Common security challenges using Istio
Istio, a widely used open-source service mesh solution, provides tools for traffic management, observability, and security, including mutual TLS (mTLS) for service-to-service communications. Enforcing mTLS for workload communication in Istio environments is crucial. However, without robust security governance to ensure trusted workload authentication, challenges may arise. One important challenge relates to how the default Istio setup relies on self-signed certificates using Istio’s standard Certificate Authority (CA) system, which if deployed to production will fail to meet the stringent standards for workload authentication demanded by Infosec teams. Without security governance and policy compliance to ensure workload communication is trusted, self-signed CAs in Istio can become rogue CAs. This potentially allows unauthorized actors to issue untrusted certificates, resulting in serious breaches. To mitigate these risks and prevent cyber threats from compromising the system, it is essential to replace self-signed CAs in Istio.
Firefly’s solution for Istio
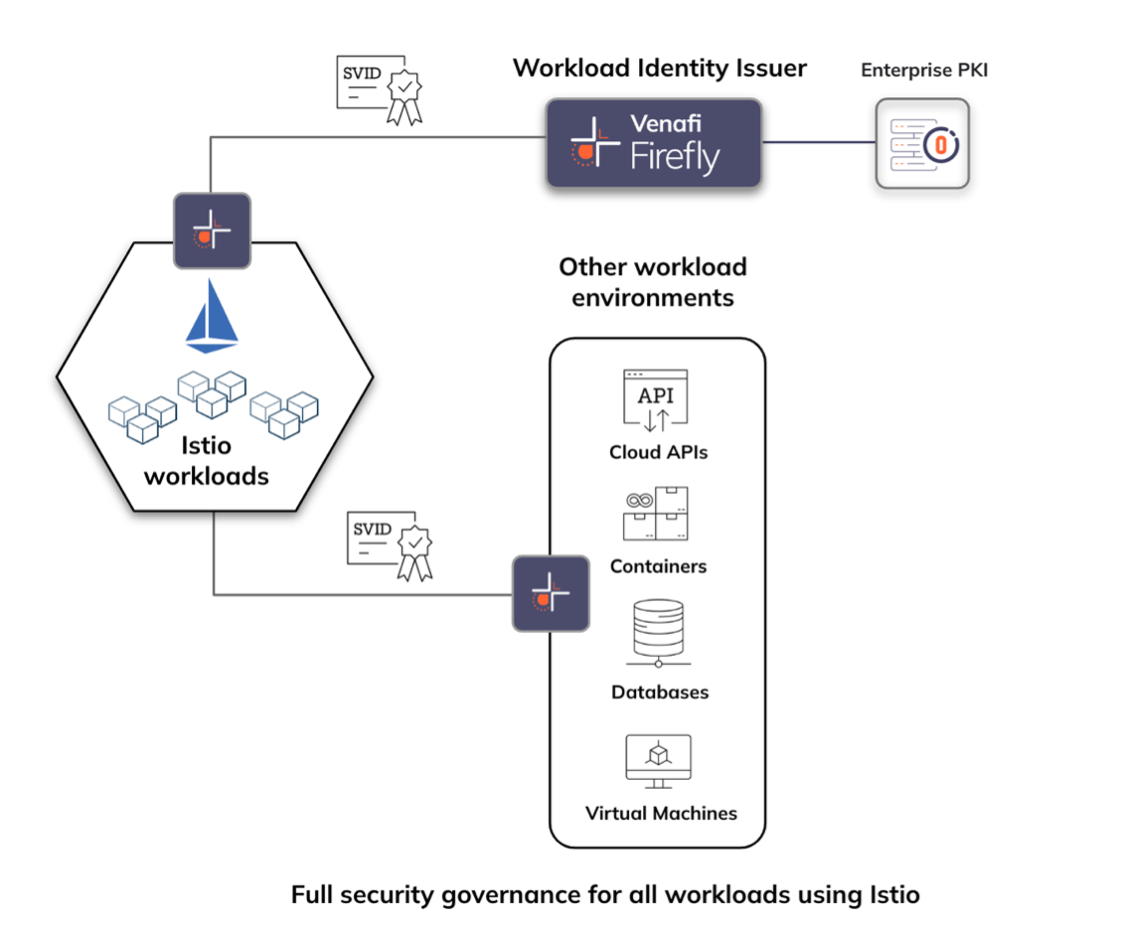
Better overall security governance is essential to prevent rogue CAs in Istio. Venafi’s Firefly removes the limitations of self-signed certificates, ensuring that all mesh traffic adheres to Infosec policies and standards for using approved PKI for all workload environments. This allows Infosec teams to enforce consistent security policies with oversight and governance for workload authentication across the service mesh which even extends to Virtual Machines (VMs) to secure workloads operating outside the mesh in non-containerized environments.
