Browsers are taking consecutive steps trying to protect end-users from falling prey to malicious actors. Following their decisions to promote the use of HTTPS by all websites, now they have extended those security efforts by blocking HTTP downloads.
Back in February 2020, Google announced a plan to gradually block all HTTP downloads on the Chrome browser, while Mozilla has also implemented similar policies in Firefox.
What is the danger behind HTTP downloads?
As we have written before in this blog, all major browser vendors are displaying either a textual or a visual warning when users are visiting a non-HTTPS website.
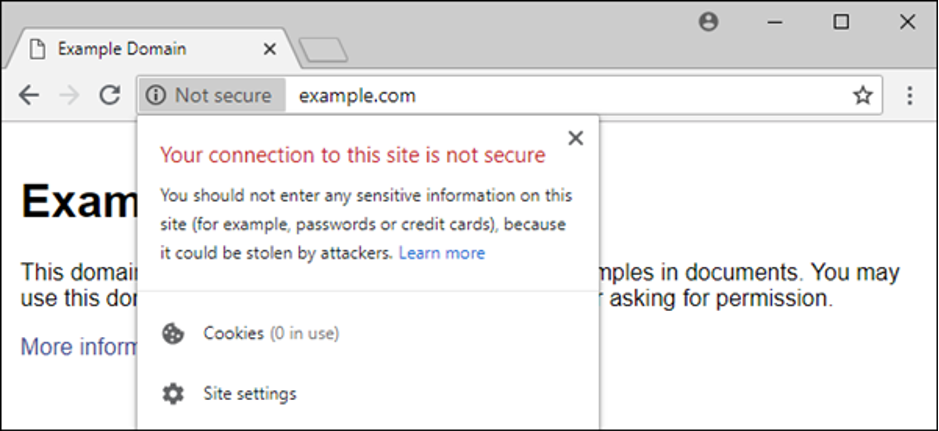
Figure 1: "Not Secure" warning displayed on a Chrome browser
This way, users are informed about the insecure connection so that they are cautious not to transmit any critical information to that website. This has played a pivotal role to drive user awareness and HTTPS adoption.
However, Google and Mozilla decided that this is not enough. Many websites, although protected by a TLS/SSL certificate, serve content downloads through HTTP connections. This is also known as mixed content.
When a user visits a webpage fully transmitted over HTTPS, such as a bank website, the connection is authenticated and encrypted, and thus safeguarded from both eavesdroppers and man-in-the-middle attacks. However, if the HTTPS page includes HTTP content, the HTTP portion can be read or modified by attackers, even though the main page is served over HTTPS. In this case, the page is only partially encrypted and even though it appears to be secure, it is not. The connection is in fact open to eavesdropping and man-in-the-middle attacks.
As Google said in a blog post “Insecurely-downloaded files are a risk to users' security and privacy. For instance, insecurely-downloaded programs can be swapped out for malware by attackers, and eavesdroppers can read users' insecurely-downloaded bank statements.” This is a hole in HTTPS security. Hence, Google and Mozilla have decided to close this gap by blocking HTTP downloads from HTTPS websites.

