Connected homes, self-driving cars and automated industry—just a few of the things that come to mind when you think of the Internet of Things (IoT). Behind the scenes, however, there’s still plenty of work to be done before many IoT devices can truly become a cost-effective and efficient reality.
In fact, only recently did a hacker disclose a massive list of more than 500,000 Telnet credentials for servers, home routers, and IoT "smart" devices. According to ZDNet, the list includes each device's IP address, along with a username and password for the Telnet service, and it was compiled by scanning the entire internet for devices that were exposing their Telnet port. The hacker then tried using either factory-set default usernames and passwords, or custom, but easy-to-guess, password combinations. These types of lists—called "bot lists"—are a common component of an IoT botnet operation. Hackers scan the internet to build bot lists and then use them to connect to the devices and install malware.
What will the new IoT security require?
The paradigm above highlights the importance of understanding the security issues posed by increasingly complex networks of connected IoT devices, and the need for new security solutions supporting constrained device deployments, which include embedded devices with very restricted RAM, ROM, or power budget. These security solutions should support:
- End-to-end security, across multiple intermediary devices and protocols
- Group communication with individual responses securely bound to the request
- Authentication, authorization and access control with granular and rich permission set configured by the application
The purpose of this blog is to present three recent advancements in the field of IoT security. It is important to highlight that all three solutions are the result of cooperation, either between businesses and academia (OSCORE) or between businesses (BroadKey and KeyScaler).
How can OSCORE help?
As part of the Horizon 2020 European project for the certification and security of IoT devices, Ericsson in partnership with RISE Research Institutes of Sweden have developed OSCORE (Object Security for Constrained RESTful Environments), which is a new lightweight IoT security protocol designed specifically for constrained nodes.
In July 2019, the Internet Engineering Task Force (IETF) published RFC 8613 standard which standardizes this new communication security protocol. OSCORE is defined as an extension to the Constrained Application Protocol (CoAP) and reuses CoAP's serialization of messages. According to RFC 7252, CoAP is a specialized web transfer protocol for use with constrained nodes and constrained (e.g., low-power, lossy) networks. CoAP is designed to easily interface with HTTP for integration with the Web while meeting specialized requirements such as multicast support, very low overhead, and simplicity for constrained environments.
TLS Security in CoAP
CoAP specifies the use of proxies for scalability and efficiency and references TLS for security. However, CoAP-to-CoAP, HTTP-to-CoAP, and CoAP-to-HTTP proxies require TLS to be terminated at the proxy. Therefore, the proxy not only has access to the data required for performing the intended proxy functionality, but is also able to eavesdrop on, or manipulate any part of the message payload and metadata in transit between the endpoints. The proxy can also inject, delete, or reorder packets since they are no longer protected by TLS.
The trust model where all intermediary nodes are considered trustworthy is problematic, not only from a privacy perspective, but also from a security perspective, as the intermediaries are free to delete resources on sensors and falsify commands to actuators (such as "unlock door", "start fire alarm", "raise bridge"). Even in the rare cases where all the owners of the intermediary nodes are fully trusted, attacks and data breaches make such an architecture brittle.
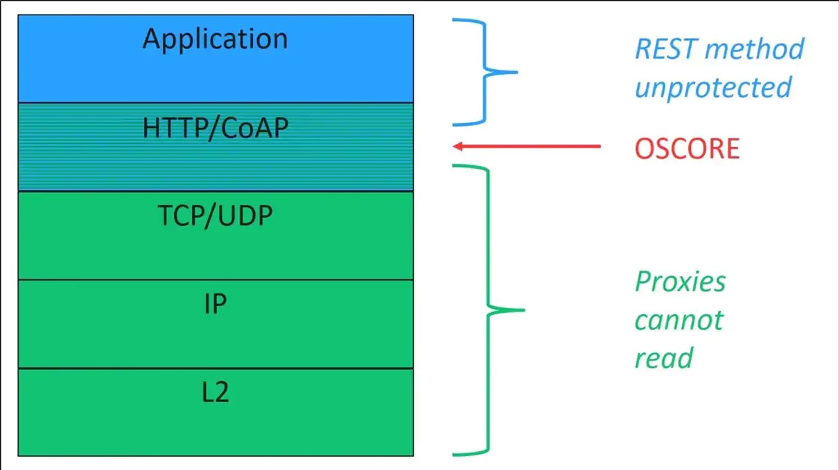
Figure 1: Abstract Layering of CoAP with OSCORE. Source: Ericsson/RISE Research Institutes of Sweden
How does it work?
