Spoofing refers to a cyberattack where an individual tries to deceive computer networks by posing as a legitimate source, using a computer, device, or network. This tactic allows cybercriminals to infiltrate computers, extracting confidential information, converting them into 'zombie' machines for malicious purposes, or initiating Denial-of-Service (DoS) attacks. Among various spoofing techniques, IP spoofing is the most common

SSL/TLS Certificates and Their Prevalence on the Dark Web
What is IP Spoofing?
IP spoofing is a technique where a hacker manipulates the source address in an IP packet's header. This makes it appear as though the packet comes from a trusted source, such as a legitimate computer on a network. The goal is often to hide the sender's identity or to impersonate another system, thereby deceiving security measures and making network traffic difficult to trace. This manipulation happens at the network level, often without any obvious signs of tampering.
Before discussing how it works, let us refresh our memory on how data is transmitted over the internet.
IP Packet Headers
When data is sent over the internet, it's split into several smaller pieces called packets. These packets are sent separately and then put back together when they reach their destination. Every packet includes an IP header, which holds details about it, such as the IP address of the sender (source) and the IP address of the receiver (destination).
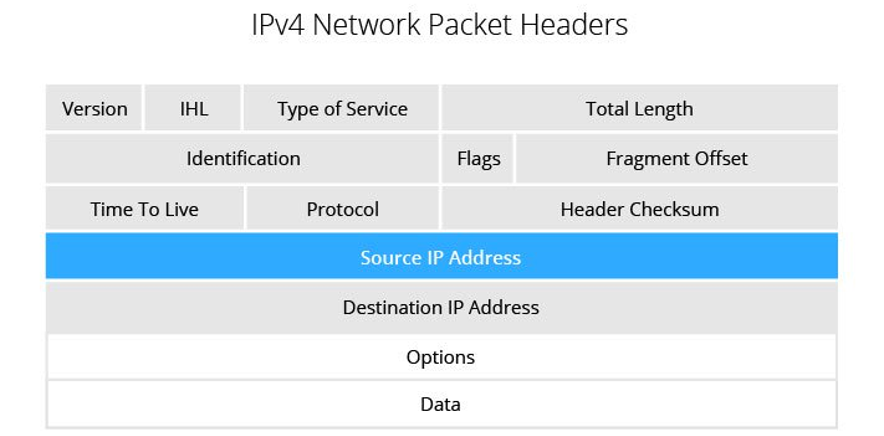
Figure 1: IPv4 Packet Headers. Source: imperva.com
How does IP spoofing work?
IP address spoofing involves altering the Source IP header information, often using random numbers, to either hide the identity of the sender or to initiate a DDoS (Distributed Denial of Service) attack. The main goal is to deceive the recipient's computer system into believing that the packet originates from a reliable source, like a computer within a trusted network, prompting it to accept the packet. This type of spoofing happens at the network level, making it difficult to detect any external signs of interference.
IP Spoofing can be compared to someone sending a package with a fake return address. If the recipient tries to stop further packages by blocking the fake address, it won't be effective, as the sender can easily change this address. Similarly, if the recipient responds to the package, their reply will be sent to an incorrect address, not reaching the actual sender.
Spoofing packet addresses is a key weakness that many DDoS (Distributed Denial of Service) attacks exploit. In these attacks, the perpetrators often use spoofing to flood a target with traffic, while hiding where it's coming from, making it hard to stop the attack. If the source IP address in these attacks is fake and keeps changing, it becomes very challenging to block these harmful requests.
IP spoofing complicates the task for law enforcement and cybersecurity experts in identifying the attackers. This difficulty arises because these attacks often utilize widespread botnets, which are networks of hijacked computers. Each botnet can have thousands of computers, each capable of mimicking various source IP addresses. Consequently, tracking the origins of such automated attacks becomes a challenging endeavor.
An alternate method involves using a multitude of computers to dispatch messages with an identical, forged source IP address to numerous recipients. The receivers of these messages, in turn, automatically send back acknowledgments to this falsified IP address, leading to an overload on the intended target server.
A different malicious IP spoofing technique involves a Man-in-the-Middle attack. In this attack, the hacker intercepts the communication between two computers, modifies the data packets, and then sends them on without the knowledge of either the original sender or receiver. Through this method, attackers can gather substantial amounts of private information over time, which they might use or sell.
In networks where trust among connected computers is key, IP spoofing can be employed to get around IP address-based authentication. The basic idea of this security method is straightforward: treat external entities as potential threats, but trust those within the network. However, once intruders penetrate this trusted zone, they can easily navigate the system and manipulate IP addresses. Given this weakness, relying solely on basic authentication is inadequate. Instead, stronger security measures are needed, like multi-factor authentication, which includes adaptive authentication and the utilization of machine identities.
How to prevent IP spoofing - Detecting and preventing IP spoofers
Organizations can implement several strategies to prevent spoofed packets from entering their networks:
- Regularly monitor network activities for any unusual patterns.
- Install packet filtering technologies that can identify discrepancies, such as inbound packets whose source IP addresses do not align with the organization's network.
- Apply stringent verification processes for all remote access, including systems within the enterprise's internal network, to avoid accepting spoofed packets, particularly from attackers who have compromised other systems in the network.
- Authenticate the IP addresses of incoming IP packets.
- Use a network attack blocker to provide an additional layer of security.
Web designers are advised to transition websites to IPv6, the latest internet protocol version. Unlike IPv4, IPv6 enhances security by integrating encryption and authentication, making IP spoofing more difficult. Despite these advantages, a significant portion of global internet traffic still relies on IPv4. According to the Seattle Internet Exchange's statistics on IPv6 traffic, only about 5% of internet traffic has shifted to this newer and more secure protocol.
Another option to consider is the use of network edge devices, such as firewalls, configured to support packet filtering to detect inconsistencies and reject packets with spoofed addresses. Some basic considerations include:
- Configure network devices to reject packets with private IP addresses coming from outside the enterprise perimeter (ingress filtering).
- Block internal traffic that falsely claims an external IP address as its source (egress filtering), preventing the launch of spoofing attacks from within the organization against external networks.
Finally, end-users typically cannot detect IP spoofing on their own. However, they can reduce the likelihood of falling victim to other spoofing methods. One effective way is by using secure encryption protocols, such as HTTPS, and making sure to visit websites that also employ these protocols.
Conclusion
IP spoofing is a technique cybercriminals use to mimic legitimate networks or devices, mainly for conducting DDoS and Man-In-The-Middle attacks. These attacks aim to either disrupt network services or steal sensitive information. While detecting IP spoofing is challenging, various solutions can help organizations prevent spoofed messages from entering their secure systems. The best practices include ongoing network monitoring, effective packet filtering, and robust authentication methods, which are essential tools for any security team.
(This post has been updated. It was originally published on September 8, 2020.)
Why Do You Need a Control Plane for Machine Identities?
Related posts
