Digital transformation, the growth of new technologies, and evolving business models have made traditional corporate digital boundaries less clear. The rise of remote work has further blurred these lines. The old security methods, which relied on a well-defined security perimeter to protect digital assets, are now less effective. We need security solutions that can handle requests for access from a wide range of locations, not just within the traditional office space.
Additionally, the increase in data breaches shows that just trusting users and systems is risky. The Zero Trust security model, which follows the principle of 'Never Trust, Always Verify', becomes essential. It continuously and rigorously verifies the identities of all users and machines, adapting to a world where work and access can happen from anywhere.
What is zero trust identity?
In a business environment where applications are delivered from the cloud to the cloud, users are located everywhere and use multiple machines to accomplish routine tasks. That means that all interactions—even those originating from employees—are inherently risky and necessitate a different approach to security.
Zero Trust Identity, as defined by the National Institute of Standards and Technology (NIST), represents a transformative approach to organizational security. This strategic principle operates on the assumption that trust should never be automatically granted, regardless of whether an entity is inside or outside the organization's network. NIST describes Zero Trust as a compilation of concepts aimed at significantly reducing uncertainty in the enforcement of precise, least privilege access decisions. This is particularly critical in environments where networks are considered potentially compromised. Zero Trust Identity focuses on continuous verification of every user's authentication and authorization, ensuring ongoing alignment with security configurations and postures, thereby effectively safeguarding applications and data from breaches.
Zero Trust is a security approach emphasizing the scrutiny of individual transactions, particularly focusing on the identities of the involved parties, both human and machine. This model mandates stringent verification of all identities, thereby shifting the authentication and authorization process closer to the endpoint. Furthermore, Zero Trust minimizes implicit trust zones and advocates for highly specific access rules. These rules aim to enforce the principle of least privilege, ensuring that each entity is granted only the minimal level of access necessary to perform its required actions.
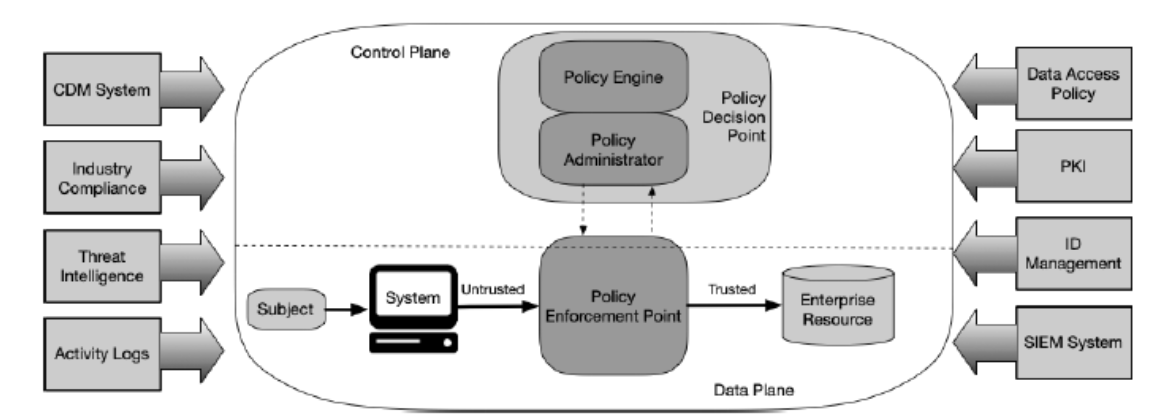
Figure 1: Identity-centric Zero Trust. Source: NIST SP 800-207
The identity-centric approach of Zero Trust architecture places a strong emphasis on both human and machine identities as the core of security policy formulation. In this framework, access controls and policies within an enterprise are established based on identity and corresponding attributes. The fundamental criterion for accessing corporate data and resources hinges on the access privileges assigned to the user or machine making the request. To enhance authentication and adopt a risk-based security strategy, access policies might also take into account additional factors, such as the device being used, the status of the asset, and various environmental conditions.

TLS Machine Identity Management for Dummies
Why do we need to validate machine identities?
The proliferation of IoT devices, the adoption of multi-cloud platforms and the widespread use of containers all require the creation and management of numerous identities to authenticate them. Businesses have become increasingly reliant on human and machine identities. As a result, identity and access management (IAM) functions have become a top security priority for all organizations. However, these identities are also attractive targets for cyber criminals. According to the Verizon 2021 Data Breach Investigations Report (DBIR), compromised credentials and identity theft are the main causes of security incidents and data breaches.
In addition to the expanding attack surface driving the need for Zero Trust, regulations such as GDPR, CCPA, PCI DSS and HIPAA enforce the principle of accountability, by requiring the strong authentication and authorization of every access request to corporate data. Finally, as the global business environment is changing and as remote working becomes the norm, it will accelerate the adoption of multiple cloud platforms. The new technology and security landscape increases the need to effectively authenticate and grant access to corporate resources based on contextual, adaptive, and dynamic decisions. All of these contribute to your Zero Trust strategy and architecture.
Don’t forget about machine identity management
When businesses begin adopting the Zero Trust model, they typically start by segmenting their network, implementing privileged access management, and adopting multi-factor authentication. However, one frequently overlooked aspect is the effective management of machine identities. This crucial step involves safeguarding associated certificates and cryptographic keys.
This overlooked area creates many gaps. Cybercriminals are prone to leveraging compromised machine identities and stolen keys to either infiltrate undetected corporate networks or masquerade their actions, by using encrypted channels. The risks associated with mismanaged machine identities are huge and can become really serious really quickly in the event of a breach.
As the number of machines, cloud workloads, containers, and IoT devices accessing corporate resources grows rapidly, issues with machine identity management are becoming a significant risk for businesses across all sectors. These issues include expired certificates, outdated cipher suites, and compromised certificates and keys, all of which can lead to serious security vulnerabilities.
The benefits of identity-based Zero Trust
Identity-based Zero Trust offers several benefits that aid in the establishment of strong access controls, enhancing security, and reducing risk. One of the key advantages of Zero Trust is its technology-agnostic nature, eliminating the need for rebuilding or replacing any part of your system's infrastructure. Once implemented, identity-based Zero Trust significantly improves risk visibility by conducting risk analysis at each access request for every entry point, rather than solely at the network level. Most crucially, by shifting the decision-making process to the level of the entity requesting resource access, Zero Trust bolsters the detection of anomalies and threats. This approach markedly enhances an organization’s overall security posture.
To protect everything properly, Zero Trust architecture should cover all resources, whether they are on-site or in the cloud. It should also check all access requests from people and machines. Applying Zero Trust to both people and machines makes this possible. For Zero Trust to work well and for businesses to get its full benefits, managing all identities, both people and machines, has to be done carefully and effectively.
Get a 30 Day Free Trial of TLS Protect Cloud, Automated Certificate Management.
Related posts

2024 Machine Identity Management Summit
Help us forge a new era of cybersecurity
Looking to vulcanize your security with an identity-first strategy? Register today and save up to $100 with exclusive deals. But hurry, this sale won't last!
