Domain Name Server (DNS) poisoning or DNS spoofing is a type of cyber-attack that exploits system vulnerabilities in the domain name server to divert traffic away from legitimate servers and directs it towards fake ones.
What is DNS caching?
Before we explain how DNS poisoning works, let us remember how DNS works. Each time your browser contacts a domain name, it must contact the DNS server first. Domain Name Servers (DNS) are the Internet's equivalent of a telephone book. They maintain a directory of domain names and translate them to Internet Protocol (IP) addresses.
This is necessary because, although domain names are easy for people to remember, computers or machines access websites based on IP addresses.
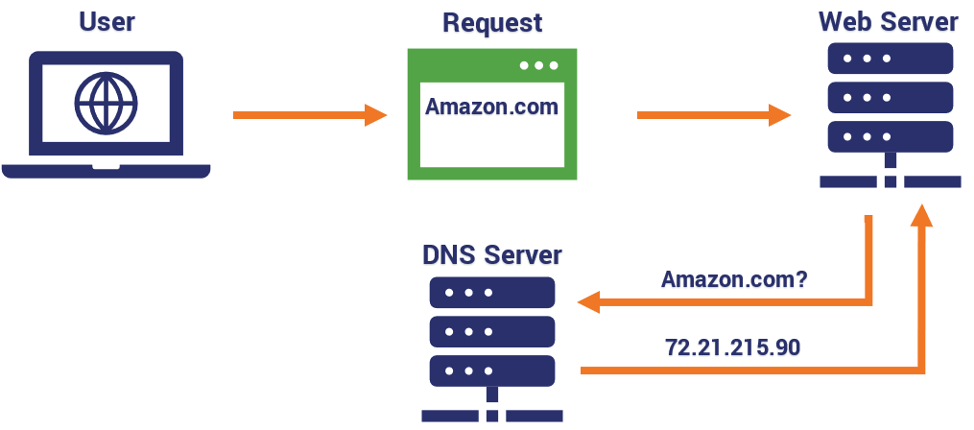
Figure 1: DNS Functioning. Source: The SSL Store
The server will then respond with at least one IP address (but usually more) for your computer to reach the domain name. Once your computer connects to the IP address, the DNS converts the domain name into an IP address that your computer can read.
Right now, your internet service provider is running multiple DNS servers, each of which caches (or saves) information from other servers as well. The Wi-Fi router you have in your home essentially acts like a DNS server as well, as it caches information from the servers of your ISP.
The DNS lookup process works like this:
- Your web browser attempts to find the IP address attached to the website you’re trying to use.
- Your operating system will first look in the computer’s memory cache. A website you’ve visited previously will likely have the IP address already stored on your computer.
- If your operating system doesn’t find the IP address on the computer, it will query the resolving name server—which is the first DNS server.
- The query passes through the DNS servers to find the matching IP address.
- The IP address is then sent back to the operating system, which sends it back to your web browser.

SSL/TLS Certificates and Their Prevalence on the Dark Web
How DNS Poisoning Works
A DNS cache is “poisoned” when the server receives an incorrect entry. To put this into perspective, it can occur when a hacker gains control over a DNS server and then changes information in it.
For instance, they may modify the information so that the DNS server would tell users to look for a certain website with the wrong address. In other words, the user would be entering the correct name of the website, but then be sent to the wrong IP address, and specifically, to a phishing website.
