Venafi is a strong proponent of and is always encouraging people to move to HTTPS for several reasons such as performance benefits, security, and even SEO advantages. While we constantly use the acronyms HTTP and HTTPS, it is equally important to understand the basics of how they work and what their differences are.
HTTP vs HTTPS in a nutshell
Understanding the distinction between HTTP and HTTPS is crucial in grasping web security fundamentals. While HTTP serves as a protocol for transmitting data across the world wide web, HTTPS adds a critical layer of security to this process. The primary difference lies in the encryption that HTTPS provides. Employing TLS (previously SSL), HTTPS encrypts standard HTTP requests and responses, significantly enhancing the security of data exchanges. This extra layer of protection is easily identifiable in a website's URL: if it starts with HTTP://, it is using HTTP, but if it starts with HTTPS://, it signifies the added security offered by HTTPS. Hence, HTTPS offers a more secure option for data transmission on the internet compared to HTTP.

Figure 1: HTTP vs HTTPS. Image source: Cloudflare
What is HTTP?
The Hypertext Transfer Protocol, better known as HTTP, is the cornerstone of data communication on the World Wide Web. It's a well-structured protocol—a set of defined rules and syntax—that governs the transfer of data over networked environments. HTTP is primarily responsible for loading webpages through hypertext links. Moreover, it facilitates various forms of data transfer on the internet, including delivering website content and making API calls. Operating as an application layer protocol, HTTP sits atop other network protocol layers, enhancing interoperability. The protocol's functionality hinges on a request-response model: a client machine initiates a request, which is answered by a server response. Thus, HTTP is more than just a protocol—it's the critical infrastructure that powers data exchange on the internet.

TLS Machine Identity Management for Dummies
What is an HTTP request and how does it work?
There are two main kinds of HTTP messages: requests and responses. HTTP requests are generated by a user's browser as the user interacts with web properties. For example, if a user clicks on a hyperlink, the browser will send a series of "HTTP GET" requests for the content that appears on that page. These HTTP requests go to either an origin server or a proxy caching server, and that server will generate an HTTP response. HTTP responses are answers to HTTP requests.
HTTP requests and responses are sent across the Internet in plaintext. The problem is that anyone monitoring the connection can read these plaintexts. This is especially an issue when users submit sensitive data via a website or a web application. This could be a password, a credit card number, or any other data typed into a form. Essentially, a malicious actor can just read the text in the request or the response and know exactly what information someone is asking for, sending, or receiving, and even manipulate the communication.
The answer to the above security problem is HTTPS.
What is HTTPS?
HTTPS is the acronym for Hypertext Transfer Protocol Secure (also known as HTTP over TLS or HTTP over SSL). HTTPS is used to encrypt HTTP requests and responses via TLS (or SSL), ensuring that instead of plaintext, an attacker only sees a series of seemingly random characters. This means that sensitive information, such as login credentials, personal data, or payment details, is protected from interception during transmission, making it significantly harder for attackers to access or tamper with the data.
TLS uses a technology called public key encryption: there are two keys, a public key and a private key. The public key is shared with client devices via the server's SSL certificate. The certificates are cryptographically signed by a Certificate Authority (CA), and each browser has a list of CAs it implicitly trusts. Any certificate signed by a CA in the trusted list is given a green padlock lock in the browser’s address bar, because it is proven to be “trusted” and belongs to that domain. Companies like Let’s Encrypt have now made the process of issuing SSL/TLS certificates free.
When a client opens a connection with a server, each machine needs a verified identity. So, the two devices use the public and private key to agree on new keys, called session keys, to encrypt further communications between them. All HTTP requests and responses are then encrypted with these session keys, so that anyone who intercepts communications can only see a random string of characters, not the plaintext.
In addition to encrypting communication, HTTPS is used for authenticating the two communicating parties. Authentication means verifying that a person or machine is who they claim to be. In HTTP, there is no verification of identity—it is based on a principle of trust. But on the modern Internet, authentication is essential.
Just like an ID card confirms a person's identity, a private key confirms server identity. When a client opens a channel with an origin server (e.g. when a user navigates to a website), possession of the private key that matches with the public key in a website's SSL certificate proves that the server is actually the legitimate host of the website. This prevents or helps block a number of attacks that are possible when there is no authentication, such as Man-in-the-middle attacks, DNS hijacking, and domain spoofing.
What is the difference between HTTP and HTTPS?
Based on the above presentation of HTTP and HTTPS, the following table presents the main differences between these two protocols.
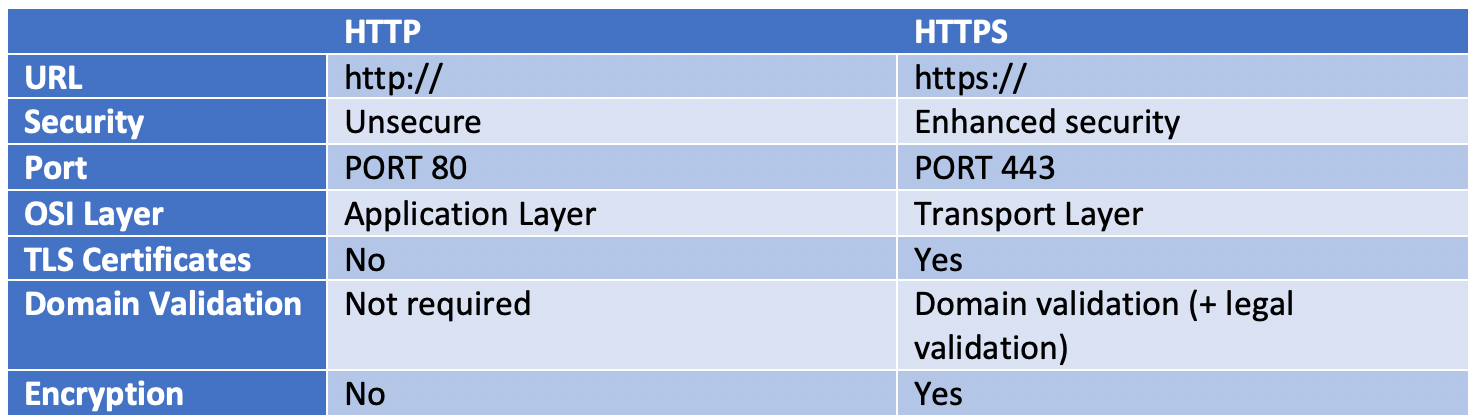
Table 1: Differences between HTTP and HTTPS are mainly to drive better security
In HTTPS, the URL starts with https://, whereas HTTP starts with http://. HTTPS offers security protections beyond those of standard HTTP, such as enhanced security, the use of TLS certificates, required domain validation, and encryption. These work in tandem to provide the better security that comes with HTTPS.
Conclusion
HTTPS comes with many advantages, both performance and, most important, security wise. All browsers are strongly encouraging users to trust only websites implementing HTTPS because this is the single measure that can help them mitigate a variety of threats and attacks.
(This post has been updated. It was originally published on September 22, 2022.)
