To determine if a website is secured with an SSL certificate, simply check the website's URL. If it begins with "https://" instead of "http://", the site is SSL encrypted. For further verification, click on the padlock icon located in the address bar. This action reveals the website's security credentials, including detailed SSL certificate information. This quick check ensures you're browsing securely, protecting your sensitive data.
SSL protocol ensures that data on that site is secured through SSL/TLS encryption and verification. It’s important to make sure that any website where sensitive data may be transferred uses SSL. Sites that don’t are vulnerable to attack by hackers or identity thieves or may be fraudulent themselves.
Digital certificates function as digital proof of identity for people, computers, and various entities within a network. As the use of both private and public networks for transmitting sensitive information and executing essential transactions grows, there's a heightened demand for verified trust in the identities at the opposite end of these exchanges. By employing digital certificates alongside public key encryption, there's a significant improvement in authenticating devices and individuals, thereby elevating the security and confidentiality of online communications.
What is an SSL Certificate?
SSL (Secure Sockets Layer) certificates serve as digital credentials that verify a website's identity and establish a secure connection from a web server to a browser. These certificates are crucial for safeguarding data exchanges, user logins, and confidential information online. While "SSL" has become a common term for web encryption, it has been technically replaced by TLS (Transport Layer Security), which offers enhanced encryption and security features. However, the phrase "SSL certificate" continues to be popularly used to describe any certificate that secures online connections, whether it's based on the SSL or TLS protocol. Nowadays, the majority of what are referred to as "SSL certificates" actually employ the more advanced TLS encryption, indicating progress in security standards while retaining the original, well-known nomenclature.
How do I view an SSL certificate in Chrome or Firefox?
Chrome has streamlined the process for users to access a website's certificate details in just a few steps:
- Select the padlock icon located in the address bar of the website.
- In the pop-up window, choose "Certificate (Valid)."
- Review the "Valid from" dates to ensure the SSL certificate is up-to-date.
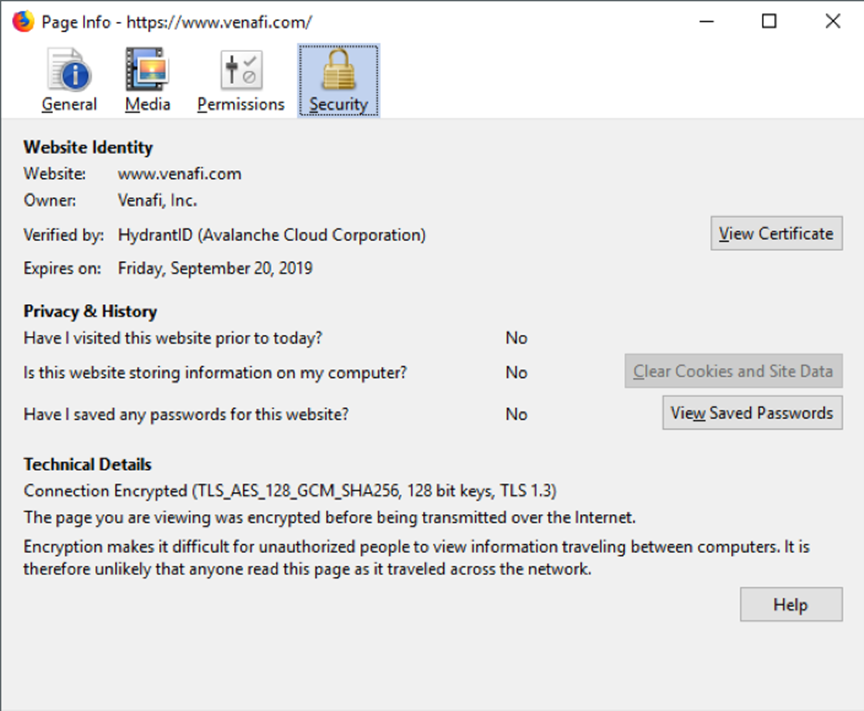
