Computer encryption, which relies on encryption protocols derived from the science of cryptography, has been pivotal in keeping information confidential. These protocols have evolved significantly since the times humans first desired to conceal their messages. Before the digital age, cryptography was chiefly employed by governments, especially for military communications. The rich history of encryption stretches back to the ancient Greeks and Romans, who sent secret messages using substitution ciphers that could only be decoded with a secret key.
Encryption Protocols: A Brief History
In ancient Greece, a device known as a Scytale was employed for quicker encryption using a transposition cipher. The Greeks would wrap a strip of parchment around a cylinder, inscribe their message, and then unwind it, rendering the text incomprehensible. While this method of encryption was relatively simple and could be deciphered with some ease, it stands as one of the earliest instances of practical encryption. Similarly, Julius Caesar adopted an encryption technique, now known as Caesar’s cipher, during his reign. This method involved shifting each letter in a message a certain number of positions left or right in the alphabet. Since only the intended recipient knew the specific shift used, it posed a challenge for unauthorized decoders.
During World War II, the German military used the Enigma machine for encrypted communications on the battlefield. The Allied forces spent years attempting to decrypt these transmissions, and their eventual success played a crucial role in their victory.
Encryption Protocols Today and How They Work
Most forms of cryptography in use nowadays rely on computers, simply because a human-based code is too easy for a computer to crack. Cryptosystems utilize a collection of processes known as cryptographic algorithms, or ciphers, which are essential for encrypting and decrypting messages, thereby securing communications across computer systems, devices like smartphones, and various applications. A cipher suite typically employs distinct algorithms: one for encryption, another for message authentication, and a separate one for key exchange. Embedded within protocols and software that operate on both operating systems and networked computer systems, this process encompasses the generation of public and private keys for data encryption and decryption, the use of digital signatures and verification for message authentication, as well as the key exchange mechanism.
Computer encryption systems generally belong in one of two categories: symmetric-key encryption and public-key encryption.

PKI: Are You Doing It Wrong?
Encryption System 1: Symmetric Keys
Like the ancient commanders encrypting their correspondence, computers today employ symmetric-key encryption, necessitating a unified key for secure communication. Each machine harbors a clandestine key, a unique code used to cloak a bundle of data before it traverses the network to its counterpart. This method mandates a prearranged setup, with the shared key deployed on all involved computers. Symmetric-key encryption is akin to an exclusive cipher—both sender and receiver must possess the key to unveil the data's true meaning. This mirrors the encryption you use in your home WiFi network, where a single password grants entry to both your router and laptop.
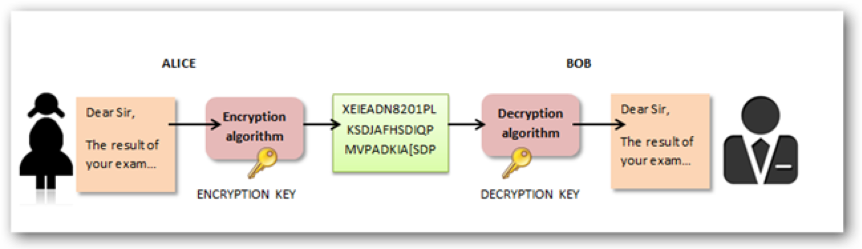
In symmetric-key encryption, there are two primary classifications: stream ciphers and block ciphers. Stream ciphers operate by sequentially encrypting each bit of the message, processing them one after another. On the other hand, block ciphers approach encryption differently, handling groups of bits, commonly in 64-bit blocks, and encrypting them collectively as a whole. Today's cryptographic practices mainly utilize block ciphers, with stream ciphers being less commonly employed.
The first significant symmetric encryption algorithm developed for computers in the United States was the Data Encryption Standard (DES), which gained approval in the 1970s. DES utilizes a 56-bit key. However, with the substantial increase in computer processing speed since the '70s, DES is no longer considered secure; it is vulnerable to brute force attacks that can decrypt data relatively quickly. Consequently, DES has been succeeded by the Advanced Encryption Standard (AES), which employs keys of 128, 192, or 256 bits, offering enhanced security.
Encryption System 2: Public-key Encryption
Establishing a secure connection to a website over the public internet presents a unique challenge, as relying solely on symmetric encryption is not feasible due to lack of control over the connection's other end. The critical question arises: how can two parties safely exchange a secret key over the internet without it being intercepted? This conundrum was addressed in a seminal paper by Diffie and Hellman, titled “New Directions in Cryptography,” published in the “IEEE Transactions on Information Theory” in November 1976. Their innovative solution laid the foundation for public-key encryption.
Public-key cryptography, also recognized as asymmetric-key encryption, is a secure method used to maintain the privacy, authenticity, and irrefutability of digital communications and data storage. It operates using a dual-key system, involving both a private and a public key. The private key is kept secret by the individual it belongs to, while the public key is disseminated widely, often via a repository that is accessible to the public. For a computer to successfully decrypt a message, it must employ the public key provided by the message sender, along with its own private key.
Although messages sent from one computer to another using public-key encryption are encrypted with a key that is publicly available, these messages remain secure. This is because, despite the public accessibility of the encryption key, the message cannot be decrypted without the corresponding private key. The security of this system is further reinforced by its foundation on long-length prime numbers, offering an extremely high level of security. The near-infinite number of prime numbers available translates to an almost limitless array of possible key combinations, greatly enhancing the system's security.
Typically, both the public and private keys are generated simultaneously through the same mathematical procedure, establishing a strong mathematical correlation between them. This intrinsic relationship allows them to encrypt and decrypt the same data. As a result, public and private keys from different pairs are incompatible with each other. Each web server possesses its distinct set of keys, ensuring that your connection to a particular website is unique and distinct from others.
