In keeping with the latest rise of encryption attacks, Google’s Threat Analysis Group (TAG) have just uncovered a new technique threat actors can employ to sneak malware, adware, and other malicious software past trusted malware detection tools.
Users of Windows Internet Information Services (IIS), a Microsoft Windows web server, are being targeted with false notifications warning of an expired certificate that encourages users to download the malicious fake installer. How is this possible, and what can you do to protect your organization from these kinds of attacks?
Neel Mehta, Google researcher, has surmised that the cybercriminals are able to trick Microsoft’s malware detection by means of a software code-signing certificate from a legitimate certificate authority. It creates signatures Windows will accept as valid, but that can’t be inspected by OpenSSL code security tools.

SSL/TLS Certificates and Their Prevalence on the Dark Web
The phony security notification tells users that they have to “update a security certificate” and then installs malware disguised as Virus Total, which is signed with a DigiCert certificate.
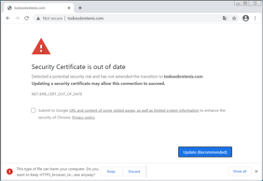
What is really being installed? TVRAT, also known as TeamSpy and Team Viewer RAT, a malware that grants its installers complete remote access to the infected machine. Attackers have been using stolen digital certificates to evade malware detection tools for a while now, for example in the recent SolarWinds attack.
In this instance, the cybercriminals are using a deliberately distorted signature that OpenSSL-based security products cannot decode. Neel Mehta said, "Security products using OpenSSL to extract signature information will reject this encoding as invalid. However, to a parser that permits these encodings, the digital signature of the binary will otherwise appear legitimate and valid."
Google TAG reported the issue to Microsoft because, as Mehta points out, the Windows operating system treats it as valid.
How can I keep my network secure?
One of the biggest steps your organization can take to protect your machine identities is to automate your certificate management strategy. How? Venafi Control Plane for Machine Identities allows complete visibility into your network, allowing you to immediately identify and react to potential threats!
Why Do You Need a Control Plane for Machine Identities?
Related posts