OSCORE (RFC 8613) provides end-to-end protection between endpoints communicating using CoAP. OSCORE is used together with TLS to protect the application layer request and response messages between the endpoints. Therefore, OSCORE protects not only the payload containing the value associated to an indicated resource, but also the request method, the identifier of the resource, and the content format of the payload. In this way, the application relevant data and semantics of the request/response can be protected in a way which is decoupled from the transport of the messages, and it is also lightweight in terms of overhead.
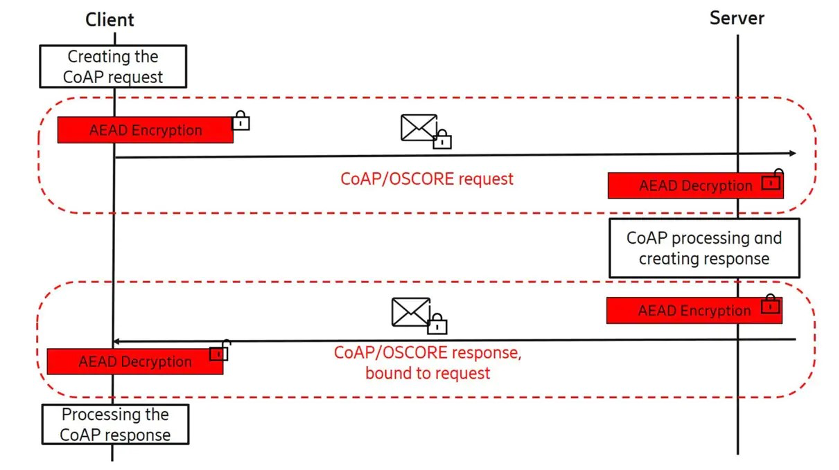
Figure 2: Protecting CoAP Messages with OSCORE. Source: Ericsson/RISE Research Institutes of Sweden
OSCORE security
OSCORE is specified to offer end-to-end encryption, integrity, replay protection, and binding of response to request. The latter is important to prevent attacks involving forwarding of a response intended for one request to another request. OSCORE requires a pre-shared master secret to derive a security context with which the communication is protected. The security context may be used for the lifetime of the device provided it is securely updated. As an alternative procedure, the master secret may be used multiple times with an initiation protocol to derive different security contexts between the same or different endpoints. The master secret may have been established out-of-band or with a key establishment protocol.
IoT machine identity lifecycle automation
The growing number of endpoints require strong identities as the foundation of trust to establish and scale robust security. Intrinsic ID’s BroadKey is a secure root key generation and management software solution for IoT security that allows device manufacturers to secure their products with an internally generated, unique identity without the need for adding a costly, security-dedicated silicon.
This solution, funded by Venafi’s Machine Identity Management Development Fund, is fully integrated with the Venafi platform, and will enable Venafi customers to ensure device authenticity through acquisition, deployment and use.
How does BroadKey implement a root of trust?
To solve security problems in IoT systems, such as authentication, product lifecycle management, reverse engineering and cloning, every device needs an unclonable identity. This consists of a secret key, a public key and a certificate. The biggest challenge is to get these credentials into the device. The figure below illustrates how this can be achieved by using BroadKey.
BroadKey creates the secret key of the unclonable identity from within, using the intrinsic randomness in uninitialized SRAM. This secret key is not stored but is dynamically regenerated from the SRAM PUF.
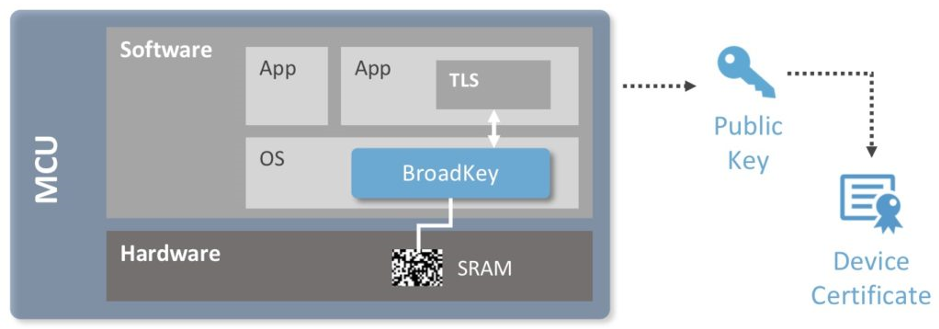
Figure 3: BroadKey in Action. Source: Intrinsic ID
At power-up, SRAM bits settle in the one or zero state in a non-deterministic way that not even the manufacturer can predict or duplicate. That’s what makes it a physical unclonable function, or PUF, which can be used as a unique “silicon fingerprint.” An SRAM PUF response is a noisy fingerprint and turning it into a high-quality and secure key vault requires further processing.
