Does the office feel empty? Can’t find your system administrator? There’s a scheduled security install that has been languishing for days, mysteriously untouched? You and your office might be experiencing Black Hat syndrome.
The top minds in InfoSec and IT have been siphoned off for a week-long industry rite, converging in Las Vegas yearly to meet with others of like mind to discuss the safety of information security systems and what can be done to hack them. Ahem, protect them. The best ways to keep ahead of the curve are expounded, explained and exploited at the industry’s largest, “most … relevant information security event series in the world.”
Missed it? We didn’t.

SSL/TLS Certificates and Their Prevalence on the Dark Web
Hacker vibes | “With great power comes great fesponsibility”
What’s the difference between a penetration test and a penetration attack? Motivation. And probably a few billion dollars. With the amount of oven-ready hacking techniques being thrown around at this year’s conference, the ethics of testing has never been more relevant.
#HackerSummerCamp

https://twitter.com/4rkan3/status/1157754020380868608?s=20
Glitch a secure chip for $5 USD
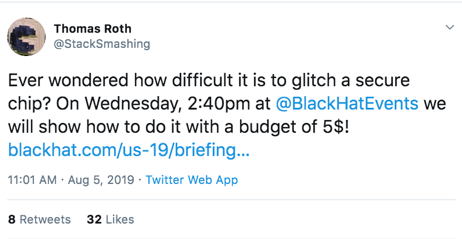
https://twitter.com/StackSmashing/status/1158422730305409024?s=20
Is this true?
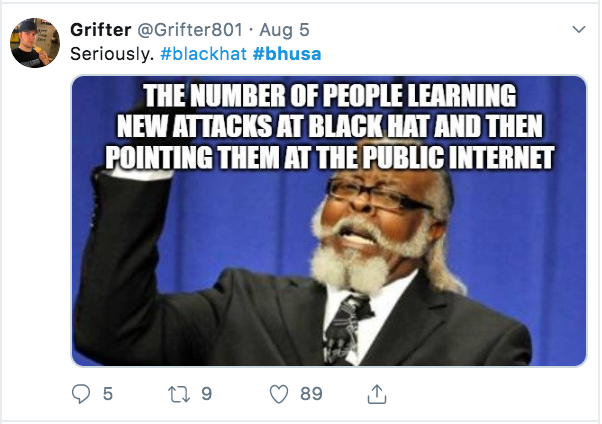
https://twitter.com/Grifter801/status/1158457477123301377?s=20
And should it go too far:

https://twitter.com/BlackHatEvents/status/1158822587335630848?s=20
IoT | Naked and afraid
You have a “super strong” password, you use fingerprint ID and you can unlock your phone with your face. However, some of the most potent threats aren’t with your identity, but the identity of the device itself. Dare to dabble?
"Not inherently secure" Are you doing what it takes to secure your devices?
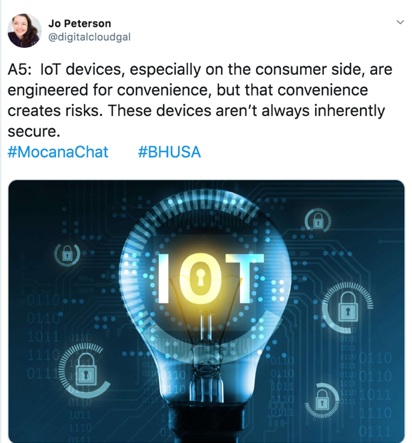
https://twitter.com/digitalcloudgal/status/1159154025004032001?s=20
IoT: Hack this House
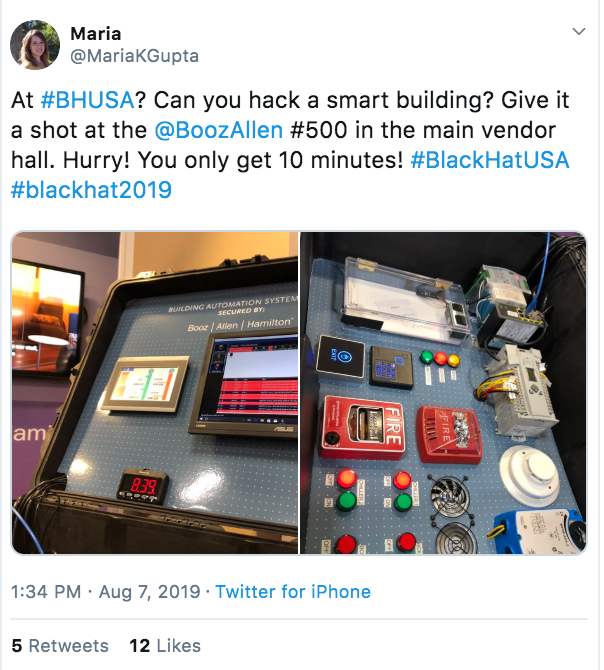
https://twitter.com/MariaKGupta/status/1159186170347003905?s=20
Security Labels on bedside monitoring devices a "Must Have"

https://twitter.com/HopeFrank/status/1159152841983795201?s=20
“IoT requires a Chief Risk Officer”

https://twitter.com/HopeFrank/status/1159153909190893568?s=20
The best way to defend is to hack yourself first. Know how.

