HTTPS and TLS/SSL are actually quite similar. They are used together, but not exactly the same. HTTPS (Hypertext Transfer Protocol Secure) occurs when sites are properly secured with TLS/SSL security certificates. To clarify further, HTTPS is a standard Internet protocol that makes sure that online data is encrypted. It’s a more advanced and secure version of the previous HTTP protocol.
Originally, Secure Socket Layer (SSL) put the “s” in HTTPS as the “secure” part of the HTTPS protocol that performs the encryption of the data. But SSL has now been replaced by Transport Layer Security (TLS), which is an updated, more secure version of SSL.

TLS Machine Identity Management for Dummies
What is TLS/SSL?
TLS is the newer cryptographic protocol that replaced SSL as the means of providing communications security over a computer network. The TLS protocol is widely used in securing HTTPS to provide privacy, integrity and authenticity of data as it travels between two or more communicating computer applications.
TLS uses a handshake process to authenticate authorized devices to communicate securely over the Internet. TLS also ensures that data is only available to authorized users and prevents hackers from seeing or stealing any data transferred, including personal or financial data.
The TLS protocol secures communications by using asymmetric public key infrastructure (PKI). This type of PKI uses two different keys to encrypt communications between two parties:
- Private key: Controlled by the website owner, the private key lives on a web server and is used to decrypt information encrypted by the public key.
- Public key: Available to everyone who wants to interact with the server in a way that’s secure, the public key encrypts data in a way that can only be decrypted by the private key.
HTTPS uses the TLS encryption protocol to encrypt communications. It’s the standard technology for securing an internet connection by encrypting data sent between a website and a browser or between two servers.
What is HTTPS?
HTTPS represents the secure version of HTTP, the key protocol for transferring data between a web browser and a website. HTTPS improves security by incorporating an extra layer of encryption, which is important when users share sensitive information, such as logging into banking services, email accounts, or health insurance platforms.
When a website is protected by an SSL/TLS certificate, the URL displays 'HTTPS'. Users can inspect the certificate details, including the issuer and the registered business name of the website owner, by clicking on the lock icon in the browser's address bar.
According to Cloudflare, “Any website, especially those that require login credentials, should use HTTPS. In modern web browsers such as Chrome, websites that do not use HTTPS are marked differently than those that are. Look for a padlock in the URL bar to signify the webpage is secure. Web browsers take HTTPS seriously; Google Chrome and other browsers flag all non-HTTPS websites as not secure.”
