Venafi recently sponsored a webinar with Secureworld on how to get a handle on shorter TLS certificate lifespans or "certificate shrinkflation”. In the webinar, Florin Lazurca and I got to talk about the proposal from Google to shorten the lifespan of public-facing certificates to 90 days. We’re not fortune tellers, but we do believe this change, or something close to it, will happen in the not-too-distant future. When it does, anyone still trying to manage large numbers of certificates manually should expect issues like outages caused by expired certificates. So now is the time to think seriously about how to prepare through automation.
How did we get here?
Since September 2020, public-facing TLS certificates have had a lifespan of 13 months, a number agreed to by a majority of members of the CA/Browser Forum, a consortium of Certificate Authorities (Cas) and browser vendors. The new proposal from Google would reduce certificate lifespans by 75%. And while that number is extreme, the reduction itself is in line with the frequency of previous reductions. Since 2011, the group has consistently agreed to reduce lifespans every 2-3 years.
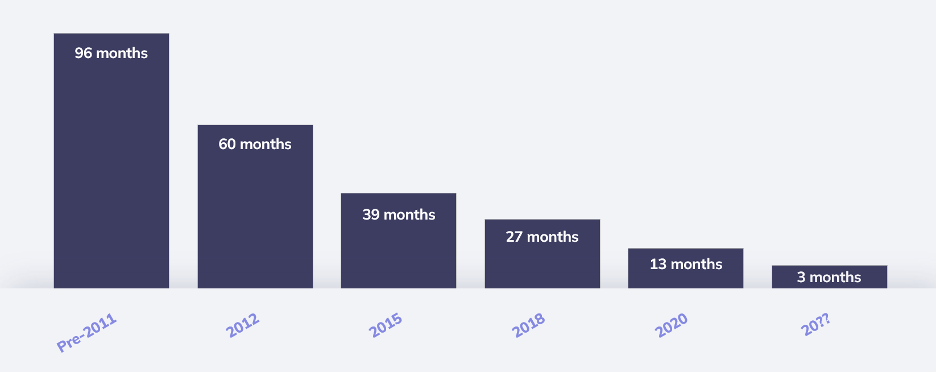
90-Day certificate validity proposal from Google
In March of this year, the Chromium Project released in a “Moving Forward, Together” roadmap, where Google announced that it intended to move to a 90-day certificate, whether by CA/B Forum ballet or by policy alone. In this document, Google suggests four key reasons for this change:
- Force automation. At 13-month lifespans, many organizations continue to manage certificates manually (with mixed results). A 90-day certificate lifespan would be a forcing factor for automation, and Google argues that it would be a good thing to force everyone away from time-consuming and error-prone manual issuance processes.
- Adoption of new capabilities. A side-benefit to automation is that it’d be faster for the industry to adopt new security capabilities and best practices.
- Reduce reliance on revocation. Today, when a certificate needs to be revoked (say its private key has been compromised), the mechanisms to ensure the CA marks the revocation and browsers know about are not ideal. Certificate Revocation Lists (CRLs) are maintained by CAs and can cause performance issues. Also, Online Certificate Status Protocol (OCSP) can cause concerns about privacy. Shorter lifespans would reduce the need for revocation and avoid these concerns.
- Decrease CT log disqualification impact. Certificate Transparency (CT) log disqualifications occur when a certificate doesn't contain at least three Signed Certificates Timestamps (SCTs) from three independent logs. If a certificate doesn't contain those three SCTs, then it won't be CT qualified and will therefore be rejected by the browser. Like the situation with revocation, shorter-lived certificates will decrease the impact if this situation happens.