The information presented will cover the certificate's intended uses, the entity it's assigned to, the authority that issued it, and its validity period. For Extended Validation (EV) Certificates, additional details about the organization running the website are available. For other types of certificates, such as Domain Validated and Organization Validated, the display will primarily show the issuing Certificate Authority (CA) under the "Verified by:" section at the pop-up's end. For further details, users can click on the "More Information" link.
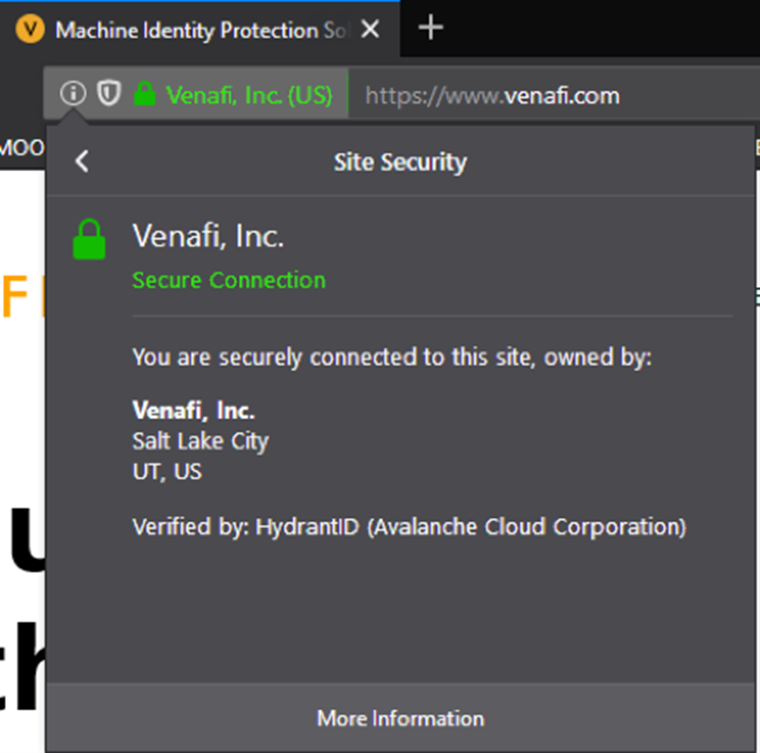
EV certificate in Firefox
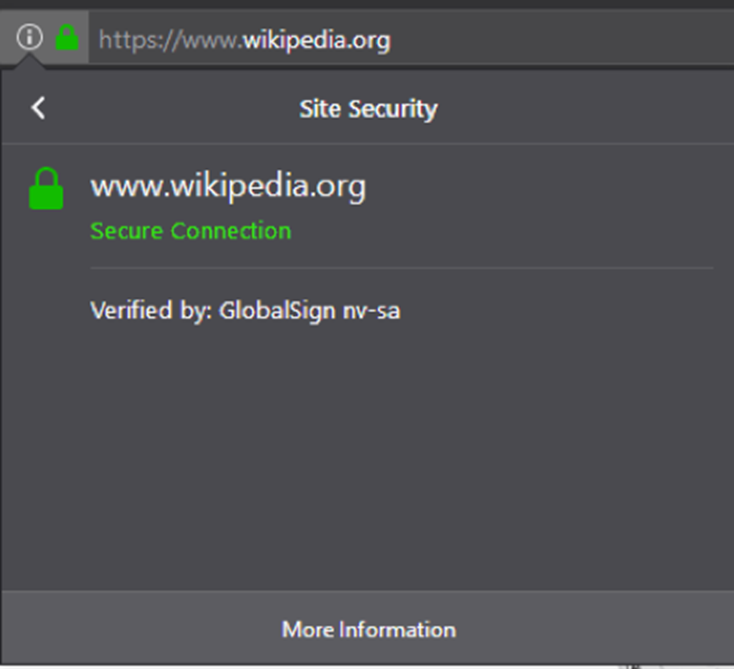
Non-EV certificate in Firefox
This takes you to the page's security details, where additional details on the website's identity are provided (for EV Certificates, the owning company's name is displayed) alongside the encryption's foundational elements, including the protocols, ciphers, and keys utilized.
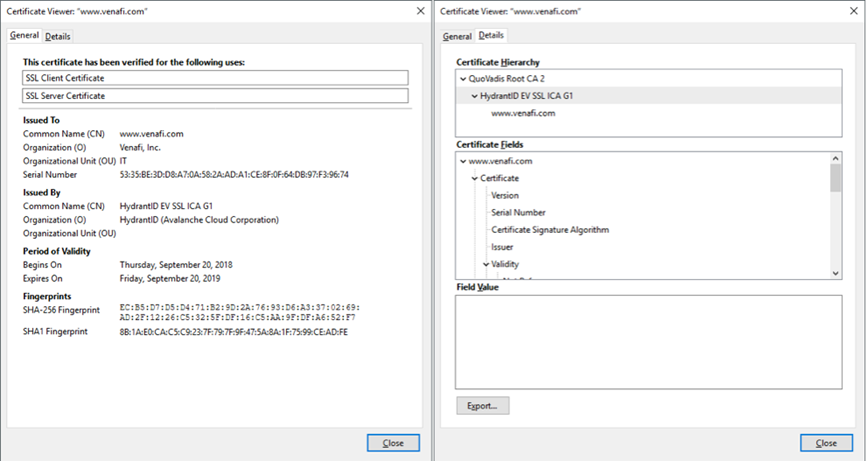
If you want even more details about the certificate, just click “View Certificate”. On the “Details” tab, you’ll find the certificate hierarchy and can dig through the certificate fields.
How do I find my SSL certificate?
Finding your SSL may be as simple as checking your dashboard or account with the Certificate Authority (CA) who issued the certificate. But if that is not an option, or your company has multiple certificates, there are two methods to locate the installed SSL certificates on a website you own.
There are two ways to locate the installed SSL certificates on a website owned by the reader of this post. Before we go into specifics, we must remember that in the Windows Server environment, the installed certificates are stored in Certificate Stores, which are containers that hold one or more certificates. These containers are
- Personal: Contains certificates tied to private keys that are accessible to the user.
- Trusted Root Certification Authorities: Encompasses all certificates found in the Third-Party Root Certification Authorities store, along with root certificates from Microsoft and customer organizations.
- Intermediate Certification Authorities: Holds certificates granted to subordinate CAs.
One great way to make sure you found all your certificates is to use Venafi as a Service. This software-as-a-service solution will scan your network and find any certificates that are installed there and give you tons of information on each one.
If you decide to go the manual route, to examine the stores on your local device to find an appropriate certificate you should follow the procedure below.
- First, you will have to use the Microsoft Management Console (MMC). To do that, open the Command Prompt, type mmc and press Enter.
- Click the File menu and then select Add/Remove Snap-in.
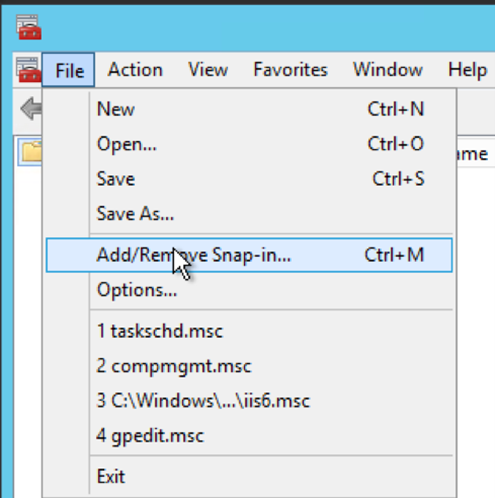
- From the Available snap-ins list, choose Certificates, then select Add.

