to the attack. An attacker can either keep reconnecting or keep requesting, during an active TLS connection, arbitrary number of 64 kilobyte pieces of memory content until enough secrets are revealed. The researchers that discovered the vulnerability were able to “steal” the secret keys used for their X.509 certificates, usernames and passwords, instant messages, emails and business critical documents and communication.
What is the worst that could happen?
There are many well-known, high-profile APT attacks, with dire effects. The GhostNet cyberespionage operation discovered in 2009 was initiated via spear phishing emails containing malicious attachments. The attacks compromised computers in more than 100 countries. The attackers focused on gaining access to the network devices of government ministries and embassies. These attacks enabled the hackers to control these compromised devices, turning them into listening and recording devices by remotely switching on their cameras and audio recording capabilities.
- Stuxnet in 2010 was reportedly created by American and Israeli programmers as part of operation “Olympic Games” targeting the Natanz nuclear facility in Iran to control SCADA systems and ultimately create an industrial catastrophe.
- APT29, the Russian advanced persistent threat group also known as Cozy Bear, has been linked to a number of attacks, including a 2015 spear phishing attack on the Pentagon, as well as the 2016 attacks on the Democratic National Committee.
- APT28, the Russian advanced persistent threat group also known as Fancy Bear, has been linked to attacks against military and government targets in Eastern Europe, including Ukraine and Georgia, as well as campaigns targeting NATO organizations and U.S. defense contractors.
- APT34, an advanced persistent threat group linked to Iran, has targeted companies in the Middle East with attacks against financial, government, energy, chemical and telecommunications companies.
The aforementioned examples of APT attacks highlight both the motivation and the consequences of such an attack. The worst thing that can happen is to disrupt or damage a nation’s critical infrastructure, such as the electric grid, the water supply or the oil industry. Such was the case with Triton malware, which affected the industrial control systems of the Saudi Arabia based oil company SaudiAramco Needless to say, disruption of such systems can directly or indirectly affect the functioning of vital services or, even worse, the state of national security.
Besides APT attacks to critical infrastructure, other targets include healthcare organizations, financial institutions, retail and consumers goods industry, telecommunications, etc. The victim organizations of APT attacks can suffer business disruption, intellectual property loss, customer information loss, such as personal identifiable information (PII) or protected health information (PHI), reputation loss and financial loss due to legal constraints and loss of customers.
