Organizations need machine identity management to oversee and secure the way their machines—which can be anything from physical servers to cloud instances and containers—connect and communicate with one another. Unlike human identities, which use usernames and passwords or biometric devices, machine identities use cryptographic methods to identify themselves. While there are two types of encryption methods, symmetric and asymmetric, this article focuses on asymmetric encryption, also known as public key encryption, used in public key infrastructure (PKI).
How does public key encryption work?
Public key encryption operates using a pair of cryptographic keys: a public key and a private key, which work together in an encryption algorithm. This method is pivotal in securing data transmitted over the internet. Here's how it works: the public key encrypts plaintext data, rendering it unreadable. Only the corresponding private key, which is kept secret, can decrypt this data back into its original form. The strength of public key encryption lies in its security; as long as the private key is not compromised, the encrypted data remains secure. This ensures that only the intended recipient, who possesses the private key, can access the information.

TLS Machine Identity Management for Dummies
Public Key Encryption Example
Public key encryption can be explained by the simple, well-known Alice and Bob example, provided by Ron Rivest, Adi Shamir, and Leonard Adleman in their 1978 paper, A Method for Obtaining Digital Signatures and Public-Key Cryptosystems. In August 2013, Panayotis Vryonis expanded the encryption example. In the examples, Alice and Bob are two users of a public-key cryptosystem. They use a trunk to exchange messages. The trunk has a lock that only Alice and Bob can access and two keys, a public key and a private key, referred to as a public-private key pair. While a typical lock only has two positions, locked and unlocked, the lock for public key cryptography has the following three positions.
Locks on the left (position A)
Unlocks in the middle (position B)
Locks on the right (position C)
As for the two keys, the first one can only turn clockwise (from A to B to C) and the second one can only turn counterclockwise (from C to B to A). One key can only turn to the left side, while the other key can only turn to the right side. Both keys can lock the trunk, which includes the message, but the key that was used to lock the trunk (key #1) is not used to unlock it. Only the other key (key #2) of the public-private key pair can unlock it. For this example, the trunk represents the plaintext data that is scrambled during the process of encryption.
In the example, Alice shares her public key with family, friends and colleagues. She keeps her private key, which turns clockwise from A to B to C, a secret. Everyone who has her public key can turn the key counterclockwise from C to B to A.
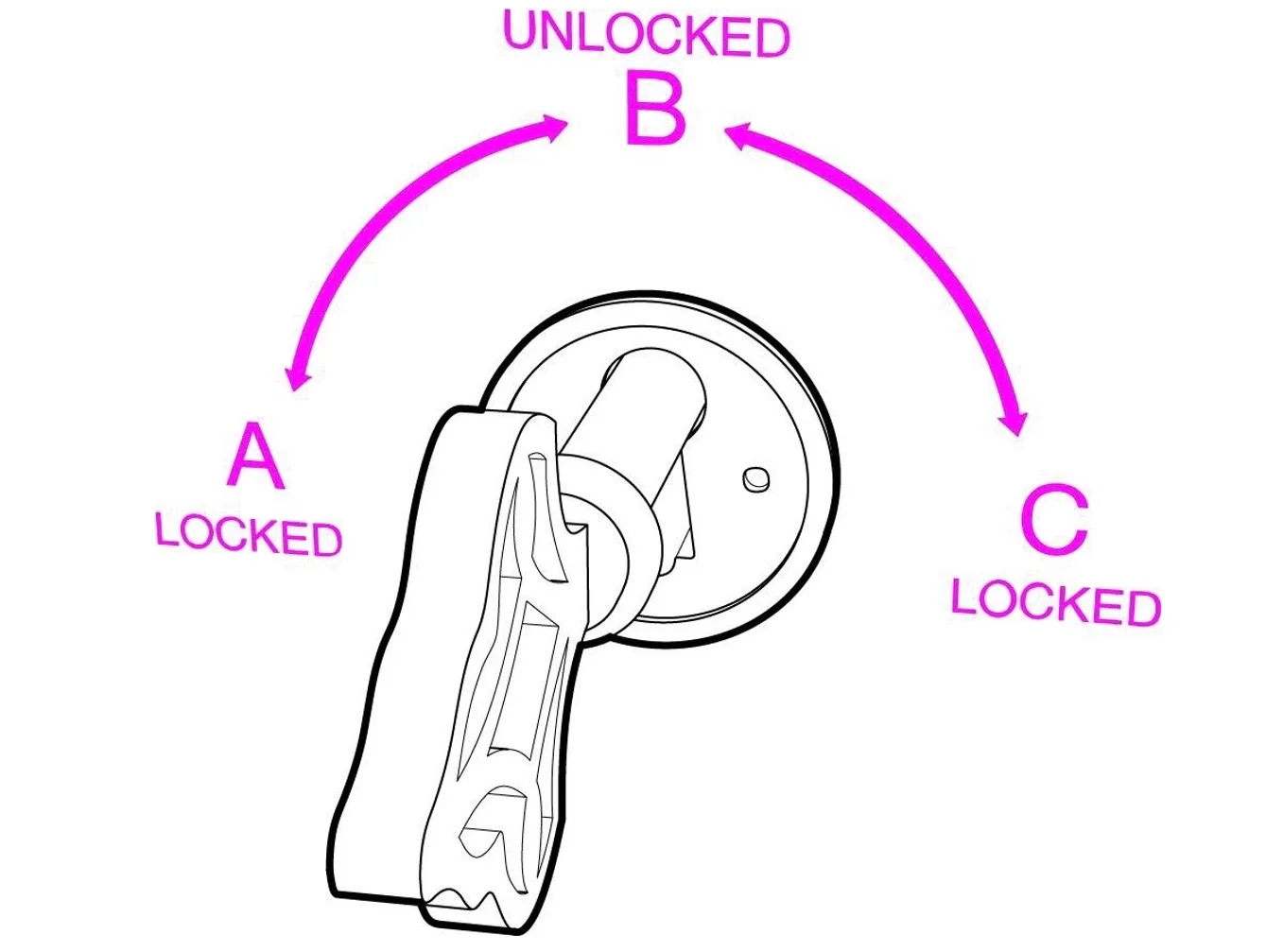
Figure 1: Public Key Encryption explained. Image courtesy of Panayotis Vryonis
If Bob wants to send Alice a sensitive document, he places the document in the trunk, and uses a copy of Alice’s public key to lock it. Remember, her public key only turns counterclockwise, so Bob will turn the key counterclockwise from C to B to A to lock the trunk. The only key that can turn from A to B is Alice’s private key, which she has kept a secret. Alice can unlock the trunk with her private key and read the sensitive document.