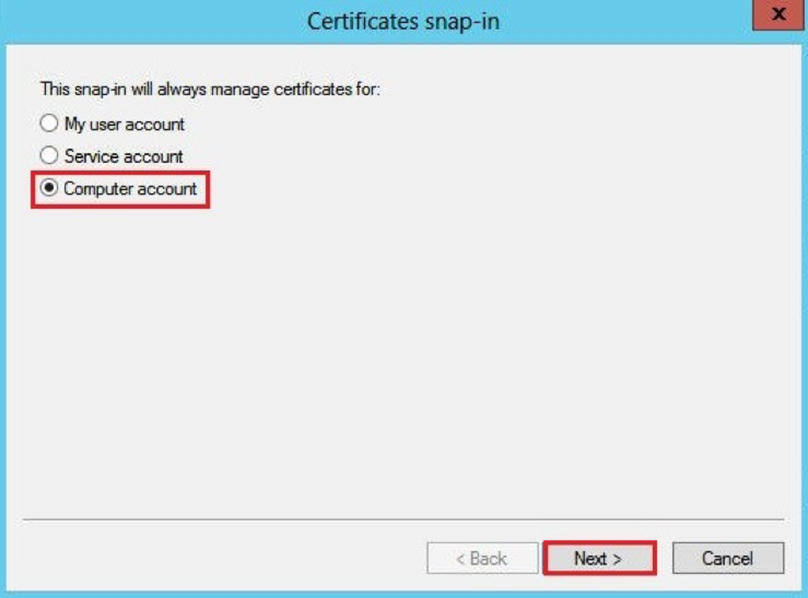
- In the next dialog box, select Computer account and click Next.
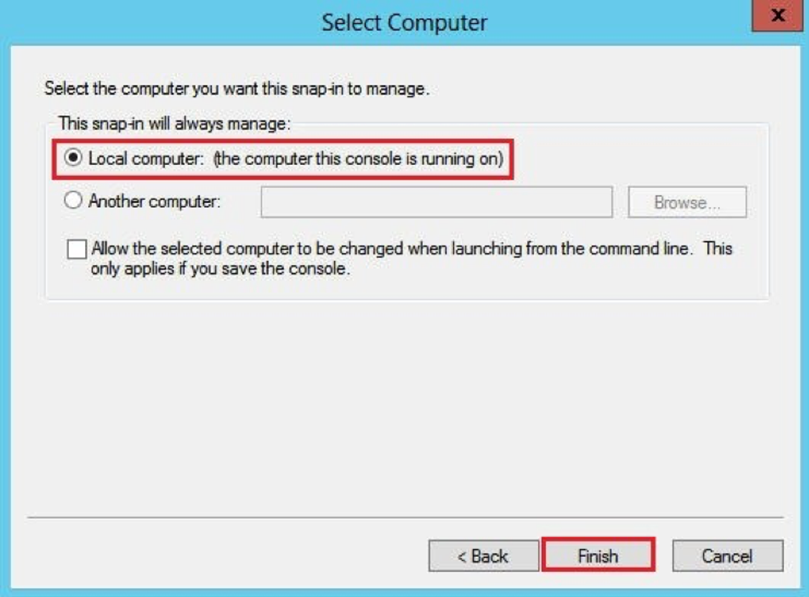
- Select Local computer and click Finish.
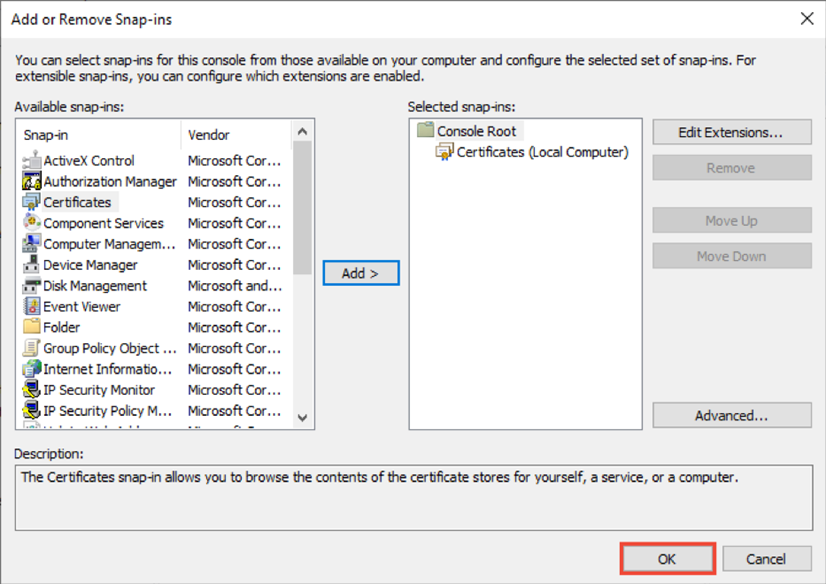
- Now you are back at the “Add or Remove Snap-ins” window, just click OK.
- To view your certificates in the MMC snap-in, select a certificates store on the left pane. The available certificates are displayed on the middle pane.
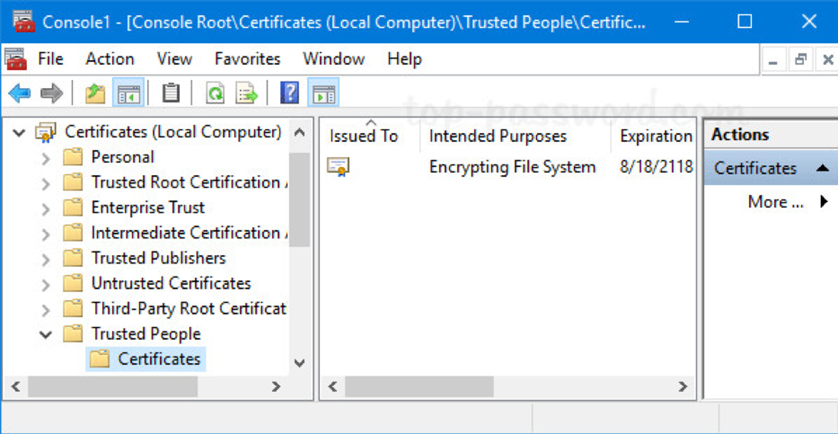
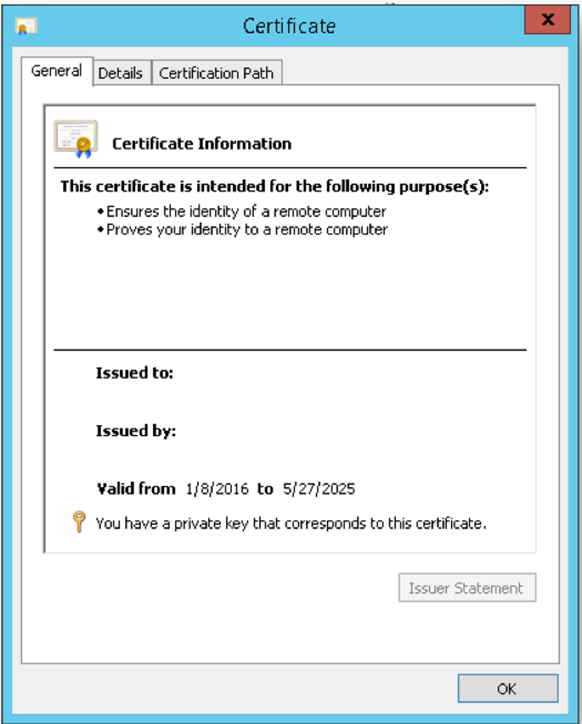
- If you double click on a certificate, the Certificate window appears which displays the various attributes of the selected certificate.