Firefly ensures robust policy control and visibility, enforcing trusted communication for all service mesh traffic. It streamlines workload authentication, making it easier for organizations to implement scalable and secure mesh environments, ensuring all mesh identities are rooted using enterprise-approved Public Key Infrastructure (PKI).
Leveraging SPIFFE workload identities
Firefly builds upon the widely-used SPIFFE workload identity framework by issuing unique SPIFFE IDs (SVIDs) to all workloads within the Istio service mesh. Istio’s inherent use of SVIDs enables mutual TLS authentication to support precise access control policies between services. Firefly ensures all SVIDs within the mesh can be verified using compliant PKI, providing the strongest foundation for secure service-to-service communication.
Full compliance and governance for workload-to-workload, and service-to-service authentication for any environment is a constant challenge for Infosec teams. Istio will operate more securely if all workload identities can be validated. Using Firefly as a trusted issuer of policy-compliant workload identities allows Infosec teams to implement a trust-root system that standardizes and strengthens the way all workloads authenticate and communicate securely using SPIFFE.
The challenge of self-signed certificates
- Self-signed CAs increase the risk of attackers impersonating legitimate services.
- Non-compliant PKI undermines the trust mechanism for secure service-to-service communication, leading to rogue CAs.
- Self-signed certificates lack the rigorous lifecycle management found in enterprise-grade solutions like Firefly.
Real-world attack vectors targeting self-signed CAs
In a real-world attack vector targeting self-signed CAs in a default Istio setup, a state actor can exploit a company's software supply chain by inserting malicious code into a widely used open-source tool. This tool, perhaps used in the form of a common Helm Chart is automatically deployed to a Kubernetes cluster into its own namespace, with access to all Kubernetes secrets and uses a "phone-home" functionality to extract and scan an Istio self-signed CA to an external attacker-controlled server. The attacker may then create fake SPIFFE workload identities (SVIDs) to impersonate legitimate Kubernetes workloads, bypassing networking policies and gaining undetected access within the cluster's trust framework. This allows the attacker to query and access sensitive data, performing unauthorized actions. Using Venafi Firefly to replace Istio's default CAs mitigates this threat by enforcing strict certificate issuance policies and robust security controls, ensuring the authenticity of certificates and workload identities. It ensures compliant certificate issuance policies with security controls that validate and monitor the authenticity of certificates and significantly reduces the level of overall compromise that this type of Man In The Middle can inflict.
Firefly security benefits
Multi-cloud Istio trust domains
Firefly seamlessly authenticates multi-cloud mesh traffic, allowing Infosec teams to establish Istio trust domains without relying on individual cloud provider CA solutions, which can be highly complex and costly.
Compliant workload authentication
Firefly ensures that service-to-service communications within the Istio service mesh are secured with a trust root system for all workload identities using a compliant CA solution for mutual TLS.
Firefly operational benefits
Resilience to attacks and outages
By replacing untrusted self-signed certificates with policy-compliant certificates issued by a trusted identity issuer, Firefly ensures secure and scalable operations for mesh environments.
Kubernetes zero trust environments
Firefly aligns with Kubernetes zero trust security models by ensuring that service mesh traffic remains compliant with enterprise security policies. This is achieved by using workload identity to implement strict access and verification controls for workloads.
Simplified secrets management
Firefly reduces complexity in secrets management by bootstrapping ephemeral trust anchors for issuing short-lived identities for mesh workloads. This improves threat prevention in high-scale Istio mesh environments.
Post-quantum readiness
Firefly implements a trust system for workload authentication with operational readiness to dynamically support post-quantum (PQC) encryption standards.

Cloud Native Machine Identity Health Check
Securing Istio trust domains using mutual TLS with cert-manager
Firefly integrates directly with cert-manager, the widely popular open-source tool used by platform engineering teams to automate certificate management in Kubernetes clusters. By leveraging cert-manager’s Istio components, Firefly mints SPIFFE identities (SVIDs), ensuring that all traffic within the service mesh adheres to Infosec policies for compliant PKI. This improves security, operational reliability, and threat management in Istio mesh environments that are scaling across multiple clusters.
Infosec teams can significantly reduce complexity and cost by using Firefly to consolidate all mesh authentication and identity issuance onto a single Venafi solution. Firefly’s lightweight design supports using ephemeral identities to replace stored secrets inside clusters, while also supporting hardened storage environments using Hardware Security Modules (HSMs) if required.
Replace rogue CAs in Istio using Firefly
Venafi Firefly ensures secure, compliant communication between services across Kubernetes clusters, Istio service mesh domains, public clouds, and data centers. It provides a trusted root system for workload communication, directly addressing risks from untrusted CAs and delivers governance for Infosec teams. To get into more detail with this subject you can download a technical brief here to share with your team. Also, to find out how you can fully deploy Istio and enable full governance for authenticating workloads using mTLS across any type of environment, reach out to us here to set-up a discussion.
