The digital world is moving to HTTP/3, and this implies huge changes in the way applications will use TLS. The HTTP/3 stack with QUIC is a new reality for machine identity management where secure sessions using TLS endpoint encryption are established with a single handshake. This means applications now natively have the capability for identity. But the really important change is that developers no longer need to build-in and configure TLS for HTTP flows as the application is inherently capable of creating secure connections using HTTP/3.
But this new development does not mean that TLS machine identities can now be on autopilot. In this new world, developers must still ensure the standard capabilities and policies for certificate provisioning and rotation are built into the development process. In modern cloud native environments with fast moving, short-lived workload cycles, defining specific HTTP/3 development flows for certificate management would be a significant task for developers. What both developer and security teams need is a simpler foundation to use HTTP/3 that can securely connect highly distributed microservices using TLS and mTLS with certificate management policy and rotation natively built into the application.
How HTTP/3 with QuicSec will simplify the way we manage microservices
Easier management of microservices, reduced complexity for developers and better security for applications using HTTP/3 is the premise under which QuicSec has been developed, a newly released open source project by Pod8, built with the support of the Venafi Machine Identity Development Fund. QuicSec adds HTTP/3 support to existing HTTP application flows along with certificate management automation and transparently enables security using mTLS.
This is great news for cloud native developers and security teams alike because certificate management can be difficult at high volumes, and connecting microservices across multiple platforms and environments is complex. Using QuicSec, these teams have a security strategy and forward path to adopting HTTP/3 while instantly enabling all existing applications to natively automate TLS and mTLS within existing HTTP flows. This will remove much of the present complexity associated with managing external proxy configurations, control planes and sidecars to inject TLS and mTLS into HTTP flows. And in the end, it will ultimately improve the security posture for applications.
As middleware that works natively within the HTTP/3 stack, the QuicSec open source project from Pod8 provides:
- Accelerated application migration to HTTP/3 with better performance and integrated security
- Out of the box cloud native support for certificate provisioning and rotation using cert-manager
- Universal mTLS workload protection which removes the need for external proxies and sidecars with multiple control planes
- The added ability to observe, troubleshoot and operate with logs and metrics that can be integrated with popular observability platforms

Zero Trust with cert-manager, Istio and Kubernetes
Seamless HTTP/3 machine identity security for cloud native using cert-manager
QuicSec has integrated cert-manager to natively use TLS and mTLS encryption specifically for cloud native applications to take care of the process for issuing and rotating X.509 certificates for Kubernetes and OpenShift environments. This allows the cloud native application to use cert-manager as the native machine identity component for HTTP/3 cloud native applications and easily automate mTLS encryption along with certificate rotation.
QuicSec builds-in cert-manager, but more precisely it uses cert-manager’s csi-driver-spiffe component to automatically mount a certificate into a pod. This is significant because the CNCF SPIFFE project provides a universal identity control plane for distributed applications which has become the standard open source identity framework for assigning identities to workloads.
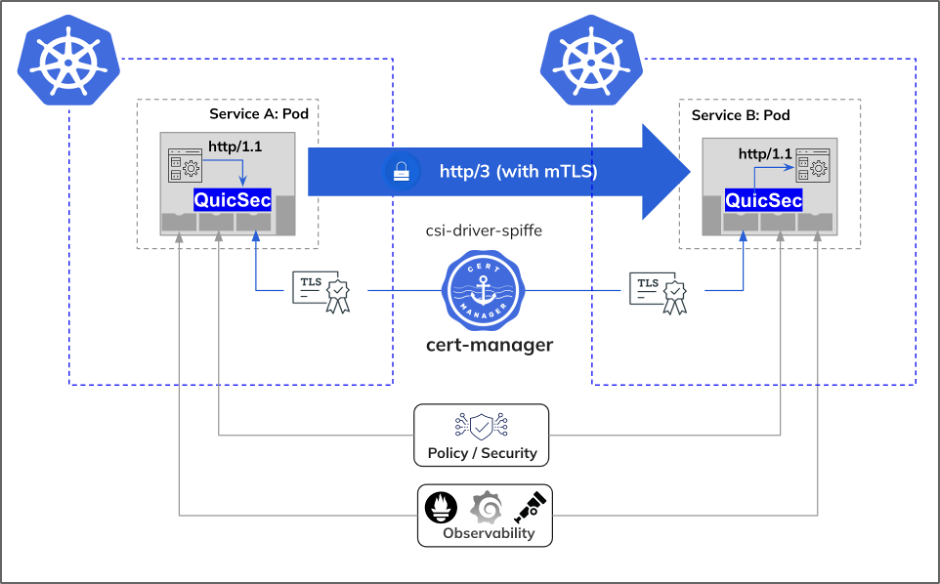
QuicSec makes the machine identity process straightforward and simple for engineering teams by using cert-manager csi-driver-spiffe to enable mTLS in lock step with X.509 certificate issuance using SPIFFE (SVID) identities created and rotated hourly. So new Kubernetes workloads can use QuicSec with HTTP/3 and automatically use the csi-driver-spiffe to provision SVIDs for applications and rely on cert-manager for automated rotation, revocation and secrets management.
By harmonizing the best and most established open source solutions with the new HTTP/3 standard, this new approach marks a significant shift in thinking and enables identity based, application-aware security. Organizations can now purposefully enable their cloud native applications with HTTP/3 and use QuicSec with cert-manager to significantly reduce operational complexity and improve security.
Connect microservices the easy way with native support for HTTP/3
For both platform and security teams, complexity can quickly become a problem for any cloud native project. With QuicSec and cert-manager, these teams can now instantly enable their applications over HTTP/3 with the inherent capability to automate TLS and mTLS secure communications. This ability significantly reduces the current complexities and extra burden involved in handling TLS for in-house application development. Security teams benefit too since they will be able to enforce TLS and machine identity authentication by default.
- For a fast insight into how QuicSec works, check out these video demos.
- Learn more at the QuicSec.io website
- Check out QuicSec on the Venafi Market Place
Attending KubeCon EU in Amsterdam?
Venafi and Pod8 will be attending KubeCon in Amsterdam next week and the cert-manager team will be showcasing the QuicSec solution at the Project Pavilion cert-manager booth. Feel free to drop by the cert-manager stand and request a demo.
Is SPIFFE now ready for mainstream production? On Tuesday April 18 Venafi will be hosting a special in-person event at a central Amsterdam location to showcase the very best initiatives on open source machine identity management and Zero Trust security. Pod8 will be present along with the Venafi CTO Matt Bates, who will explain how QuicSec is about to change the game for cloud native security. Click this link for a special invite.
Additionally, Pod8 will be presenting two talks at the Cloud Native Rejekts event titled Connecting Microservices The Easy Way and Lightweight mTLS without Proxies, Sidecars or Complexity on Sunday & Monday, April 16 & 17. Stop by to see QuicSec in action and join the community.
Cover every cluster with ease and efficiency.
Related posts