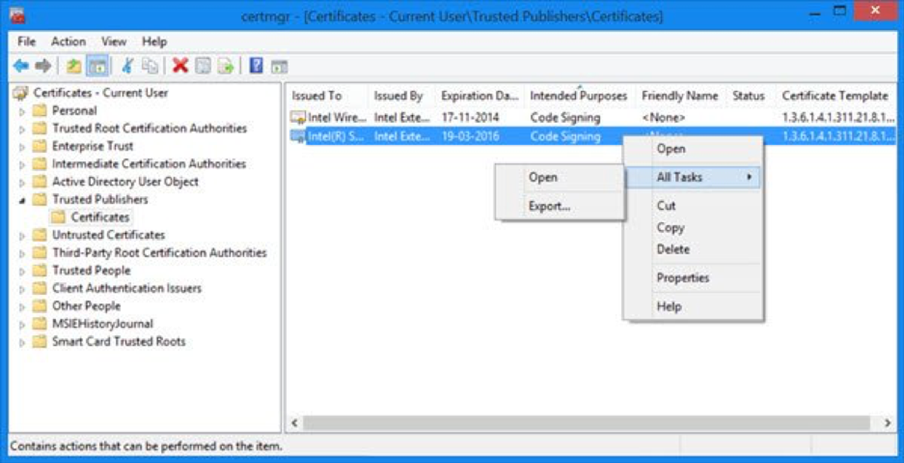
Certificate Manager Tool
Another method to view the installed certificates is to launch the Windows Certificate Manager Tool.
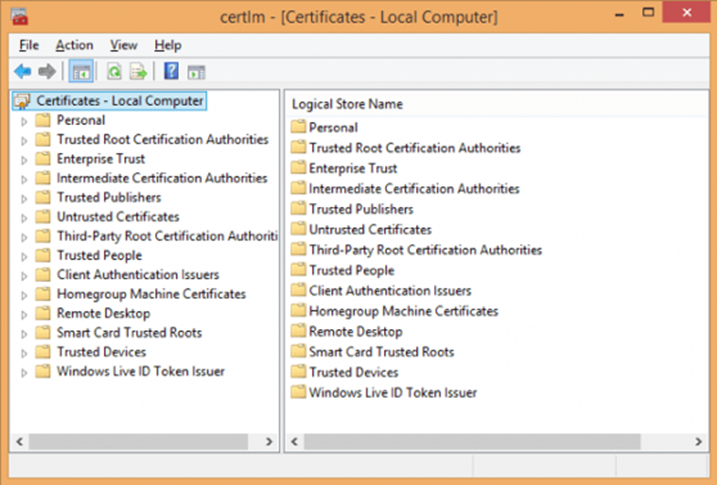
To view certificates for the local device, open the command console and then type certlm.msc. The Certificate Manager tool for the local device appears. To view your certificates, under Certificates - Local Computer in the left pane, expand the directory for the type of certificate you want to view.
To view certificates for the current user, open the command console, and then type certmgr.msc. The Certificate Manager tool for the current user appears. To view your certificates, under Certificates - Current User in the left pane, expand the directory for the type of certificate you want to view.
How do I check if my SSL certificate is valid?
Every digital certificate is subject to expiration, after which it is no longer valid. The validity period for these certificates can vary, typically ranging from one to three years, influenced by organizational policies or cost factors. At a minimum, replacing certificates upon their expiration is necessary to prevent service disruptions and maintain security levels. Nevertheless, there could be instances where an earlier replacement of certificates is needed, such as the discovery of vulnerabilities like the Heartbleed bug, transitions away from SHA-1, corporate mergers, or alterations in company guidelines.
To check the validity of your SSL certificate, several tools are available. However, with the appropriate knowledge, you can perform this verification on your own. After identifying the SSL certificates on your web server, you have two primary methods to verify their current validity.
How do you check SSL Certificates in Windows?
To check SSL certificate validity in Windows, there are two methods. The first method involves executing the certlm.msc command to access the Certificates - Local Computer interface, where you'll sift through the store's list of certificates to confirm that only those that are legitimate are installed. Although this task can take a lot of time, it is achievable.
The second method entails using a tool from Windows Sysinternals named sigcheck, which simplifies the task of checking Root Certificates significantly. Acquire or update this utility from Microsoft and initiate it using the command: sigcheck -tv. This process involves the utility retrieving the trusted root certificate list from Microsoft and then displaying only those valid certificates that aren't linked to any certificate within that list.
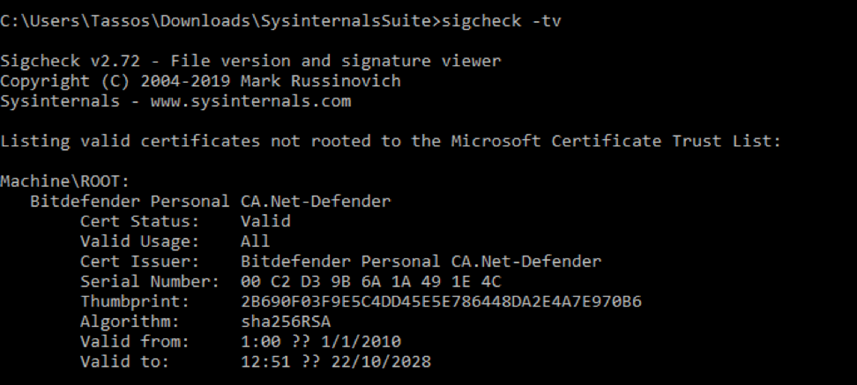
Checking SSL validation and managing certificates can be a very difficult and error-prone process. There are many critical tasks that come with enterprise SSL certificate management and ignoring or mishandling any one of them can set the stage for a Web application exploit.
