SSL stripping attacks, also known as SSL strip, SSL downgrade, or HTTP downgrade attacks, compromise the security of HTTPS by downgrading the connection to the more vulnerable HTTP. These attacks pose a significant cyber threat to numerous businesses. The risk is particularly high for corporate employees who frequently use open, unsecured Wi-Fi hotspots for Internet access while traveling, making them susceptible to SSL stripping attacks. In such attacks, cybercriminals infiltrate a network and position themselves as a Man-in-the-Middle (MITM), enabling them to intercept network connections. This interception technique is not limited to wireless networks; it can also be executed in wired networks if the attacker manages to access an Ethernet port.
The KRACK Attack effectively demonstrated that corporate users can’t blindly trust the medium that connects them to the internet. It also illustrates how encryption can be completely stripped away even if the site supports HTTPS.

SSL/TLS Certificates and Their Prevalence on the Dark Web
What is SSL Stripping? A bit of history
Moxie Marlinspike, an esteemed American computer security researcher, is credited with uncovering the SSL strip vulnerability. In 2009, he first brought this critical SSL flaw to light during a presentation at the Black Hat security conference. Marlinspike highlighted the gravity of exploiting this vulnerability, emphasizing its significant threat to the confidentiality of digital credentials. This attack can occur in real-time and remain unnoticed, targeting any secure website users are accessing at that moment. The process does not necessitate multiple certificates, and after completing the attack, the perpetrator can seamlessly revert victims back to their regular traffic flow, making the intrusion difficult to detect.
SSL Stripping: A bit of theory
HTTP and HTTPS are application-layer protocols in the TCP/IP model, as depicted in the accompanying figure. HTTPS distinguishes itself by using a secure tunnel, commonly referred to as SSL/TLS (Secure Socket Layer / Transport Layer Security), to transmit and receive data, thus adding the 'S' suffix to HTTPS for its secure nature.
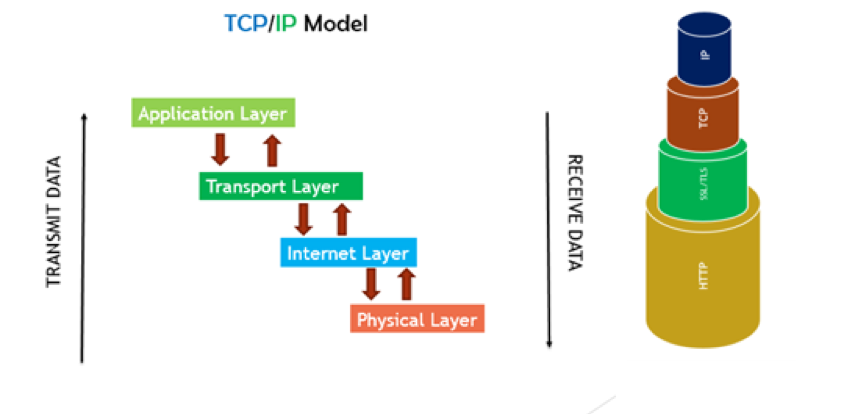
SSL/TLS functions as a robust protocol for transmitting confidential information. It's particularly employed when transferring sensitive data, such as banking details or email communications. The protocol ensures security through an encrypted connection between two entities, typically a client application and a server. This encrypted connection is widely used by browsers and web servers to establish a secure channel as needed.
The typical sequence of events in establishing a secure connection is as follows:
- The user initiates an unsecured HTTP request.
- The server responds with an HTTP message and redirects the user to a secure HTTPS connection.
- The user then sends a secure HTTPS request, initiating a secure session.
This method effectively ensures both privacy and integrity. It goes beyond mere encryption of messages; it also ensures that the messages are not altered during transmission
This procedure offers a solid assurance of privacy and integrity. This means that it's not just about encrypting the messages we send; it also involves ensuring that the messages we receive remain unaltered during transmission.
How an SSL stripping attack works
To execute an SSL stripping attack, an attacker intercepts the transition from HTTP to HTTPS. They do this by capturing a user's request to the server during the protocol redirection. The attacker then sets up a secure HTTPS connection with the server on one end and an unsecured HTTP connection with the user on the other, effectively positioning themselves as a "bridge" between the two.