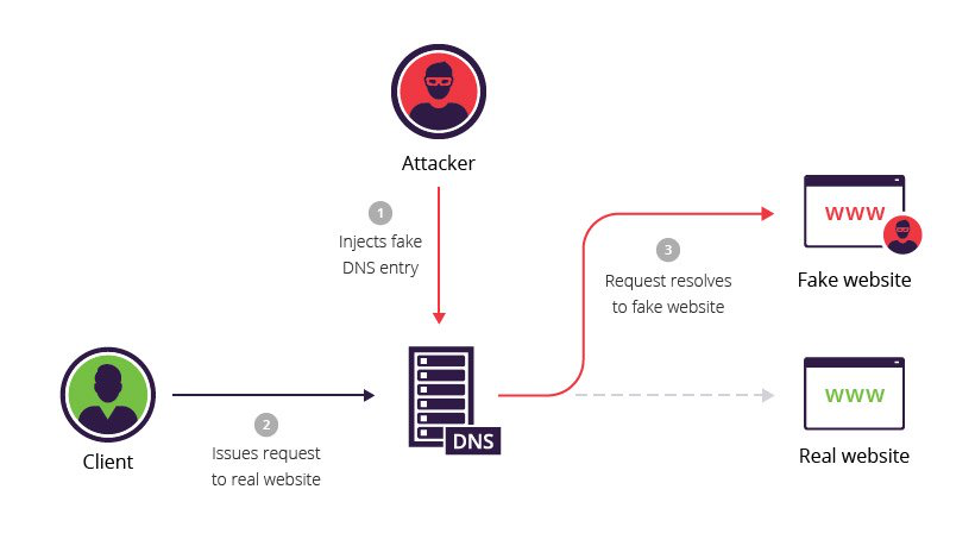
Figure 2: How DNS poisoning works. Source: imperva.com
The code for DNS cache poisoning is often found in URLs sent via spam emails. These emails attempt to frighten users into clicking on the supplied URL, which in turn infects their computer. Banner ads and images—both in emails and untrustworthy websites—can also direct users to this code. Once poisoned, a user's computer will take them to fake websites that are spoofed to look like the real thing, exposing them to risks such as spyware, keyloggers or worms.
Risks
DNS poisoning can be very dangerous because it can quickly spread from one DNS server to the next. This is accomplished when multiple internet service providers are receiving their DNS information from a hacker-controlled server, which results in the ‘poisoned’ DNS entry spreading to those ISPs to be cached. From that point on, it can spread to other DNS servers and home routers as well as computers, resulting in more and more people becoming a victim of the poisoning.
DNS poisoning poses several risks, starting with data theft. Banking websites and popular online retailers are easily spoofed, meaning any password, credit card or personal information may be compromised. Also, if spoofed sites include Internet security providers, a user's computer may be exposed to additional threats such as viruses or Trojans, because legitimate security updates will not be performed.
How to Detect DNS Poisoning
So how do you detect a DNS cache poisoning attack? The best way to do that is to monitor your DNS servers for indicators of possible attacks. Applying data security analytics to your DNS monitoring can help you identify normal DNS behavior from attacks. For example:
- A sudden increase in DNS activity from a single source about a single domain indicates a potential Birthday attack.
- An increase in DNS activity from a single source that is querying your DNS server for multiple domain names without recursion indicates an attempt to find an entry to use for poisoning.
How to Protect Against DNS Poisoning
One of the tricky aspects of DNS poisoning is the difficulty in determining whether the DNS responses you receive are legitimate or not. Fortunately, there are still several measures that your organization can take to prevent such an attack from happening to you.
For example, one thing you should do is have your DNS servers configured to rely very little on relationships with other DNS servers. This makes it much harder for a cyber-criminal to use their DNS server to corrupt their targets. This means that your own DNS server is less likely to be corrupted, and therefore you (and everyone in your organization) are less likely to be redirected to an incorrect website.
You can also configure your DNS servers to only store data that is related specifically to the requested domain and to limit query responses to only provide information that concerns the requested domain. The idea is that the server will be set up so that required services are the only ones permitted to run. By having additional services that are not required to run on your DNS server, you greatly increase the odds of an attack happening.
You should also ensure that the most recent version of the DNS is being utilized. This is because the most recent versions use security features such as port randomization and transaction IDs that are cryptographically secure to help guard against poisoning attacks.
Probably the single most important thing you can do to protect against DNS poisoning is to use DNSSec, which is critical for avoiding DNS cache poisoning. The standard has been strengthened in recent years with features specifically designed to prevent this kind of attack. It will verify the root domain (referred to as “signing the root”) whenever an end user attempts to access a site.
Another important defense against DNS cache poisoning is to look for the company’s name in the browser’s address bar. This means the site is using an SSL/TLS certificate. This would help prevent attentive people from falling victim to a poisoning attack, because they would be aware that they should not enter their personal details into a hacker’s website. Although this is not a foolproof measure, it can be helpful when trying to determine if you’re on the right site.
Conclusion
In summary, DNS poisoning is when an attacker exploits a DNS server to send a forged DNS response that will be cached by legitimate servers. Subsequently, users who visit the corrupted domain will be sent to a new IP address that the hacker controls, which is usually a malicious phishing website where victims can be manipulated into downloading malware or submitting login or financial details. Taking the steps above will help defend your organization against DNS poisoning attacks.
What to learn more about securely managing your network? Download our TLS Machine Identity Management eBook.
Get a 30 Day Free Trial of TLS Protect Cloud, Automated Certificate Management.
Related posts