How do you install SSL certificates?
The process for installing an SSL certificate depends on the provider that you purchased it from. Some providers will streamline installation or take care of it for you. If you need to install the certificate manually, the steps are dependent upon your platform and operating system.
How do you renew SSL Certificates?
SSL renewal keeps your encryption and ciphers up to date, keeping your website and customers safer. Keep on top of renewals to avoid the mistake of letting your certificates expire.
There are two different procedures to follow, which depends on whether you are renewing self-signed certificates or certificates from CAs.
How do you create a new Self-Signed Certificate?
While self-signed certificates are not recommended for use on e-commerce platforms or any sites handling sensitive data like credit card or social security numbers, they might be suitable for specific contexts such as intranets, development servers for IIS, or personal websites with minimal traffic.
- Access the Start menu, navigate to Administrative Tools, and select Internet Information Services (IIS) Manager.
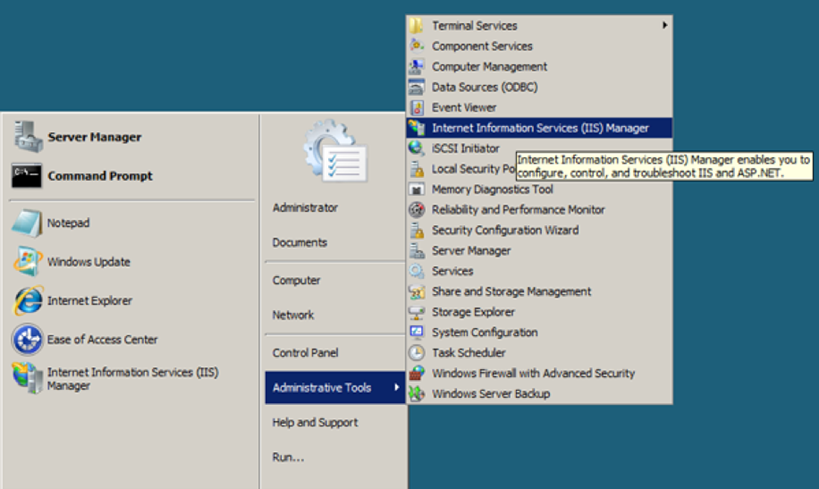
- Click your server's name in the Connections pane on the left. Then, double-click Server Certificates.
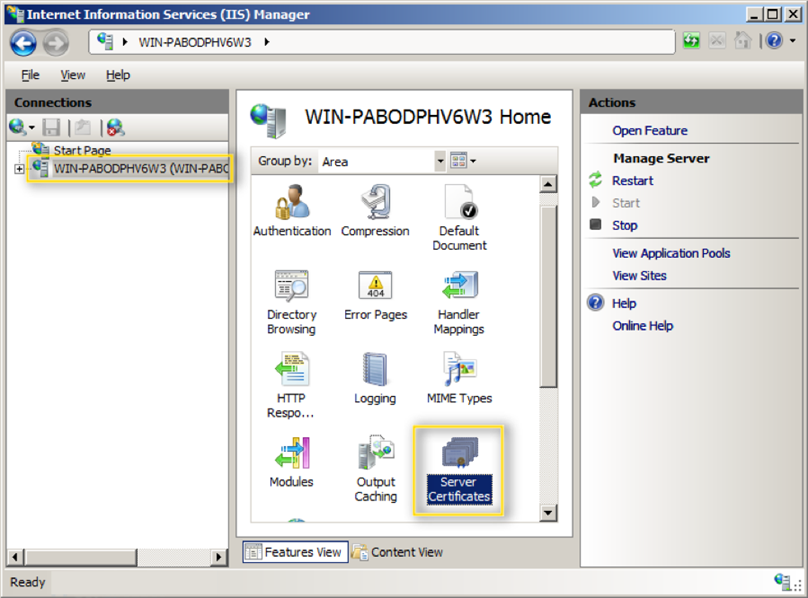
- In the Actions pane on the right, select Create Self-Signed Certificate…
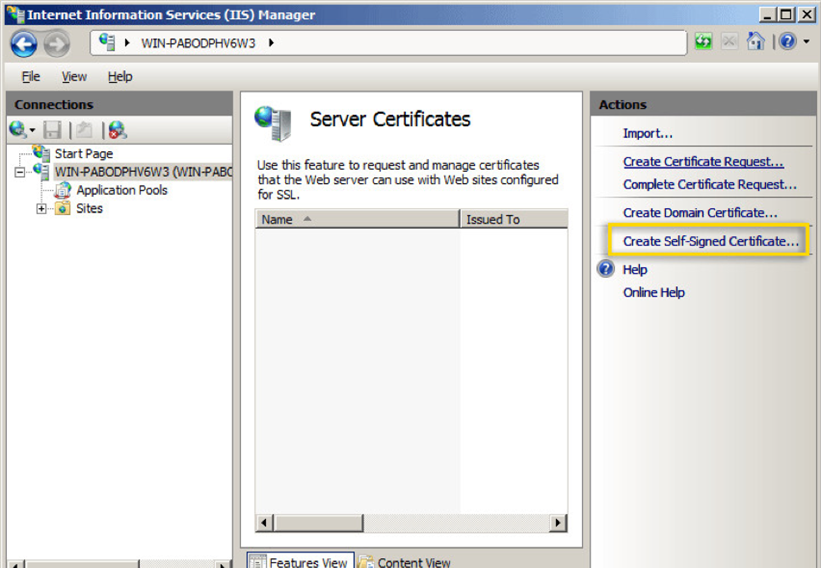
- Input a friendly name for your certificate and click OK.
