Based on a relatively long string of errors made by Symantec certificate authorities (CAs), major browser makers Google and Mozilla have stated that they will revoke the trust of certificates issued by Symantec or certificates that chain to a Symantec root. That includes the widely known Thawte, VeriSign, Equifax, GeoTrust and Rapid SSL brands. Both Google and Mozilla have published timelines for this distrust, which will trigger untrusted connection errors for all impacted certificates as early as April, 2018. But sadly, Symantec’s mistakes are not all that uncommon in the industry.
As the largest issuer of extended validation (EV) certificates, perhaps Symantec’s foibles are more visible than other CAs. But Symantec is certainly not the only CA to fall prey to human error or policy failures. There are a number of ways in which CAs can inadvertently compromise the security of certificates that they issue. And this, in turn, will impact the trust of the machine identities that protect your organization.
I’ll outline the six major CA errors that can impact the trust of certificates below.
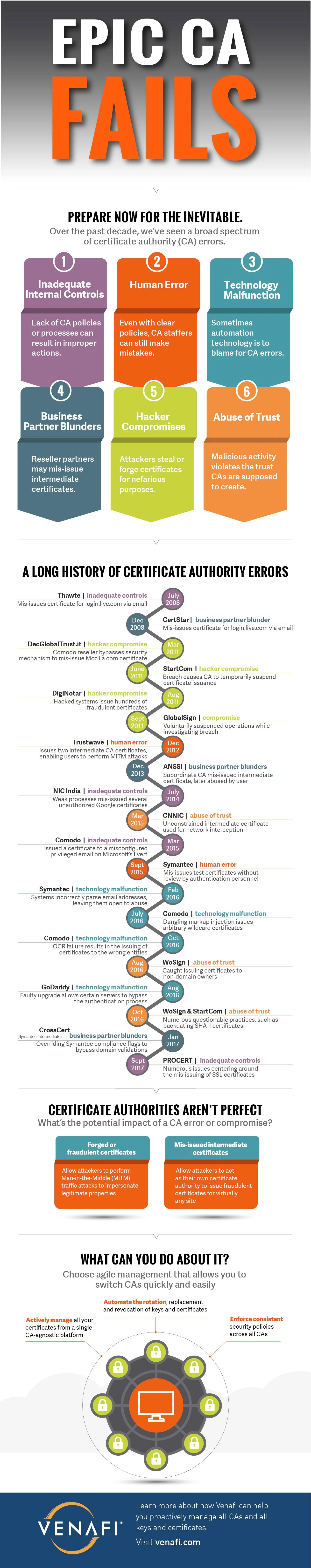
The trust model on which the internet is currently (and has been) designed has many single points of failure and each CA is one of them. Every time a CA breaks the trust we place in them, regardless whether it’s intentional or accidental, someone on the internet is harmed. And the next time it happens, it maybe you or your organization. You need to be prepared to act quickly if your certificates are impacted in any way.
In the next post, we’ll talk about how to minimize the chances of your organization being impacted by a breach of CA trust.
Find out why you need machine identity management
Related blogs