https://twitter.com/snaropanth/status/1157687969899114497?s=20
What they did there [what you missed]
Haven’t had enough? Here are some highlights for useful knowledge shares discovered at this year’s conference, and the places you can find them.
“Find...more vulnerabilities out of coverage-guided fuzzing”
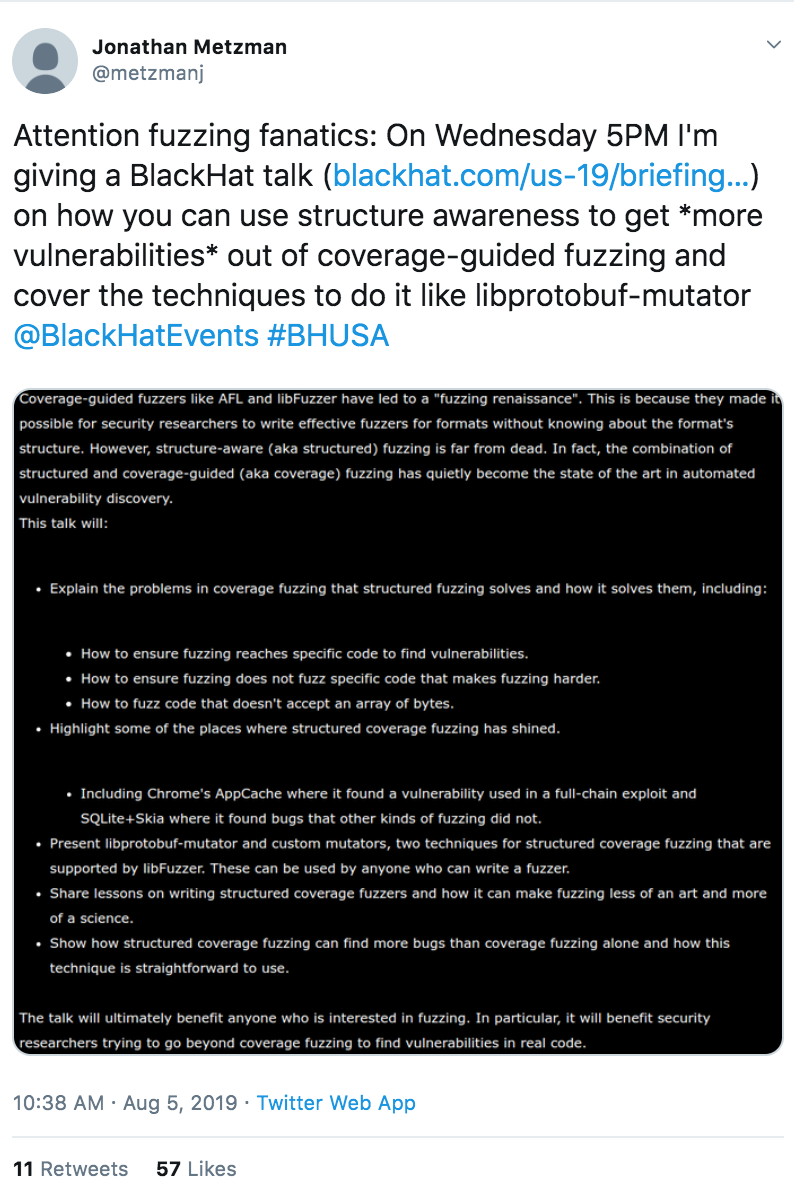
https://twitter.com/metzmanj/status/1158417076010094598?s=20
How to Reverse Engineer a Windows Malware