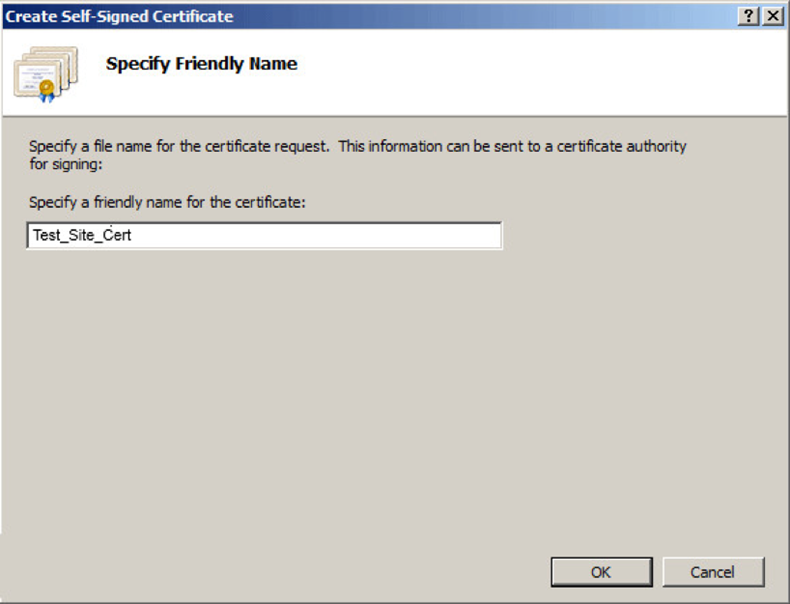
- You've now generated a self-signed certificate, which is valid for one year and appears in the Server Certificates list. By default, the certificate's common name is the server's name. The next step is to link this certificate with your website.
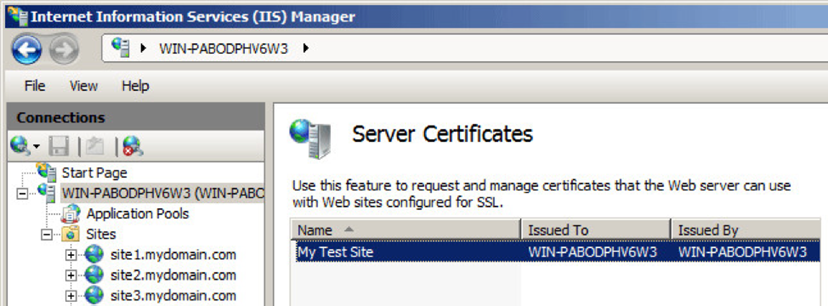
- To assign this certificate to a website, in the Connections pane, unfold the sites directory and choose the site you wish to secure. Select Bindings... from the Actions pane.
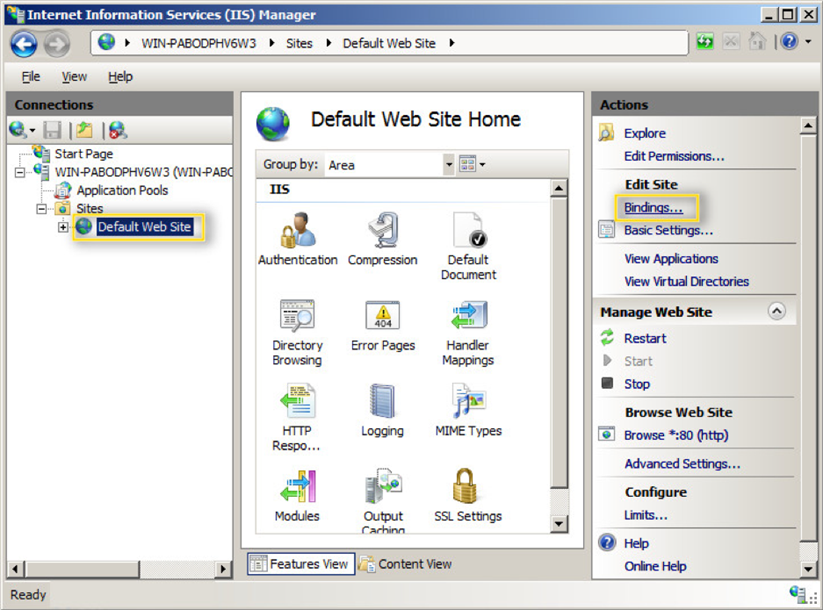
- In the Site Bindings window, hit the Add... button.
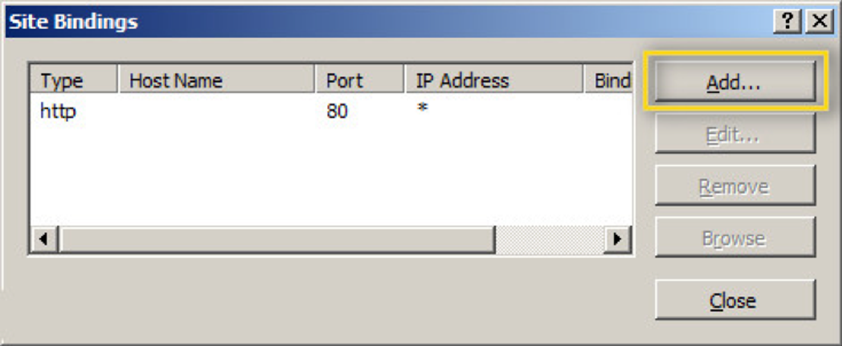
- Change the Type to https, pick the newly installed SSL certificate, and press OK.
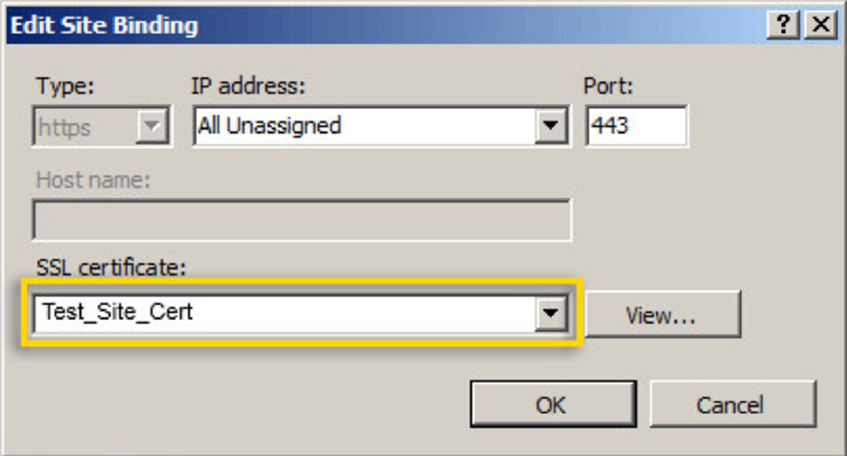
- The port 443 binding should now be visible. Click Close.