TLS Machine Identity Management for Dummies
What downloads are blocked and when
According to Google’s original announcement in February, the browser would begin blocking “the file types that pose the most risk to users,” starting from Chrome 81, released in March 2020. These file types include executable files such as .exe and .apk.
However, the Chrome Platform Status has an update informing users that “User-visible warnings will start in Chrome 84 (instead of Chrome 82), with warnings ramping up through Chrome 87. Final desktop blocking will be complete by Chrome 88. Android will lag one release behind, with the first user-visual warnings seen in Chrome 85.” Chrome 84 is released in August 2020.
Google’s approach to blocking mixed content is a gradual rollout that is “designed to mitigate the worst risks quickly, provide developers an opportunity to update sites, and minimize how many warnings Chrome users have to see.” The table below, adapted from Google’s original plan, displays the rollout as it currently stands.
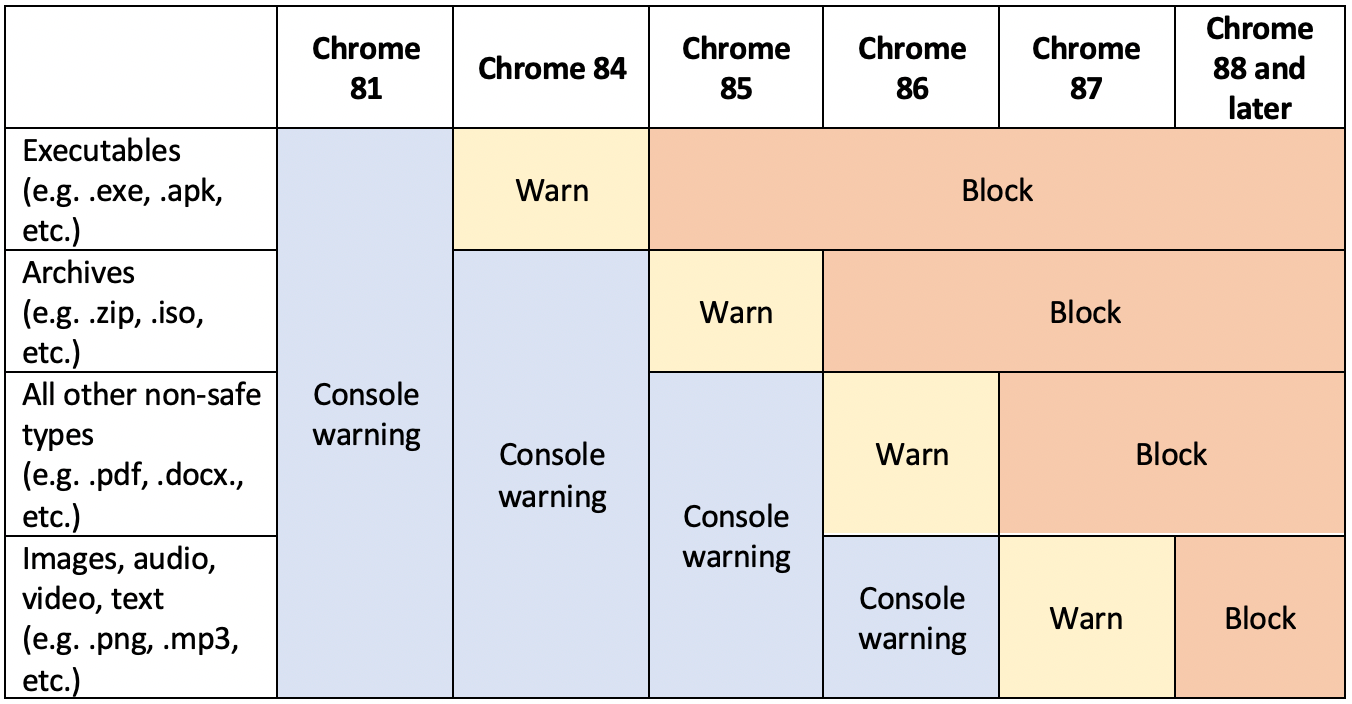
Table 1: Google's updated HTTP Block plan
Please note that if a website uses HTTP, users can still download HTTP files. This plan targets HTTPS sites that use HTTP download URLs because the browser is showing the site to be secure while the download is insecure.
When a user tries to download HTTP content that is blocked, they should get a warning like the one displayed below.
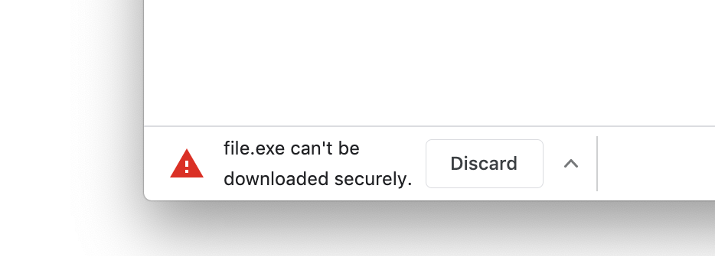
Figure 2: Potential warning on Chrome of blocked HTTP download
On the other hand, Mozilla is already implementing a mixed content block. According to the vendor, users will see a gray padlock when they visit a website where mixed content is blocked, and this site is fully served via HTTPS. If the site contains mixed content that is not blocked or it is served only through HTTP, visitors will see a gray padlock with a red line over it. Finally, a gray padlock with an orange or yellow triangle indicates that Firefox is not blocking insecure passive content, such as images. Mozilla provides instructions on how to disable the default blocking of active mixed content.

Figure 3: Mozilla padlocks for mixed content
By default, Firefox does not block mixed passive content; users will simply see a warning that the page is not fully secure. Attackers may be able to manipulate parts of the page like displaying misleading or inappropriate content, but they should not be able to steal personal data from the site.
Conclusion
Although browser vendors have been putting efforts into raising awareness and driving wider adoption of HTTPS, blocking mixed content downloads is certainly a milestone towards enhancing security and privacy on the internet.
Get a 30 Day Free Trial of TLS Protect Cloud, Automated Certificate Management.
Related posts
- Google vs. the Certificate Authorities: Are EV Certificates the Answer?
- What is HTTPS and Why Don’t More Businesses Use It?
- Google Has Increased HTTPS Use. Is That Enough?

2024 Machine Identity Management Summit
Help us forge a new era of cybersecurity
Looking to vulcanize your security with an identity-first strategy? Register today and save up to $100 with exclusive deals. But hurry, this sale won't last!