This is done with the BroadKey software IP. BroadKey reliably reconstructs the same cryptographic key under all environmental circumstances. Upon first use, called the enrollment, it generates an activation code (AC) which, in combination with the SRAM startup behavior, is used to reconstruct on demand, in real time, an intrinsic PUF key. This PUF key is never stored in flash or OTP. When it is needed later it can be reconstructed.
Completing the unclonable identity requires that a public key be generated from the secret key. And this public key can be turned into a certificate by signing it at a certificate authority. At that point the device is ready to prove its identity and set up a secure channel with another device, a server or a cloud.
Code signing for IoT
Device Authority KeyScaler delivers full end-to-end code signing and update delivery for IoT use cases, so organizations do not need to design and build their own home-grown solutions to fulfill their requirements. Again, this solution is funded by Venafi’s Machine Identity Management Development Fund and is fully integrated with the Venafi platform. Additionally, KeyScaler customers can use the Venafi Control Plane for Machine Identities as a source for certificate issuance to fully manage and protect their machine identities.
KeyScaler IoT security platform
Device Authority has introduced a new paradigm of IoT security automation that accelerates and simplifies the deployment of strong IoT security. KeyScaler helps customers simplify the process of establishing a robust, end-to-end security architecture within the IoT and deliver efficiencies at scale through security automation. Therefore, KeyScaler provides a critical foundation for establishing and maintaining trust and security for IoT devices, applications, and data generated by them to securely enable data collection, analytics, decision-making, process automation, and control systems.
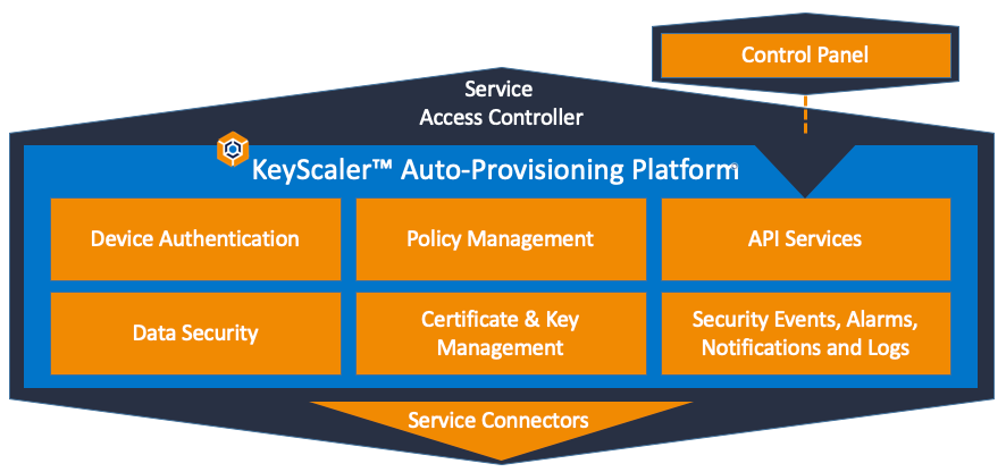
Figure 4: KeyScaler IoT Security Platform. Source: Device Authority
KeyScaler is an innovative platform that delivers comprehensive IoT security automation at scale through secure device registration and provisioning, policy-driven credential delivery and management, secure updates, and end-to-end device derived cryptography for data in transit and at rest across networks and cloud services.
What is more, KeyScaler has been designed for rapid integration and interoperability. Device Authority has developed a flexible device interface protocol that interoperates with KeyScaler for delivering automated PKI for IoT devices. Extensive REST API integration enables an abstracted interface for leveraging the security engine and system controls. The platform is highly suitable for Secure by Design architectures and follows the white listing approach for device registration.
Conclusion
Businesses and academia supported either by governmental organizations, such as the EU, or by private funds, such as Venafi’s Development Fund, are moving towards developing solutions for securing the IoT ecosystem. Venafi is proud to be part of this effort, because we strongly believe that “united we stand, divided we fall.” Such collaborations will help us develop secure-by-design and privacy-by-design IoT devices that will eliminate the attack surface and offer an added value to our society.
To date, there is no regulated protocol for machine to machine communication - in a world where Industry 4.0 and IoT are operating on even more networks and creating an ever larger attack surface. Find out what Venafi and Accessec are doing to improve IoT standards in the industry.
Get Fast, Easy, and Secure Enterprise-Grade Code Signing With Venafi!
Related posts