TLS vs HTTPS: The Differences and Similarities
HTTPS is the combination of HTTP and TLS/SSL protocols and is used to encrypt communication between a server and a browser. TLS is a cryptographic protocol that ensures secure and encrypted communication over the internet. Here’s how they compare.
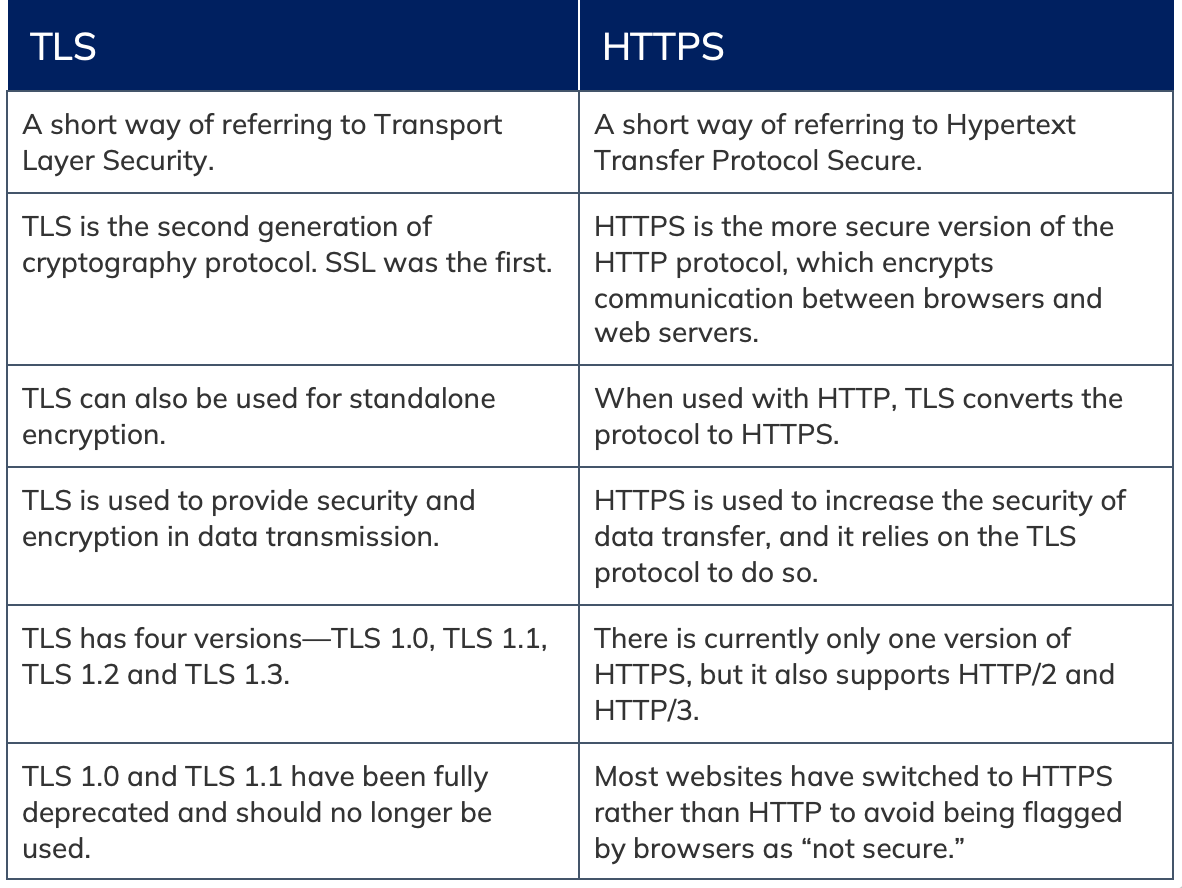
Figure 1: Comparing TLS and HTTPS
Keep your site secured
Adoption of HTTPS and TLS/SSL has been so successful that now around 95% of websites run the HTTPS protocol. But that means a lot more TLS certificates, or machine identities, are being used now than ever before. According to a recent Venafi study of 1,000 CIOs, they expect their machine identity inventories to more than double to 500,000 within the coming year.
But managing that many TLS machine identities is not an easy task. If these TLS certificates are not replaced before they expire, they will cause an outage on the website or application that they are protecting. Despite the relative sophistication of many security and identity and access management programs, certificate outages remain a challenge for organizations of any size. 83% of organizations suffered a machine identity related outage during the last 12 months, with over a quarter noting that critical systems were impacted.
As Diane Garey noted in a recent blog, “You’d think with TLS machine identities, and their predecessor SSL certificates being around for the better part of 30 years now, we’d have ample time to figure out how to avoid them expiring and causing an outage.” Manual management strategies and lack of automation are the major culprits in certificate related outages.
In the Venafi study, nearly two-thirds of CIOs admitted that rather than using a comprehensive machine identity management solution, their organizations combine multiple solutions and processes, including point solutions from certificate authorities (CAs) and public cloud providers, homegrown solutions and manual processes.
This piecemeal approach does not provide an enterprise-wide view of all machine identities or provide the mechanisms needed to enforce configuration or policy requirements.
Venafi offers a Control Plane for Machine Identities that helps enterprises stop outages to applications, services and security infrastructure by providing the capabilities necessary to manage machine identities.
If you want to learn more about stopping or preventing outages, we’ve collected some best practices and materials to help you get started. And if you’d like to see for yourself how to automate discovery, self-service and machine identity management, sign up for a free 30-day trial of our TLS Protect Cloud solution today.
Get a 30 Day Free Trial of TLS Protect Cloud, Automated Certificate Management.
Related posts

2024 Machine Identity Management Summit
Help us forge a new era of cybersecurity
Looking to vulcanize your security with an identity-first strategy? Register today and save up to $100 with exclusive deals. But hurry, this sale won't last!
