The TLS protocol, primarily designed for server identity verification to the client via X.509 certificates, traditionally delegates client authentication to the application layer, aiming to prevent fraud and encrypt data transfer. However, for scenarios requiring enhanced security through client identity verification, the protocol extends its capabilities to include client-to-server authentication. This advanced security feature, known as mutual TLS (mTLS), enables mutual authentication by utilizing client-side X.509 certificates, thereby reinforcing the integrity and privacy of the communication channel between client and server.
What is mTLS (mutual TLS authentication)?
mTLS (Mutual TLS) is a security protocol that ensures both the client and server in a network connection are who they claim to be. It works by exchanging and verifying digital certificates through a secure handshake process, similar to how websites use HTTPS. This guarantees that only authorized devices can communicate, preventing unauthorized access and data breaches. It is also known as two-way authentication.
mTLS frequently plays a critical role within a Zero Trust security model, authenticating users, devices, and servers inside an organization.
Key benefits of mTLS:
- Enhanced security: Protects sensitive data from interception and tampering.
- Mutual authentication: Verifies the identities of both parties, even on internal networks.
- Compliance with regulations: Meets data privacy and security requirements in various industries.
How mTLS works:
- Client and server exchange certificates and initiate a handshake.
- Certificates are verified to ensure they are valid and trusted.
- If verification is successful, a secure encrypted connection is established.
Use cases for mTLS:
- API communication between microservices
- Secure communication between cloud applications
- Protecting sensitive data in transit
mTLS is a powerful tool for securing network communication, but it requires careful planning and implementation.
The diagram below provides a description of mTLS authentication.
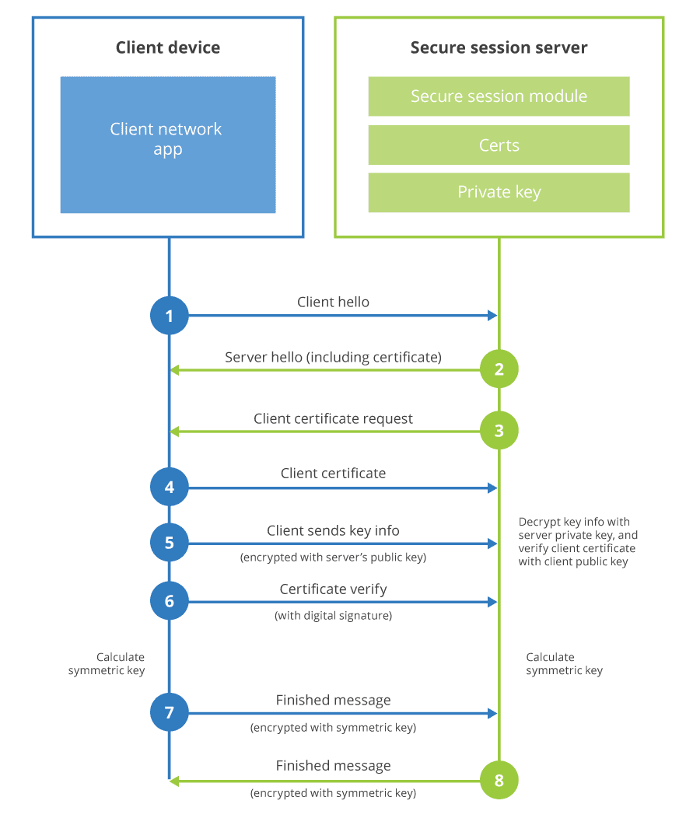
Figure 1: Mutual TLS Authentication. Source: Cloudflare

Tale of 3 Clouds eBook: How Venafi Creates Digital Transformation
The challenge of securing cloud instances
With more and more businesses migrating to the cloud and taking advantage of the benefits offered by multi-cloud platforms, the question that needs to be answered is how to secure communications with the various cloud instances. Actually, the authentication of cloud-based applications to the respective backend and middleware components seems like the Achilles' heel of application security. It is important to ensure that only approved applications or processes are granted access through APIs.
A mechanism used frequently is through single, static application logins. However, in a rapidly changing world, static logins present some security challenges.
First these logins are not updated frequently. Second, it reduces the organization’s ability to monitor and audit activities because they are grouped under the identity of the application. That problem can worsen when the application is manipulated by an attacker and the credentials are stolen or compromised. If this happens, it can prove difficult to sort out which logins are legitimate application components and which logins are unauthorized.
How mutual authentication fosters application security
The problem above can be solved by leveraging mutual TLS authentication. Just like a client (i.e. a browser) authenticates the identity of a website by validating the server certificate, so too can the server validate the client. In the case of cloud-based applications, because HTTP is the transport for the API, we can enable mutual authentication between components. In fact, we can limit the range of certificates acceptable to what is expected by requiring a specific certificate fingerprint or serial number from a particular certificate authority. Mutual authentication can be used either alone or in conjunction with a password or an identity provider.
However, employing an mTLS strategy in a cloud environment has a few dependencies. First, as we discussed beforehand, mutual TLS authentication is optional. Therefore, we must customize the API to enable TLS mutual authentication. Luckily all major PaaS vendors offer detailed step-by-step instructions on how to enable mutual authentication (see more for AWS, Azure and Google).
Advantages of mutual authentication (mTLS)
TLS mutual authentication has a few advantages from a security standpoint. Most obviously, it means relying less on insecure passwords or static secret values. Using a password or secret creates significant overhead and friction if you are to follow reasonable security practices—changing the password periodically, monitoring its usage, enforcing complexity, making sure it is appropriately protected. TLS mutual authentication removes this hassle. While setting up mutual authentication is not as straightforward as setting up a password, the amount of overhead required to manage certificates—especially if you automate the process—is far less than managing passwords.
Another advantage is that the certificate and corresponding private key are less portable than a password. While these credentials can be stolen or compromised just like any other digital credential, it requires more sophisticated skills for an attacker seeking to impersonate a remote API caller. From a monitoring and auditing point of view, using multiple certificates organizations can keep track of which component makes an API request with more granularity.
mTLS is all about effective TLS certificate management
However, these certificates are machine identities that need to be administered and managed effectively, otherwise trust will be doomed. For example, TLS certificates do expire. If you generate a certificate now and load it into your application, you should be sure to remember to reissue a new certificate when the old one expires. If you forget, your organization will face potential catastrophic outages. It is important not only to keep track of certificate expiration dates and be proactive about replacing expired certificates, but also to automate and manage effectively the whole certificate lifecycle.
Secure Your Digital Environment with Venafi TLS Protect and mTLS Authentication
Dive deeper into the world of secure communications with mTLS authentication, an essential component of a robust cybersecurity framework. In today’s fast-paced digital landscape, automating the implementation and management of mTLS within your organization is crucial for upholding the principles of a Zero Trust architecture and securing your APIs against threats. Venafi TLS Protect stands at the forefront of this challenge, offering an advanced solution that automates the intricate processes of managing and deploying mTLS. This automation ensures that users, devices, and servers are authenticated swiftly and accurately, without placing additional burdens on your IT team. Embrace the power of automation with Venafi TLS Protect and revolutionize your approach to cybersecurity.
Get a 30 Day Free Trial of TLS Protect Cloud, Automated Certificate Management.
Related posts