https://twitter.com/neslihangulery/status/1158184222437208064?s=20
Never before seen OEM security issues
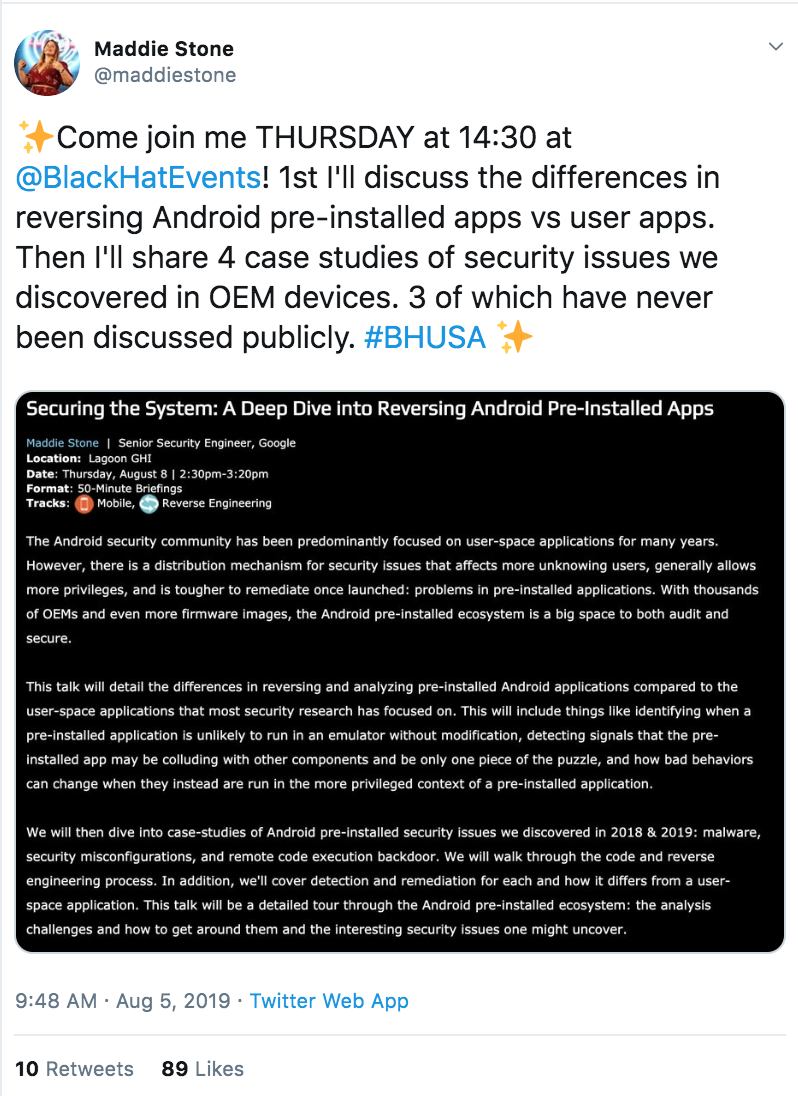
D. All of the above
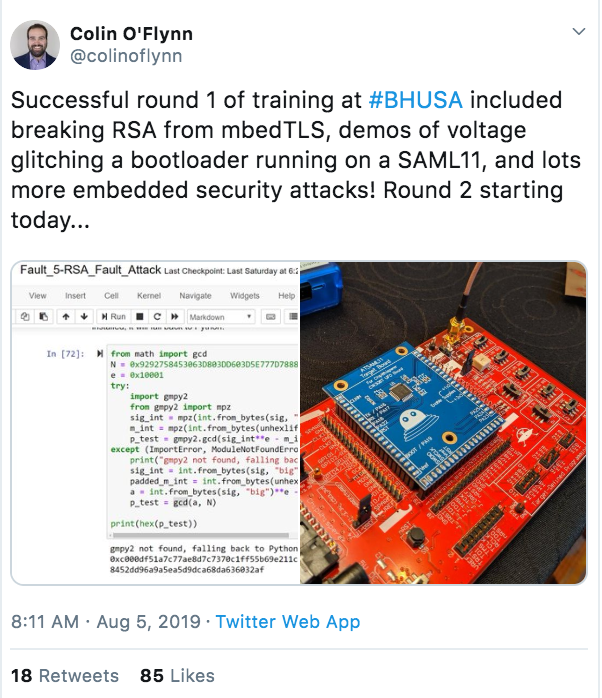
Food for thought
If a tech conference has done its job, people will walk away not only knowing different things, but thinking different things. Take a look at some of the best thought concepts to come out of a week of cyber security, tech geniuses and Las Vegas.
