Computer encryption relies on cryptography, a science that has been around for as long as people have needed to keep information confidential. Cryptography plays an important role in the secure transmission and protection of data. Historically, before the advent of digital technology, governments, especially in military contexts, were the primary users of cryptography. The practice of cryptography stretches back to ancient times, with the Greeks and Romans sending covert messages by replacing letters in a way that could only be decoded with a secret key.
To transport sensitive information securely, a system must guarantee confidentiality and privacy. However, no communications system can completely block unauthorized access to transmitted data. Data tampering, which involves the intentional alteration of data via unauthorized means, is not a novel problem and is not exclusive to the digital age. Modifying information might help shield it from unauthorized viewers, ensuring that only the intended recipient can decipher it. Encryption and decryption constitute the two fundamental operations in cryptography.

TLS Machine Identity Management for Dummies
What is Encryption?
Encryption involves the sender transforming the original information into a different form, known as ciphertext, which appears as an unintelligible message that is then sent across the network. To carry out this transformation from plaintext (the original message) to ciphertext (the encrypted message), the sender uses an encryption algorithm and a key. This process is also referred to as enciphering.
Plaintext refers to the data that requires protection while being transmitted. Ciphertext is the scrambled text generated as a result of applying an encryption algorithm, using a specific key. This ciphertext, which is not itself protected, travels through the transmission channel. The encryption algorithm is a type of cryptographic algorithm that takes plaintext and an encryption key as inputs and outputs ciphertext.

What is Decryption?
Decryption reverses the encryption process to restore the message to its original form. The recipient uses a decryption algorithm and a key to convert the ciphertext back into plaintext. This process is also called deciphering.
A decryption algorithm is a mathematical formula used in the decryption process. It produces the original plaintext from any given ciphertext and decryption key, effectively serving as the inverse of the encryption algorithm.
Encryption and Decryption Keys
Keys are randomly generated strings of bits specifically crafted for encrypting and decrypting data. Depending on the cryptosystem in use—such as Symmetric Key Encryption or Asymmetric (Public-Key) Encryption—the keys for encryption and decryption may be the same or different. Each key is uniquely produced through algorithms to ensure its randomness and unpredictability. Typically, keys are created using random number generators or algorithms that simulate these generators.
A Symmetric Key system utilizes the same secret key for both encrypting plaintext and decrypting ciphertext.
An Asymmetric Key system employs a pair of keys for encryption processes. The public key is openly available to anyone, while the private key remains confidential and is only accessible to the message's recipient.
Public Key describes a component of an asymmetric encryption system that involves two distinct keys. The public key is the one used to encrypt messages intended for a recipient.
Private Key is the counterpart in an asymmetric key pair. It is the key possessed by the recipient, which enables them to decrypt messages meant specifically for them.
Key differences between Encryption and Decryption
Below are the key differences between encryption and decryption:
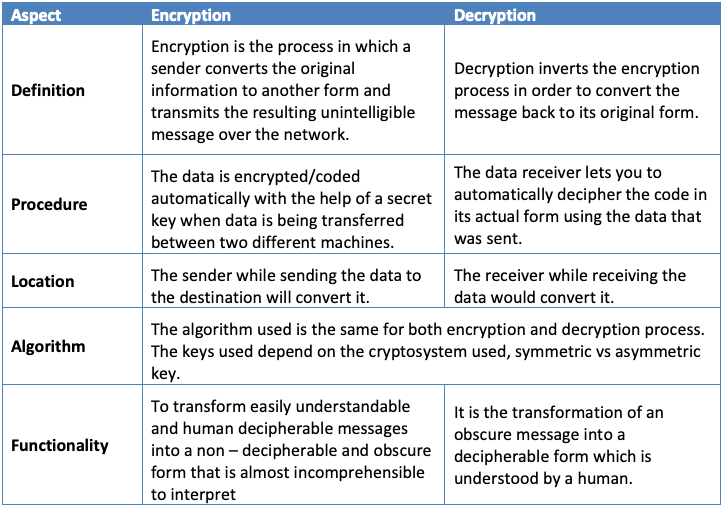
- The encryption algorithm takes an original message in a human-readable format, known as plaintext, and a key to convert it during the encryption process into an unintelligible and obscure form known as ciphertext, which cannot be easily interpreted. Conversely, during the decryption process, the decryption algorithm uses the secret key to transform the ciphertext back into a comprehensible and readable form, known as plaintext.
- Encryption is performed at the sender's end, referred to as the source, while decryption occurs at the receiver's end, known as the destination. The primary function of encryption is to convert plaintext into ciphertext, and the primary function of decryption is to revert ciphertext back to plaintext.
- Encryption automatically happens at the source when data is being sent by a machine. Pre-installed programs convert the original information into encrypted form before it is transmitted. Decryption occurs at the machine at the destination. This machine receives and converts the encrypted data back into its original form.
- Both processes are interconnected and are necessary for maintaining the confidentiality, integrity, and availability of data.
The above differences can be summarized in the following table.
Conclusion
Cryptography is critical in preserving data integrity in cyberspace. Encryption and decryption is the most common practice to protect delicate information from hackers or other threats. Encryption is the practice of converting plain text using an algorithm to prevent outsiders from accessing the information. Decryption is the practice of reversing the encrypted text to make it readable to the recipient. All of this is done with keys, public and private.
Revolutionize Your Encryption Strategy with Venafi's Zero Touch PKI Solution
Ready to simplify your encryption processes and enhance security effortlessly? Discover the power of Venafi's Zero Touch PKI solution today. Say goodbye to manual key management and hello to automated security that protects your data with ease. Take the first step towards a more secure future now!"
Get a 30 Day Free Trial of TLS Protect Cloud, Automated Certificate Management.
Related posts
- The Evolution of 256-Bit Encryption and Security Certificates
- What Is Symmetric Encryption?
- Homomorphic Encryption: What Is It and How Is It Used

2024 Machine Identity Management Summit
Help us forge a new era of cybersecurity
Looking to vulcanize your security with an identity-first strategy? Register today and save up to $100 with exclusive deals. But hurry, this sale won't last!