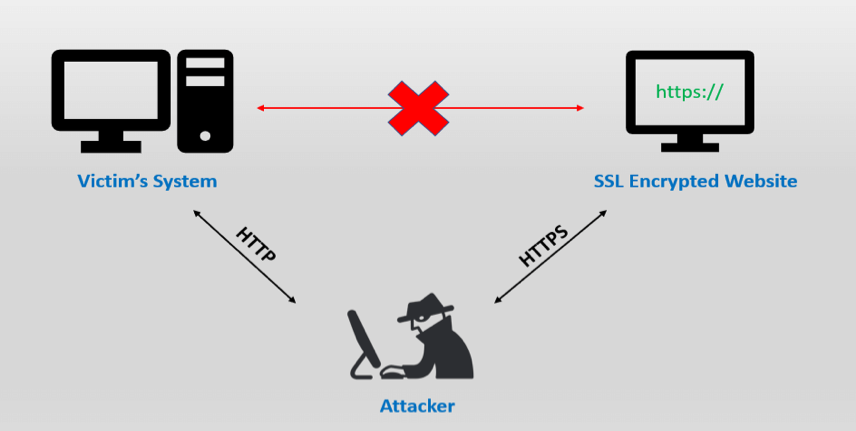
The SSL strip technique deceives both the browser and the server of a website by exploiting the common way users access SSL-secured sites. Typically, users either follow a 302 redirect from a non-SSL page or click a link on a non-SSL site to reach an SSL-secured page. For example, if a user intends to make a purchase and enters www.buyme.com in their browser, their request initially reaches the attacker's system. The attacker then relays this request to the actual server of the online store, which responds with the secure HTTPS payment page, such as https://www.buyme.com. At this juncture, the attacker manipulates the secure page, converting it from HTTPS to HTTP, and sends this modified version back to the user’s browser. Consequently, the browser gets redirected to an unsecured version, http://www.buyme.com. From this point, all data entered by the user is transmitted in unencrypted, plain text, allowing the attacker to easily intercept it. Simultaneously, the website’s server remains under the impression that it has established a secure connection, but in reality, this connection is with the attacker's system, not the user’s.
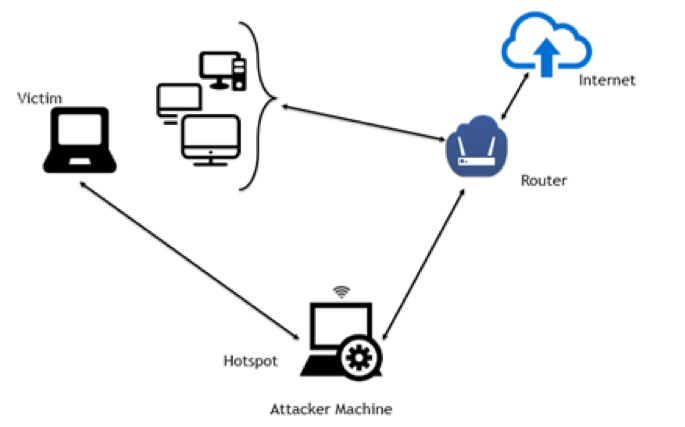
Why are open Wi-Fi hotspots dangerous?
SSL strip attacks can be implemented in a number of ways. The most common method is by creating a hotspot and allowing the victims to connect to it. Attackers often create counterfeit Wi-Fi hotspots with names closely resembling those of legitimate ones, such as using “Starbucks Coffee” in place of “Starbucks”. Unsuspecting users may connect to these deceitful hotspots. When a user attempts to access a server, the attacker, leveraging their control over the hotspot, launches an attack on the user's connection.nnect to the server, the attacker uses his control over the hotspot and attacks the user.
What is the threat of SSL stripping attacks?
After the successful implementation of an SSL strip attack, the victim’s information is transferred in plain text format and can be easily intercepted by anyone, including the attacker. This results in a breach in the integrity and confidentiality of personal identifiable information (PII) such as login credentials, bank accounts, sensitive business data, etc. Hence the threat of this vulnerability is easily understood and may have varying implications to your digital presence. Your business relies on encrypted communications to transact securely across the edge to the endpoint. But what if you can’t trust the identifying certificates on each end of the channel? Without this trust, you can’t engage in e-commerce web transactions and online banking that your consumers now rely on without having a second thought about security.
SSL stripping attacks can work only on websites that encrypt only their login page. Hence, websites that use both HTTP and HTTPS in their setup are vulnerable to SSL stripping attacks. The question to be answered now is this: what can we do to secure ourselves against this threat? Is the adoption of HTTPS and the Chrome updates a panacea?