However, this encryption process is unidirectional. If data is encrypted with one key, be it public or private, only its counterpart can decrypt it. This means that even if the public key is widely accessible, it becomes irrelevant once the data is encrypted, as decryption is only possible with the corresponding private key, securely stored on the web server.
Public key algorithms are essential components in the architecture of cryptosystems, applications, and security protocols. They form the basis of several Internet standards, including Transport Layer Security (TLS). Different public key algorithms serve varied purposes: while some, like the Diffie–Hellman key exchange, are designed for key distribution and maintaining confidentiality, others, such as the Digital Signature Algorithm, are used for creating digital signatures. There are also algorithms like RSA that offer both functionalities.
Public Key Infrastructure and Encryption
Public Key Infrastructure (PKI) represents the foundation of encryption and cybersecurity, safeguarding communications between a server (such as your website) and its clients (the users). The effectiveness of PKI hinges on the use of digital certificates. A digital certificate serves as an electronic form of identification for websites and organizations. Secure connections between two communicating devices are facilitated by Public Key Infrastructure (PKI), which allows for the verification of the identities of both parties through the use of these certificates.PKI functions on asymmetric key methodology; a private key and a public key. The private key can only be accessed by the owner of a digital certificate, and they can choose where the public key goes. A certificate is essentially a way of handing out that public key to the owner who wants to have it.
When encrypting a substantial volume of data, employing a combination of both encryption protocols can be advantageous. Initially, asymmetric encryption is utilized to establish a secure connection. Once this connection is in place, symmetric encryption takes over, maintaining the session's security for its duration. Let's delve into the details of how this process functions:
Your browser initiates a connection to the website's server, which responds by sending its public key, while its private key remains confidential. Subsequently, your browser creates a unique key, known as the session key. This key is encrypted on your computer using the server's public key. Once encrypted, the session key is sent to the server. The server then uses its private key to decrypt the session key received from your browser. At this point, both your computer and the server possess the same session key, initially generated by your computer. With this exchange, the use of public key encryption comes to an end, and symmetric encryption takes over. The ongoing session with the server proceeds using symmetric encryption exclusively, and this setup persists until you disconnect from the website.
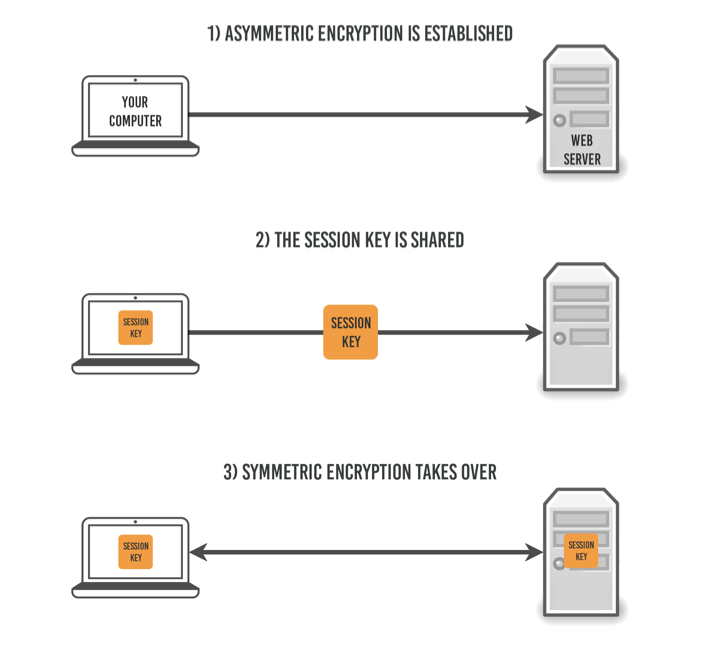
Public key, or asymmetric, encryption is employed only momentarily at the start of the connection to exchange a third key, which then facilitates the remainder of the session. This brief use is due to the intricate mathematical computations that asymmetric encryption entails, necessitating significantly more computational resources to maintain.. It is not suitable for long sessions because of the processing power it takes to keep it going.
What is the Most Secure Form of Encryption?
The algorithm trusted by the United States Government, Advanced Encryption Standard (AES), uses symmetric key encryption to cipher and decipher information. Widely considered impervious to all attacks, AES has a maximum key length of 256 bits and is practically unbreakable. It has become the global standard of encryption, and is what’s used to keep most of our interpersonal communications secure.
How Safe is Encryption?
Nothing in the world of cybersecurity can be 100% guaranteed, and varying levels of the encryption’s mathematical design properties and secure implementation will definitely impact its effectiveness. But in the case of well-designed AES that has been implemented to best practice, the odds of current computing technologies cracking the complexity of AES is highly unlikely.
The biggest potential threats to the current standards of encryption are actually found in two new cryptology developments. The first is the increased migration from on-premises storage to cloud environments, which presents a dilemma around cloud storage. Allowing cloud storage to be easily searchable makes it highly vulnerable to attack, but certain encryptions make it difficult for owners to find information when needed. The emerging solution to this problem is searchable symmetric encryption (SSE), which enables users to store documents in ciphertext form while maintaining the functionality to search keywords within their documents.
The second threat is quantum computing, a technology that has not yet even realized its full potential. All security professionals need to take the onset of quantum computing seriously, as there will soon be quantum computers capable of breaking or entirely fabricating machine identities.
Venafi and the Machine Identity Management Development Fund are bringing together the true leaders of quantum-safe computing to develop machine identities that are post-quantum-safe.
Related posts
