There are over 30 billion active Internet of Things (IoT) devices and that number is growing at an incredible rate. According to McKinsey, 127 new IoT devices are connected to the web every second. Every device comes with new vulnerabilities and increases the attack surface. Networks of industrial IoT machines are distributed over different organizations and geographies resulting in a complex mesh which poses a serious security problem. The root of the problem lies with the machine identities. Each device needs a strong, unique identity in order to authenticate itself and securely communicate with other devices. Only then can these many devices transfer and manage data securely.
Today, there is no standard interface to acquire IoT machine identities with MQTT (Message Queuing Telemetry Transport) and other protocols. Most often, manufacturer or IoT platform defaults are used for machine identities. The use of these defaults makes it easy for hackers to compromise the identities and trigger network disruptions with far-reaching effects. Similar vulnerabilities occur when machine identities expire or are not properly managed. On top of that, even if strong machine identities are created and updated, device authentication—the ability to verify its identity—remains elusive.

CIO Study: Outages Escalating with Massive Growth in Machine Identities
For the IoT to be successful, a security solution is needed that provides all IoT devices with secure machine identities that are verifiable and enables authentication of these identifies throughout the entire life cycle of the devices. Furthermore, this solution needs to be IoT-aware, providing the visibility, intelligence and automation required to deal with all the risks that IoT devices present.
Device identities can be managed by device certificates in a strong Public Key Infrastructure (PKI). Using PKI, each device identity is built from a strong public-private cryptographic key pair that is unique to the chip. While the public part can be shared to establish the identity, the private part—used to authenticate the identity—must be kept secret at all times and should be bound to the device. A very convenient way to do this is by using Physical Unclonable Functions or PUFs. For example, the SRAM PUF solutions from Intrinsic ID employ physical properties unique to the chip and can be used as a root of trust to create the cryptographic key pair. Using a PUF is a very secure way to keep a private key secret since the key is never stored but regenerated from the PUF when needed.
In order to accelerate the deployment of unclonable device identities based on SRAM PUF technology, Intrinsic ID has created an interface between the Venafi platform and the Intrinsic ID key provisioning tool. Semiconductor vendors and OEMs can use this combined solution to provision devices that deploy the Intrinsic ID SRAM PUF products for secure key storage and management as indicated in the figure below. Intrinsic ID BK embedded software IP is used to generate that strong and unique cryptographic key pair from the unique physical properties of the SRAM in the chip in the device. The public key is then exported as the Certificate Signing Request (CSR) to the Venafi backend to turn it into a digital certificate. The certificate is retrieved from the Venafi backend and installed on the device. The device now has all the credentials needed to establish a secure communication with the cloud.
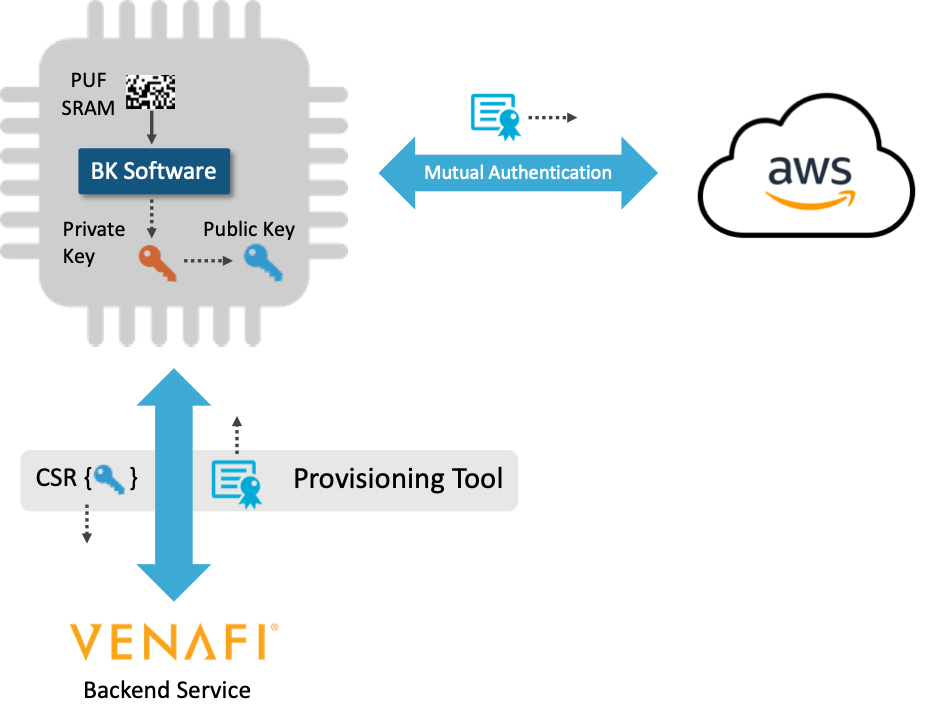
Upon connection with the cloud (e.g. with the Amazon cloud as indicated on the figure), the device will use the certificate to show its identity. Based on the certificate, the cloud can verify the identity of the IoT device. The device will need its private (secret) key in an authentication protocol with the cloud to prove its identity. The authenticity of the device can now be guaranteed since no other party knows—or has access to—the private key. The private key is reconstructed on the fly from the chip’s SRAM PUF.
Venafi’s Control Plane for Machine Identities is used for the logging, monitoring and lifecycle management of the device. The Venafi Platform provides the visibility and intelligence for machine identity management and inventory and can be easily scaled up for large numbers. Any Certificate Authority (CA) can be used in this process and the system is agnostic to the CA used. By setting up the system this way, we are able to track and monitor certificate status in an automated way. Once the certificate is generated the setup can be connected to the cloud network. Venafi provides a complete certificate lifecycle support—including revocation and renewal of device certificates.
Intrinsic ID SRAM PUF technology provides every IoT device with a strong and device-unique cryptographic key pair, which forms the basis of the device’s digital identity. This digital identity is solidly established by having a trusted party generate a digital certificate based in the unique public key of the device certificate generation and management are efficiently controlled and scaled to large number of devices by leveraging the power of the Venafi Platform backend. The result is a highly secure, dependable solution for securing and managing machine identities.
Intrinsic ID is part of the Machine Identity Management Development Fund. This vast ecosystem of partners and out-of-the-box integrations helps Venafi customers manage all machine identities and orchestrate them throughout their security infrastructure. Want to learn more? Visit Intrinsic ID on the Venafi Marketplace.
Get a 30 Day Free Trial of TLS Protect Cloud, Automated Certificate Management.
Related posts