The primary takeaway for how public key encryption works is that data encrypted using the public key requires the corresponding private key for decryption, and conversely, data encrypted with the private key can only be decrypted using the public key.
Public key encryption and secure web browsing
Public key encryption is also important for Secure Sockets Layer (SSL) and Transport Layer Security (TLS), which is used to accomplish hypertext transfer protocol secure HTTPS web browsing. TLS, which replaced SSL, is an encryption protocol that includes a number of steps that occur between the web client and server. It is referred to as the TLS Handshake. One of the things that happens during the handshake is identity authentication of the server, which is via the server’s public key and the certificate authority’s digital signature. This confirms that the server is what it claims to be and that the client is communicating with the true owner of the domain. The server also uses the public key to create a pre-master key in order to facilitate the key exchange, which is necessary to generate the master key for the remaining communication between the client and the server.
Benefits of public key encryption
Public key encryption supports authentication
The public-private key pair can be used to verify the identity of users and machines using digital certificates. Digital certificates are similar to an ID, such as a driver’s license or a passport. They uniquely identify a user or machine in the same way a passport identifies an individual. When a user digitally signs a communication with their private key, and transmits the communication to the recipient, the recipient wants to have confidence and trust that the key really belongs to the sender and not a bad actor. Digital certificates provide the confidence that the sender is a trusted source.
One drawback to asymmetric encryption is that encryption algorithms require significant computing power, which slows down the encryption process. Due to its slower speed, it is not suitable for long computing sessions.
Public key encryption is secure—as long as the private key is protected
The primary security benefit of using public key encryption is that regardless of how widely distributed public keys are, the risk of data being compromised is mitigated by the fact that a malicious actor will need the private, secret key to decrypt the message and view the data. The public-private key pair has a mathematical relationship, which means that the data encrypted with a public key can only be decrypted with the corresponding private key. The public key cannot be used to decrypt the ciphertext. Confidentiality, integrity and non-repudiation are security services that are provided when using the public key pair.
But the moment the private key is no longer a secret, the security of the encrypted data is compromised—which is why robust machine identity management policies and procedures must be enforced.
Conclusion
Public key encryption has several uses and benefits. But if the private, secret key of the public-private key pair is not securely managed, public key encryption is ineffective. Poorly distributed or mismanaged private keys may fall into the hands of a bad actor and lead to an unintended recipient decrypting the message.
Organizations must secure their private keys by using best practices for secure key generation and storage. Investing in key management technology that automates the complete lifecycle of private keys, including creation, rotation, deletion, auditing and API integration support is recommended. Using a manual key-management process leaves valuable data completely compromised and subject to theft.
