According to StatCounter in November 2018, Mozilla Firefox was the third most popular web browser platform worldwide, with about 4.92% overall marketshare. (Google Chrome was number one at 61.75%, and Apple Safari was number two at 15.12%.) That takes into account both desktop and mobile spaces. Of course, not all implementations of the Firefox platform are labelled Firefox, as there are also many popular forks. Tor Browser is one of those forks, and there are many others. A fork has most of the main Firefox code, so bugs that affect vanilla Firefox usually also affect the many forks of it as well.
Frankly I’m really impressed by the Mozilla Foundation’s commitment to cybersecurity and user privacy. Firefox’s opensource nature is one reason why implementations like Tor Browser are based on Firefox, but Mozilla’s pre-existing security features are another. Those security features, such as anti-tracking, are a reflection for Mozilla’s security philosophy. As written in their Online Privacy and Security report:
“One of Mozilla’s founding principles is the idea that security and privacy on the internet are fundamental and must not be treated as optional. This core value underlines and guides all of Mozilla’s work on online privacy and security issues—including our product development and design decisions and policies, and our public policy and advocacy work.”

CIO Study: Automation Vital to Address Shorter Lifespans and Massive Growth of TLS/SSL Certificates
Many of the Firefox Add-ons developed by third parties, such as HTTPS Everywhere and Privacy Possum, are excellent for improving user security on the web. Many more third-party Add-ons aren’t security-related, but offer useful features some people want, such as tab organizers and RSS readers. Some Firefox forks have a few Add-ons built in. The Tor Browser I previously mentioned has HTTPS Everywhere and an anti-tracking Add-on built in.
Well, guess what! On Friday May 3rd, an expired certificate caused all Add-ons in both vanilla Firefox and its forks on desktop to stop working! Users got loads of error messages alerting them that their Add-ons weren’t working. The certificate in question is a machine identity which helps to sign Add-ons into Firefox to prevent unauthorized Add-ons from being able to harm user security. Unauthorized Add-ons and other such web browser plugins are a common form of malware.
Mozilla’s Kev Needham acknowledged the problem on the Mozilla Add-ons Blog
“Late on Friday May 3rd, we became aware of an issue with Firefox that prevented existing and new add-ons from running or being installed. We are very sorry for the inconvenience caused to people who use Firefox.
Our team has identified and rolled-out a fix for all Firefox Desktop users on Release, Beta and Nightly. The fix will be automatically applied in the background within the next few hours. No active steps need to be taken to make add-ons work again. In particular, please do not delete and/or re-install any add-ons as an attempt to fix the issue. Deleting an add-on removes any data associated with it, where disabling and re-enabling does not.”
If “Allow Firefox to install and run studies” has been disabled in the user’s preferences, they will need to enable the feature in order to install the hotfix.
I’m glad that the Mozilla team are working quickly on this expired certificate problem, but it just goes to show how common of a problem expired certificates are for large tech companies and media organizations. As I wrote here just last week:
“The reputational damage from web downtime (caused by expired certificates) is difficult for an accountant to ledger, but it definitely affects a company’s bottom line. Transactions aren’t made, services aren’t delivered. If I’m in the mood to buy a new pair of boots and the website of one of my favorite shoe stores is down, I’ll just go to the website of another shoe store, their direct competitor. It’s as simple as that.”
But Firefox’s expired certificate doesn’t just affect a website, it affects all desktop Firefox users, no matter where on the web they go!
This issue didn’t go unnoticed by Venafi on Twitter.
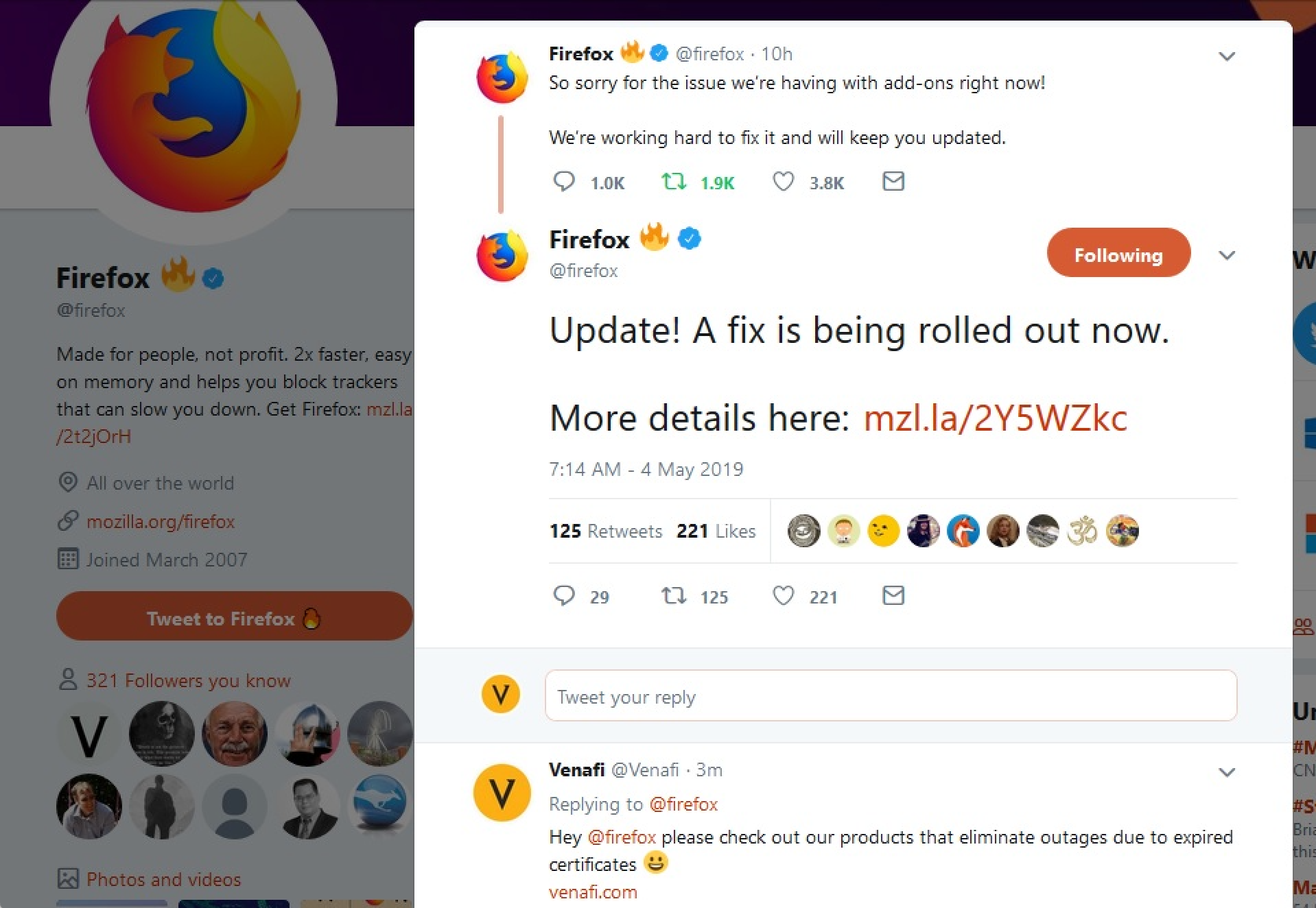
Okay, that’s a bit cheeky. But it’s true! This embarrassing problem could have been prevented with the use of Venafi machine identity management solutions!
Get a 30 Day Free Trial of TLS Protect Cloud, Automated Certificate Management.
Related posts
