This is the first of two technical blogs that discuss FAST IT and its impact on security. We understand that the development landscape is changing rapidly and we are here to help you to keep pace with the speed of that change. We’ll post part two shortly.
In this blog, we explore how the lifecycle for critical cryptographic assets can be seamlessly and centrally governed by policy within today’s highly dynamic fast IT environments. We’ll cover a high-level use case for how the Venafi Trust Protection Platform integrates with the Chef DevOps framework using a cookbook for the procurement of X.509 certificates. The principles outlined in this use case can just as easily be incorporated into almost any other DevOps framework.
Controlling the use of keys and X.509 certificates in today’s highly dynamic world of compute, container, and micro services raises new challenges that require a new approach. In this new world which emphasizes fast delivery, security simply cannot be enforced using traditional slow IT policies and processes.
The speed of providing IT services has accelerated dramatically.
Business consumers and IT professionals are demanding new IT services and environments that are created at scale and speed. They demand Amazon AWS-'like' capabilities at similar speeds for 'internal' IT services. Most enterprise organizations have moved to a bi-modal IT structure with two stream/two speed IT: one that supports existing apps that require stability and another that delivers fast IT for innovation and business-impacting projects. To facilitate this demand many organizations are implementing processes and tooling that favor short-lived virtual machines, containers, and micro-services over the more traditional long-lived computing platforms.
While these new tools and frameworks allow for speed and scalability they do not provide centralized security services. Thus, security often falls back to the traditional slow, manual, and error-prone way of doing things. Even worse, security policies and procedures are often ignored in-lieu of just getting the job done quickly.
However, keys and certificates are the foundation for securing modern SSL/TLS-based data communications. There is nothing to replace this foundational system of trust on which the Internet is based, nor will there be any time soon - which means keys and certificates are here to stay and will continually increase in numbers.
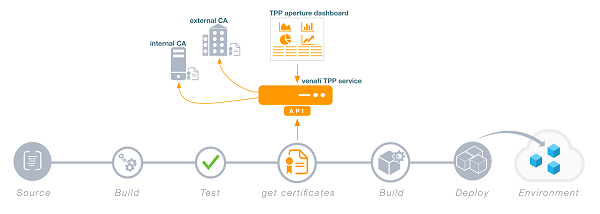
Figure 1. Automating key and certificate support for DevOps
Venafi’s industry-leading and proven Trust Protection Platform is already helping Global 5000 organizations fully encapsulate, secure, automate, and audit entire key and certificate lifecycles across their traditional IT services and infrastructures. Through the use of the Venafi API, all of these services can be made available to the new world of fast IT.
Going fast with keys and certificates.
For DevOps, the process for procuring correctly issued certificates often falls into the ‘SlowOps’ category of legacy IT, and significantly reduces velocity. DevOps teams are often found working outside of corporate security boundaries, policies, and guidelines. This isolation helps these teams get development and new innovation done faster, at the speed of business. But it also potentially introduces security risks and bad practices within the very environments that are being created - all in favor of speed.
Here are some examples of what DevOps teams may decide to do to get around the time it normally takes to procure certificates for their environments. Examples of shortcuts include:
- Don’t use TLS/SSL
- Create their own certificate authorities
- Create self-signed certificates
- Use unapproved certificate issuers
- Create certificates with weak signature algorithms
- Deploy certificates with long expiration periods
- Misinterpret or completely ignore security policies
The Venafi Platform can be configured to selectively expose some or all of its workflows and processes via easy-to-use REST APIs. These APIs can then be directly consumed by almost any DevOps, including continuous integration/delivery, automated build/deployment and container solutions such as Chef, Ansible, Puppet, SaltStack, Hashicorp, Docker, Kubernetes, UrbanCode to name a few.
Use Case - Venafi Platform integration with Chef
Figure 1 below provides an example of how the Venafi Platform easily integrates into a new or existing Chef framework. A simple sample cookbook can be used by DevOps teams as a way to get started when using Venafi’s key and certificate services.
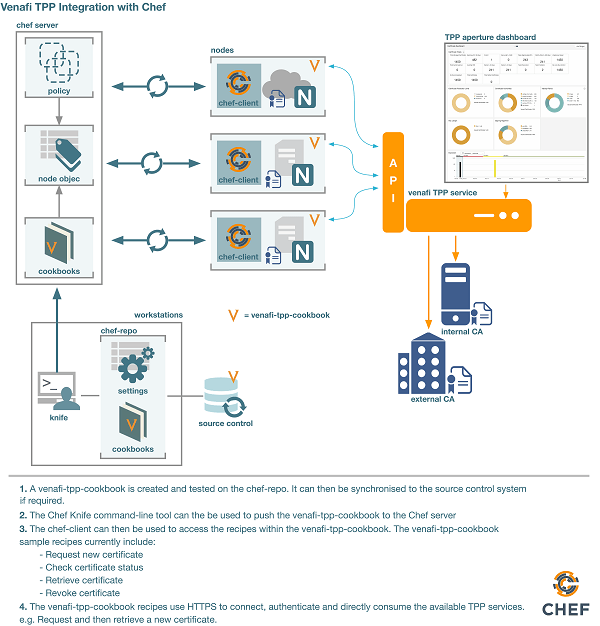
Figure 1. - Example Venafi Trust Protection Platform integration with Chef Framework
Provide fast security with fast IT
The Venafi Platform lets organizations realize the benefits of Fast IT without compromising security. Security teams can now centrally define policy through the Venafi API and enable DevOps to properly comply with security policies and best practices. Venafi makes it easy for DevOps teams to correctly apply and build in security from the beginning.
Our platform provides the following benefits to DevOps teams:
- Unique keys and certificates are generated and issued on demand in seconds
- Uses the same platform for DevOps as that used by existing security teams and system administrators
- Single view of security posture and compliance with integration to Help Desk systems and SIM/SIEM environments.
- Automated remediation and re-enrollment as standards and policies change
- Automated alerts based on anomalies detected inside an organization and externally
- Virtually infinite scalability without additional administrative overhead
NOTE: The use case depicted in this article is intended to provide a very high level example of how Venafi APIs can be used by security teams to provide key and certificate services to DevOps teams. Since most of the components fall outside the Venafi domain the solution has not been subjected to any security validation, screening, or ratification by Venafi.