"Collaboration, Not Competition" [Hackers]
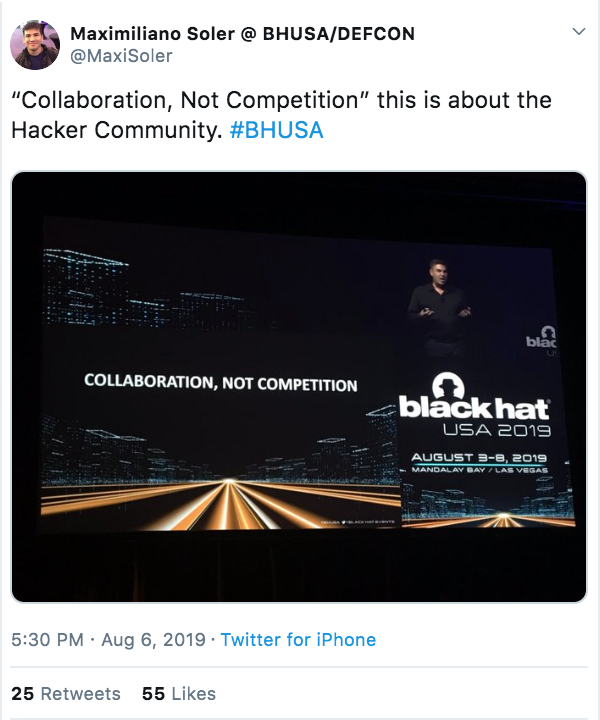
https://twitter.com/MaxiSoler/status/1158883031085723650?s=20
"Technology is deciding the fate of the world, and we are everywhere in its chains"
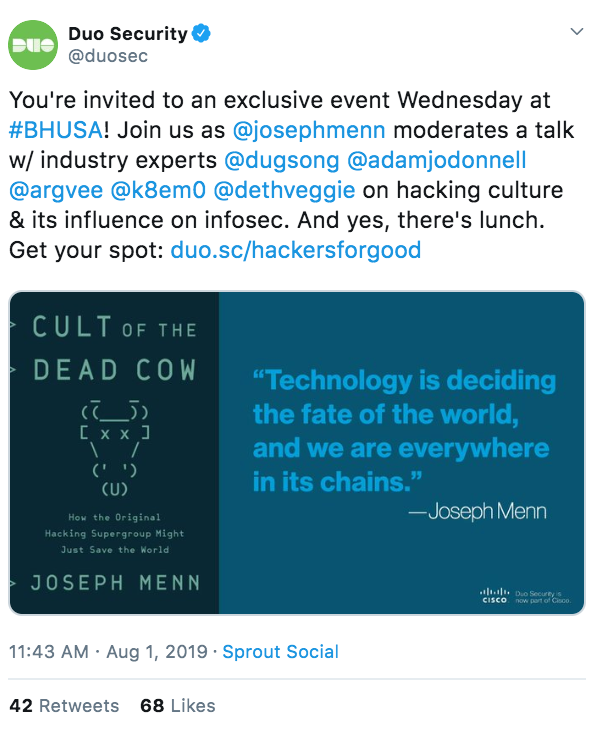
https://twitter.com/duosec/status/1156983687495507970?s=20
Strange dichotomy: How can you ever be sure you’re 100% secure?