Don’t Delay: 5 Urgent Actions to Prepare for 90-Day TLS/SSL Certificates
While these are sensible reasons for moving to shorter certificate lifespans, it’s also rational to have concerns about increased certificate management requirements. We know that certificate-related outages are a challenge today with 13-month lifespans. How many more outages will we experience if those same certificates need to be renewed at least six times more often? (Best practice is to renew certificates 30 days before expiry.) For teams that are still performing certificate lifecycles tasks manually, will they be able to keep up and/or automate quickly enough? It’s a question everyone should be considering.
But the issues go beyond public-facing certificates. We know that the lifespans of certificates issued by private CAs on internal networks are also getting shorter, sometimes to just hours or minutes driven by DevOps, cloud, cloud native and more. Like it or not, TLS certificates with shorter lifespans are already a factor in most networks. Whether it’s to keep up with the pace of internal teams, or to prepare for what will likely soon be shorter public-facing certificates, now is the time to start automating the management of these important machine identities.
Moving from manual to automated certificate management
When you look at the administrative tasks associated with a TLS certificate throughout its life cycle, there are many areas where automation is beneficial (if not required). With Venafi TLS Protect, I can automatically generate a key pair and CSR when I need to get a new certificate, submit the CSR to a CA, retrieve and install the certificate, then restart the application and validate that the certificate was correctly installed. All of that can happen much faster than it would manually. And maybe more importantly, I can do it all without the errors that I’d introduce if I tried to do it all manually. However, while the steps to automate may seem fairly straightforward, it gets more complicated in organizations where we have multiple environments, technologies and teams.
One of the best guides to help us understand how to bring these people, processes and technologies together to automate the lifecycle of TLS certificates is the NIST SP 1800-16 publication, Securing Web Transactions. You can learn more about NIST SP 1800-16 in this white paper. The NIST publication recommends that “automation should be used wherever possible for the enrollment, installation, monitoring, and replacement of certificates, or justification should be provided for continuing to use manual methods that may cause operational security risks.”

CIO Study: Automation Vital to Address Shorter Lifespans and Massive Growth of TLS/SSL Certificates
At a high level, NIST recommends the following levels of involvement:
- Security or machine identity services team: Provide a central system that supports resource owners in automating management of certificates.
- Resource owners: Automate the management of your certificates.
It’s also important for that central system to deliver a core set of capabilities, for both the security team responsible for the central system and the resource owners responsible for certificates on their machines. At a high level, the central system must deliver:
- Observability: Find all TLS certificates (and other machine identities), determine who owns them, and build an inventory to monitor them.
- Consistency: Define and enforce enterprise security policies using automation and workflows.
- Reliability: Make machine identity requests available in milliseconds as a fast, highly available service.
- Flexibility: Enable resource owners to work with the central system in the way that works best for them.
Venafi’s solution for automating the management of TLS certificates is TLS Protect, which you can learn more about sign up for a free 30-day trial from our website.
Benefits of automation go beyond certificate life cycles
We started our webinar with a discussion on the 90-day certificate lifespan proposal from Google and how it, and other factors, are driving the need to automate the management of TLS certificates. We ended on some of the benefits to automation, outside of being able to renew certificates at a more frequent cadence. Based on what we’ve seen from Venafi customers, there are many! We can break them down into three categories:
- Efficiency improvements. Many Venafi customers have told us of the massive efficiency improvements they’ve achieved through automation. One of the biggest benefit areas is eliminating errors, like a resource owner making a mistake when they request a certificate and having to double back later to fix things or not configuring the certificate correctly when installing it. We’ve seen some of our larger customers save hundreds of dollars per certificate in management costs, allowing them to redeploy hundreds of staff simply by eliminating manual tasks.
- Crypto agility. Most Venafi customers have at some time needed to replace many certificates at once. Most often it’s to deal with the aftermath of a critical vulnerability where a vendor has told them not to trust certificates on the vendor’s product after a certain patch date. Others want to replace a PKI provider after a merger or acquisition or to move from one PKI provider to another. Automation enables them to be crypto-agile and make big moves when they need to.
- Future proof. We’ve seen automation enable many Venafi customers extend TLS machine identity management to groups like development teams creating cloud native applications at machine speed, something that would never be possible to keep up with manually. They’re keeping up with the pace of all the other groups around them!
Webinar recording available!
If you missed the ‘Certificate Shrinkflation” webinar and are interested in learning more after reading the highlights here, please check out the on-demand recording. And visit our webinars page anytime to see what’s coming live in the future and check out other on-demand recordings.
Certificate Shrinkflation: How Automation Overcomes the Growing Challenges of Shrinking Lifespans

2024 Machine Identity Management Summit
Help us forge a new era of cybersecurity
Looking to vulcanize your security with an identity-first strategy? Register today and save up to $100 with exclusive deals. But hurry, this sale won't last!
