Over the last 30 years, advancements in quantum computing have posed a challenge to the security of cryptography as we use it today. Both RSA and ECC will be broken, and symmetric key algorithms will be weakened because of this risk. As a result, governments across the world are investing billions of dollars to stay on top of these advancements. From a machine identity management perspective, the most important change is coming from the standardization of the quantum safe algorithms being carried out by NIST. This means we'll see a transition period as we work through the migration to new cryptography, like we did for SHA-1, which took years to complete. But this time we have the ability to make the transition as efficient and seamless as possible.
The business impact of delaying quantum readiness will include vulnerability to breaches, reputation damage, and financial loss. And so, the question for us is what should we do about it now to minimize the potential impact? We want to be prepared. To do so, we need to take the following two steps.
- First, to avoid data compromise, we need to implement quantum safe cryptography.
- Second, we want to be able to do it fast, so we need to modernize with speed and agility and be able to quickly respond and adapt to attacks while we're reducing the cost of remediation.
Are these quantum security measures achievable for machine identities? Well, we certainly need to move to quantum persistent cryptography, but we also need to maintain sound machine identity management practices. And this includes visibility, automation, and policy enforcement. We need to protect all machine identities, and we need to make sure that the integrations are easy to do.
Quantum computing and the state of current cryptography
Currently, we are heavily reliant on the TLS protocol to protect our digital economy. The cryptography used by TLS assumes an inherent hardness that would prevent the decryption of data by anyone who doesn’t have access to decryption keys. For example, the RSA algorithm relies on the mathematical principle that the product of two prime numbers is difficult to factorize.
But the security of these time-tested algorithms may become irrelevant when the first viable quantum computer becomes available. Quantum computers will have powerful enough processing to break currently impenetrable encryption algorithms in a matter of hours. By comparison, it would take conventional computers billions of years to break current encryption.
The good news is that smart folks are already beginning to develop and use quantum cryptography. But this is a forward thinking move and is not likely to replace current cryptographic any time soon. In the meantime, we have post-quantum cryptography, which runs on our current computers, but is based on harder mathematics. This is important because when quantum computing becomes viable, traditional computing will not just disappear. At that point, it will become even more critical to have quantum-secure cryptography that runs on current computers.

Prepare for the Future of Cybersecurity: InfoSec's Guide to Post-Quantum Readiness
Where do we start preparing for quantum computing?
There's all of this work that we're beginning to think about around how we prepare machine identities for protection against the quantum threat. Let’s start by focusing on what this means from your organization's perspective and how this starts to impact your systems. We hear about quantum impacts everywhere—including in movies and TV shows. Quantum computers are often seen as these fantastical new machines that are being developed all around the world right now. Governments and industries, from the largest enterprises to the newest startups, are focusing on quantum computing. And that's mainly because they have this promise of building and solving problems that we can't solve today.
Quantum computers are very good at one specific math problem—and that math problem unfortunately underlies the cryptography that we use to protect the internet today. Shor's algorithm is used to solve this really cool math problem. Shor’s algorithm, running on a large-scale quantum computer, makes the encryption we rely on today for our internet communications and public key infrastructure—such as RSA and Elliptic Curve—obsolete. What? No security? Now this sounds like a doomsday type scenario. Don’t despair, it's not. This is a planning problem, and we need to start by clearly understanding how big this issue is and where it affects our systems.
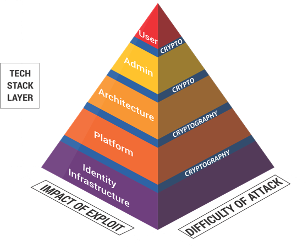
Source: ISARA Corporation
If we look at this pyramid, we can see that the cryptography we rely on is everywhere within our organizations. For example, you have a certificate and you use it to access your systems, but it impacts platforms and the architecture of the computer systems that you use, the ability to authorize administrative commands, even how users interact with something like online shopping.
You know these are all super important, and as an organization you need to start thinking about how we prepare our systems to be ready. This may sound like too big of a problem to solve. But it's really not. Your success will be measured in terms of planning and preparation. So, let's look at some specific use cases to help focus your efforts:
- Future-proof your communications systems
If I'm in an organization today and I'm thinking about preparing for the quantum threat, the first thing I'm going to do is focus on future-proofing communications. Quantum computers are expected about 10 years from now. If they can break commercial communications, then I need to ready my communications today so that they are protected 10 years from now. I should start looking at solutions now. - Plan your identity and access management migration
Even with new algorithms and processing power, machine identities will still have a strong role in protecting quantum computing. Now, I have this public key infrastructure, the Certificate Authority, that we use for protecting and identifying and authenticating users in my environment. Machine identities are impacting and being used by so many different systems in my environment. I need to start thinking about that IT migration problem and solve it to make sure my systems are ready today for quantum developments. - Prepare for authenticated software and firmware updates
We will still need to authenticate machines in a post-quantum world. For example, my vehicle that might be getting software updates over the air is relying upon a root of trust, which I know needs to be protected in order for my software update to be authenticated. If I'm a car manufacturer, or I'm an OS provider who is relying on a root of trust within a computer system, I should start thinking today about how I protect myself from the quantum threat so that my over-the-air software updates can’t be spoofed by an adversary.
As you can see, if you have not started already, it’s time to get planning! While I was at ISARA, we worked to bring the tools and the knowledge needed to face new quantum risks. One of the projects that I'm particularly proud of was a cryptographic management platform that reveals your blind spots and most importantly, equips you to take action. Additionally, ISARA collaborated with Venafi and Crypto4A through the Machine Identity Management Development Fund to build integrations with the Venafi Control Plane for Machine Identities to enable a quantum-safe solution that you can start using today.
Learn more about quantum-ready integrations on the Venafi Marketplace.
(This post has been updated. It was originally published on September 15, 2021.)