Enable SSL sitewide at all websites
To mitigate this threat, financial institutions and technology firms have already enabled HTTPS on a site-wide basis. Enabling HTTPS encrypts the connection between a browser and the website, thereby securing sensitive data transmissions. Therefore it makes perfect sense for banks and high-profile technology firms to enable HTTPS on their dynamic websites because of the transaction of important and sensitive information.
We also have to realize that it is of equal importance to enable HTTPS across static websites, even if there aren’t any sensitive data transactions. A lot of corporations purchase an SSL certificate and they only configure the pages to be served over HTTPS that require a user to transmit personal information, such as login screens and checkout pages. That’s not a good way to operate.
Because of the abstract nature of internet connections, people think that a connection to a static website is secure over HTTP. However, the traffic travels through many points to get from your browser to a website. HTTP is insecure and allows anyone to manipulate traffic at any point between a laptop and a website. Attackers can intercept a lot of information by manipulating traffic on a static website protected only by HTTP. Some of it can be relatively harmless but other abuses are much more serious. But none of these abuses are possible if a site is protected by HTTPS. If there is any problem, web browsers like Chrome and Firefox display a message that warns visitors that they cannot verify the site’s TLS certificate.
Benefits of enabling SSL sitewide
So here is the first benefit for organizations. Trust. Encryption is like multifactor and security of the end user, but it also means that users can place greater trust in a website’s safety and authenticity. SSL/TLS is a solid way to endorse just how safe your platform is, adding a touch of professionalism to any site using it.
In addition, enabling HTTPS on a site-wide basis maintains compliance with all data privacy regulations, such as GDPR or NIST SP 800-122. Especially, GDPR clearly states that organizations must be able to provide “sufficient guarantees to implement appropriate technical and organizational measures” to ensure that processing of personal data will comply with the GDPR and that data subjects’ rights are protected. It’s a win-win situation.
In 2014, when browsers were still encouraging rather than mandating SSL, Google declared that HTTPS would be a factor in its search ranking algorithm. Fast forward to 2017, experts believe that SSL implementation can give websites a boost of up to 5% in search rankings.
Consider what happens when HTTPS becomes widespread. Once everyone adopts it, the ranking boost essentially becomes the norm. The advantage then shifts: it's no longer about gaining a benefit for having HTTPS, but rather about avoiding a penalty for not having it. If everyone else is ranking 5% higher due to HTTPS, not having it puts you at a disadvantage.
Here's the catch: only pages configured with HTTPS benefit from this boost. So, if large parts of your website remain unencrypted, they're at a competitive disadvantage. Even if you have an outstanding section on your site, it will likely rank lower if it's not encrypted.
Given the crucial role of SEO in online success, embracing Always on SSL for its SEO benefits is a wise strategy, if for no other reason.
Why enable HSTS?
Besides implementing HTTPS across their entire site, companies should consider the advantages of activating HSTS (HTTP Strict Transport Security). HSTS is a web security policy mechanism designed to safeguard websites from SSL stripping attacks and cookie hijacking. It enables web servers to mandate that web browsers interact with them exclusively through secure HTTPS connections, prohibiting any interaction via the less secure HTTP protocol.
When a web application implements HSTS Policy, compliant browsers will automatically redirect all insecure HTTP requests to HTTPS for the specified website. Furthermore, if a man-in-the-middle attacker tries to intercept a user's traffic with an invalid certificate, HSTS prevents the user from bypassing the warning about the certificate's invalidity. With an HSTS policy in place, it becomes extremely difficult for attackers to intercept any information.
Secure SSL machine identities to prevent SSL stripping
In addition to enabling HTTPS on a site-wide basis and enforcing HSTS policy, corporations need to activate one last line of defense. They need to take proper safeguards to defend their SSL/TLS certificates against bad actors who could misuse the certificate. An important part of this process involves investing in a machine identity security solution such as Venafi Control Plane for Machine Identities that allows organizations to continuously monitor their digital certificates for signs of abuse. Venafi Control Plane gives you the visibility you need to block a new breed of hackers who misuse keys and certificates to hide in your encrypted traffic. Plus, you’ll have what it takes to act quickly, when needed, to keep avoiding compromise or disruption caused by expired certificates.
(This post has been updated. It was originally published on July 22, 2020.)