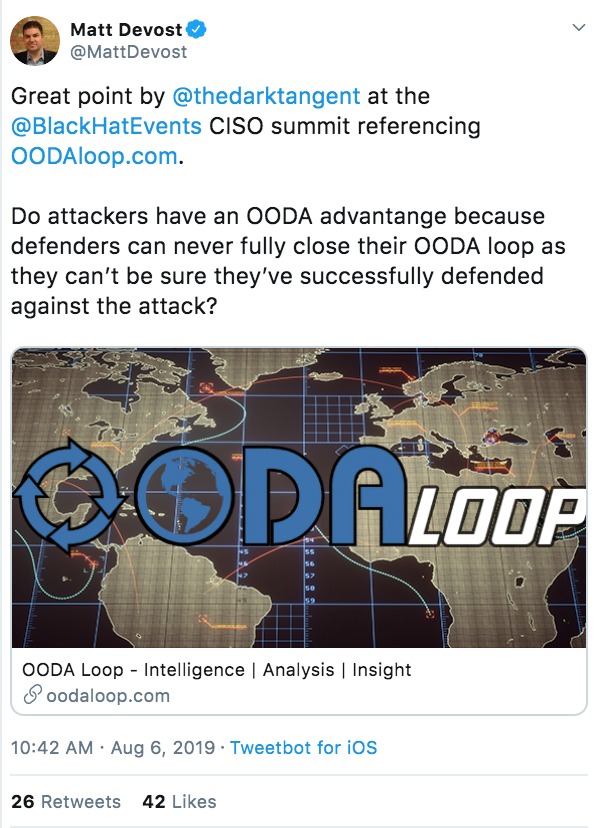
https://twitter.com/MattDevost/status/1158780456000561152?s=20
Is IT on an island?
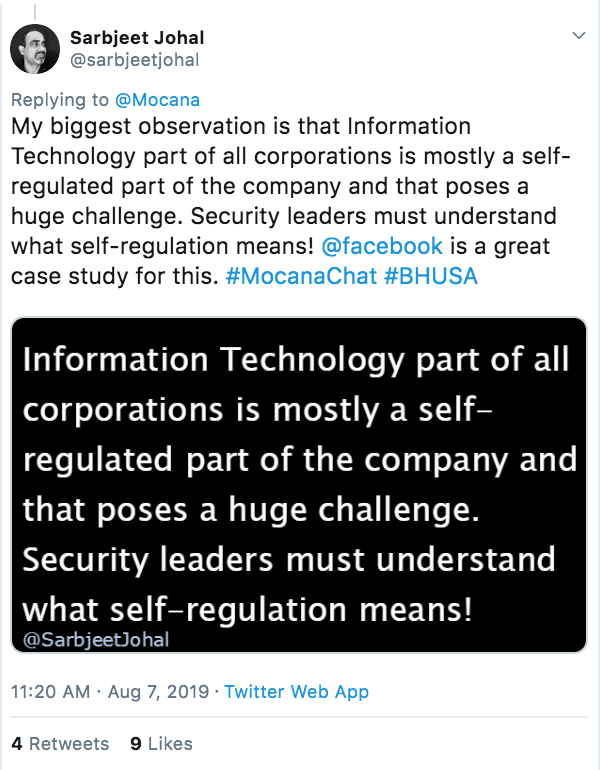
https://twitter.com/sarbjeetjohal/status/1159152416027111424?s=20
"Every security team is a software team now"
https://twitter.com/duosec/status/1158057764855472128?s=20
Hacking Ethics: The Social Good

https://twitter.com/duosec/status/1158057764855472128?s=20
Stay informed with next week’s blogs as we release exclusive Venafi survey results from Black Hat 2019 and reveal new finds on the state of the cyber security landscape and machine identity management.
Why Do You Need a Control Plane for Machine Identities?
Related Posts