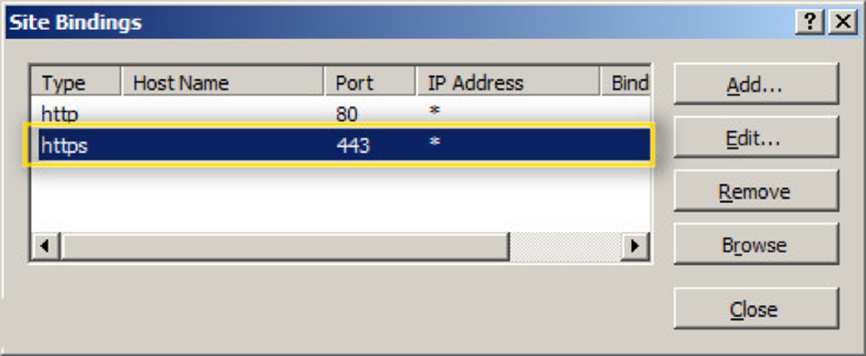
To finalize, adding your self-signed certificate to the Trusted Root Certification Authorities is advisable. Open the Microsoft Management Console (MMC) and set up a Certificate snap-in for the Local Computer account.
- Within the console, expand the Certificates section, then the Personal folder. Navigate to your self-signed certificate, right-click it, and choose Copy.
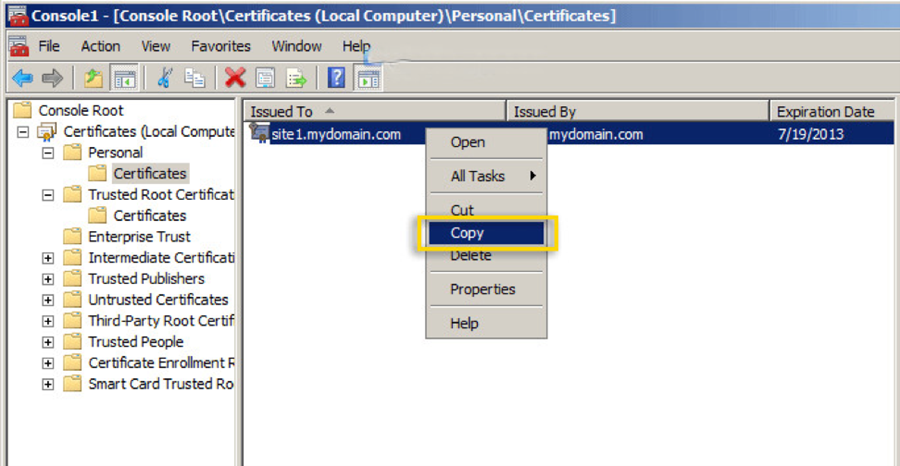
- Go to the Trusted Root Certification Authorities, click on the Certificates folder beneath it, right-click in the empty space among the listed certificates, and select Paste.
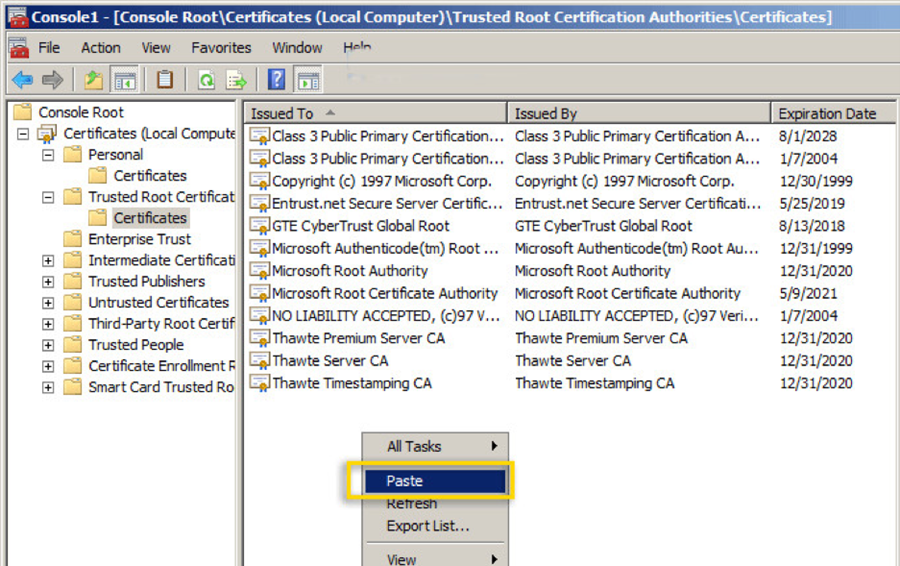
How do you renew the root certificates from your CAs?
- Within the Microsoft Management Console (MMC) on your server, initiate the Certification Authority snap-in. Right-click the Certificate Authority's name and choose All Tasks > Renew CA Certificate from the action menu.
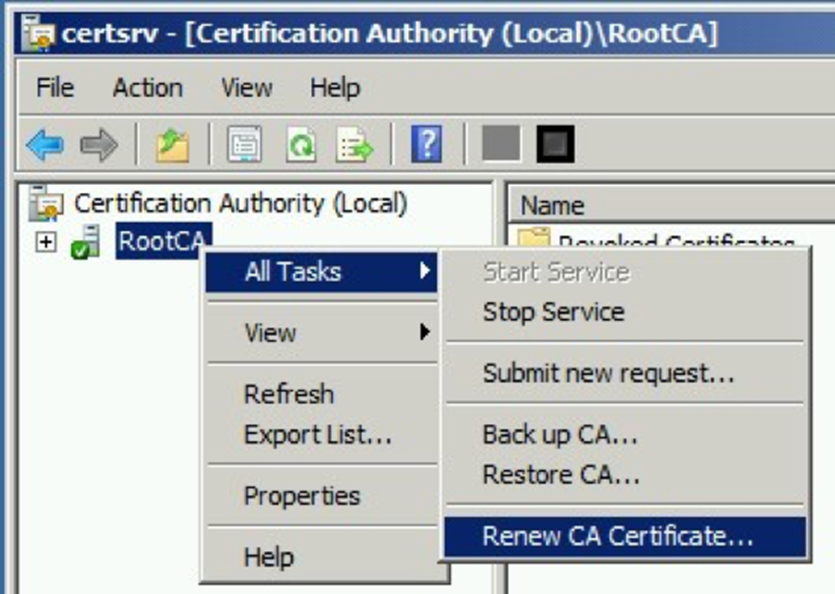
- A warning dialog, Install CA Certificate, appears to notify you that the Active Directory Certificate Services must be halted. Click Yes to proceed.
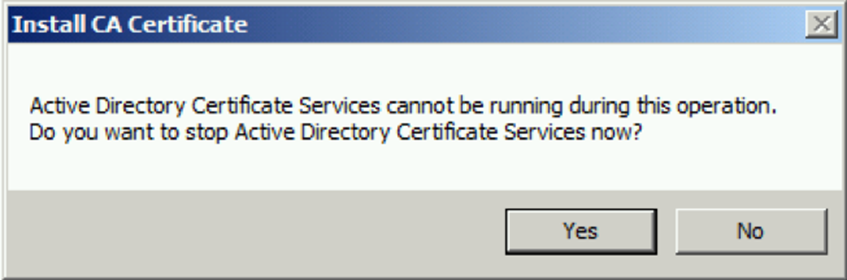
- In the Renew CA Certificate dialog, you're presented with the choice to either continue using the existing CA key pair or to generate a new key pair for the certificate's renewal. Opting to create a new public and private key pair for the CA's certificate requires selecting Yes, although the default selection is to retain the current key pair. For most scenarios, it's recommended to choose No.

- Selecting to generate a new key pair prompts Windows to create it during the new CA certificate's issuance. This ensures the key signing the CA's issued certificates aligns with the key signing the Certificate Revocation Lists (CRLs). Renewing the CA certificate with a new key pair can also address issues related to oversized CRLs, as the new CRL will only include serial numbers of certificates revoked since the new CA certificate's inception date.
- Following these steps, your certificate will be successfully renewed.
Do SSL certificates expire?
SSL certificates are hardcoded with expiration dates, typically up to two years. This provides greater protection and ensures your encryption is up to date. You can renew your SSL certificate up to 90 days before the expiration date, which gives you time to get your new certificate issued and installed and avoid a lapse in encryption.
It’s important to monitor your certificates and stay on top of expirations that may sneak up on you, which can cause outages that will hurt your site. Unfortunately, many companies manage a variety of digital certificates manually with spreadsheets. This can lead to mistakes, such as lost, mismatched, or mislabeled certificates. Certificates can inadvertently expire, meaning CAs no longer consider a website or web application secure and trusted. This can be a very expensive mistake if an affected Web application is public-facing. It may lead to reputational damage for the organization, or visitors' browsers may block access to the site entirely. It's been the cause of many high-profile system outages and is often one of the last causes administrators investigate, contributing to significantly more downtime.
Another problem occurs if the CA that issued the organization's certificate is compromised. The certificates are then revoked by other CAs, so when a client connects to the affected server, the certificate is no longer valid. Without proper SSL certificate management on an enterprise-wide level, it's impossible to tell how many (if any) of your certificates are no longer valid.
To avoid these certificate management errors and to correct any mistakes that previously occurred while managing certificates, the most effective solution is to use automation. Automated tools can search a network and record all discovered certificates. Such tools can usually assign certificates to business owners and can manage automated renewal of certificates. The software can also check that the certificate was deployed correctly to avoid mistakenly using an old certificate.
How do I remove expired digital certificates?
It is very important to highlight the importance of having valid certificates. Expired certificates can and will cause website outages and downtime which in turn will create serious reputational damage. It is therefore highly advisable to renew in a timely manner the certificates close to expiring. Do not wait until the very last moment to do so.
Once you have found all your certificates on your system, you might have discovered that some have already expired (hopefully not!). To remove expired certificates, either self-signed or provided by a CA, there are two methods.
First method: Right-click on the expired certificate and select Delete. You will have to repeat this step for all expired certificates. Once you are done, you will have to restart the server.
Second method: Right-click on the expired certificate and choose Properties. On the Properties window, select “Disable all purposes for this certificate” and then click Apply. Once you are done with all your expired certificates, you will have to restart the server.
What are the benefits of SSL certificate automation?
The importance of SSL security cannot be overstated in an organization's comprehensive security plan. As the quantity of devices connected to the internet, along with online platforms and services, expands, so do the potential entry points for security vulnerabilities and the spectrum of threats these infrastructures are exposed to.
In the current digital landscape, organizations are mandated to employ SSL certificates to safeguard data transfers across sites and internal networks. Consequently, system administrators find themselves overseeing a multitude of certificates, each with its distinct expiry date, making the task of certificate management both challenging and unwieldy.
For system administrators, the necessity of a unified platform for the setup, deployment, observation, and complete management of SSL certificates across their networks has become critical, regardless of the Certificate Authority (CA) that issued them. Lack of a comprehensive approach to managing the lifecycle of certificates can lead to gaps in both security and management within organizations.
Effective certificate lifecycle management requires the aggregation of all certificates into a unified management system, such as the Venafi Control Plane or TLS Protect Cloud. By implementing these platforms, administrators are empowered to conduct ongoing surveillance of both systems and certificates and produce audits for governance and compliance objectives. Additionally, this method simplifies the management of SSL certificates within a widespread network environment, significantly reducing both cost and complexity.
Should you find the process of checking SSL certificates overwhelming and wish to learn the advantages of automated certificate lifecycle management, contact Venafi for a tailor-made solution.